Today, we are introducing the GreyNoise Enterprise data integration in Maltego, offering SOC analysts, threat hunters, incident responders, and security engineers the ability to easily separate common noise, generated by Google bots, Shodan scans and Censys among others, from real attacks and malicious scans.
What is GreyNoise Enterprise? 🔗︎
GreyNoise is a cybersecurity platform that collects and analyzes Internet-wide scan and attack traffic. GreyNoise analyzes and enriches this data to identify behavior, methods, and intent, giving analysts the context they need to take action.
How Can I Start Using the GreyNoise Enterprise Transforms in Maltego? 🔗︎
In order to use GreyNoise Enterprise, you’ll need an API-Key as well as a commercial Maltego license.
Sign up for a free trial API key of GreyNoise Enterprise to try out the integration or plug in your own API key to access the full solution. Visit our GreyNoise Enterprise Hub detail page to learn more about the access options.
Visit our GreyNoise Community Hub detail page to learn more about access and free trial of the GreyNoise Community data.
What Type of Information Can I Get from GreyNoise Enterprise? 🔗︎
Analysts can begin their investigations using GreyNoise Enterprise and Maltego with an IP Address, Person, CVE (Common Vulnerabilities and Exposures), or an AS (Autonomous System) Entity. From there, investigators can run Transforms to uncover information related to:
- IP Addresses
- Organizations
- Tags
- ASs
- CVEs
- Locations
Use Case: Threat Hunting of Current Massive Scanners 🔗︎
Investigators can use GreyNoise Enterprise to identify the extent of malicious activities against an organization and determine the origin of said threats. Combining the intelligence of GreyNoise Enterprise with Maltego Standard Transforms will enable investigators to get a more comprehensive picture of ongoing activities. In this case, we are interested in learning where attacks may come from and which vulnerability is being scanned for the most.
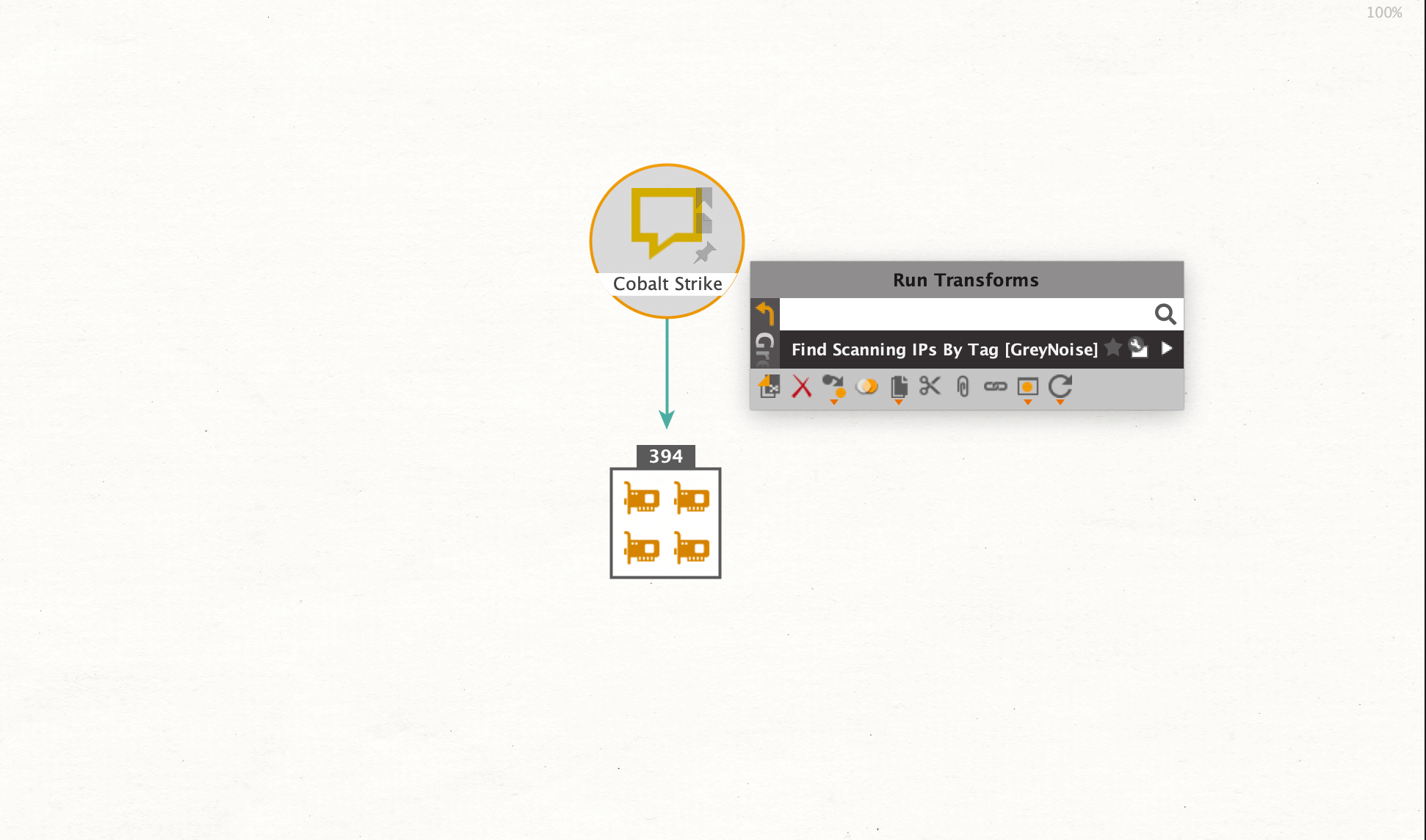
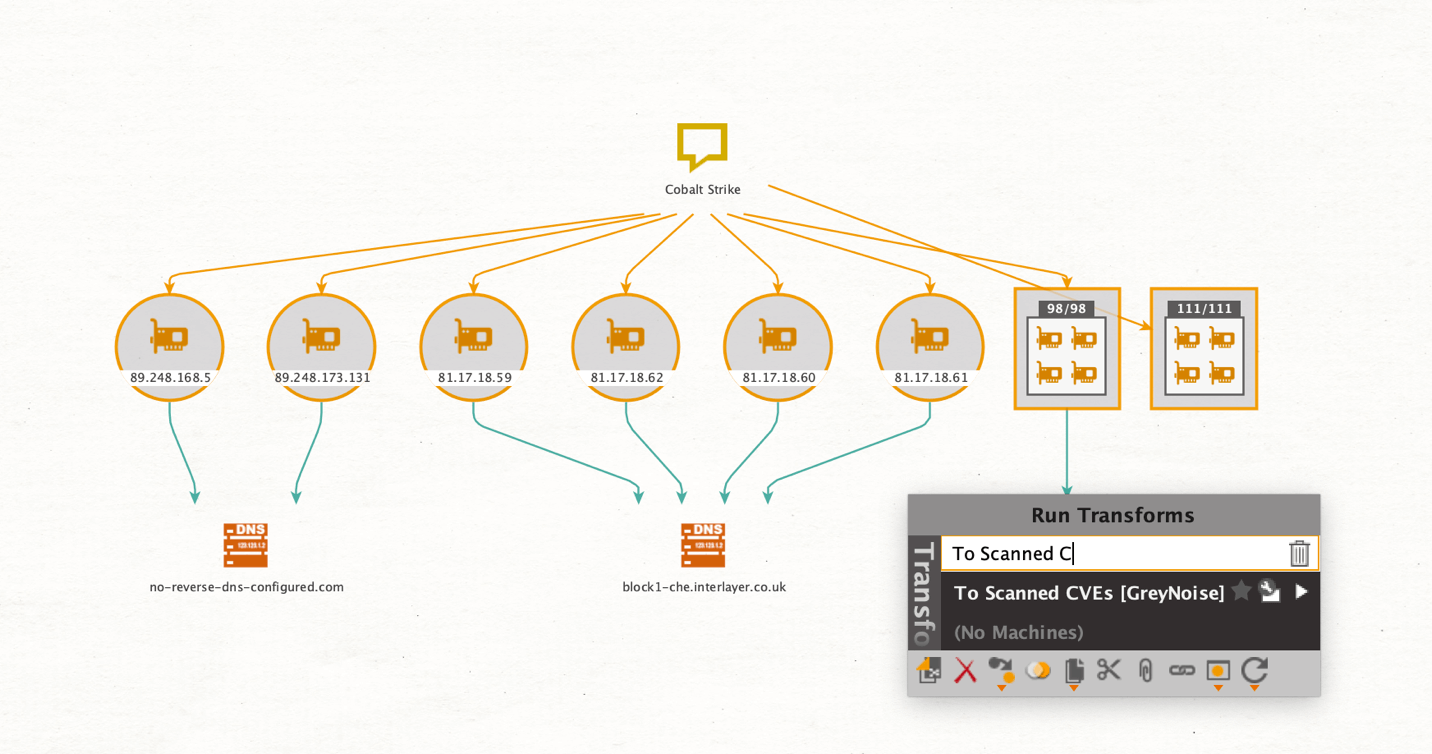
Our starting point will be a Phrase Entity with the name “Cobalt Strike”, a commercial full-featured remote access software. We want to look into IP addresses related to the software, but exclude basic scanner noise like Google or Shodan to identify systems related to active attack capabilities. To do so, we will run the Find Scanning IPs By Tag [GreyNoise] Transform.
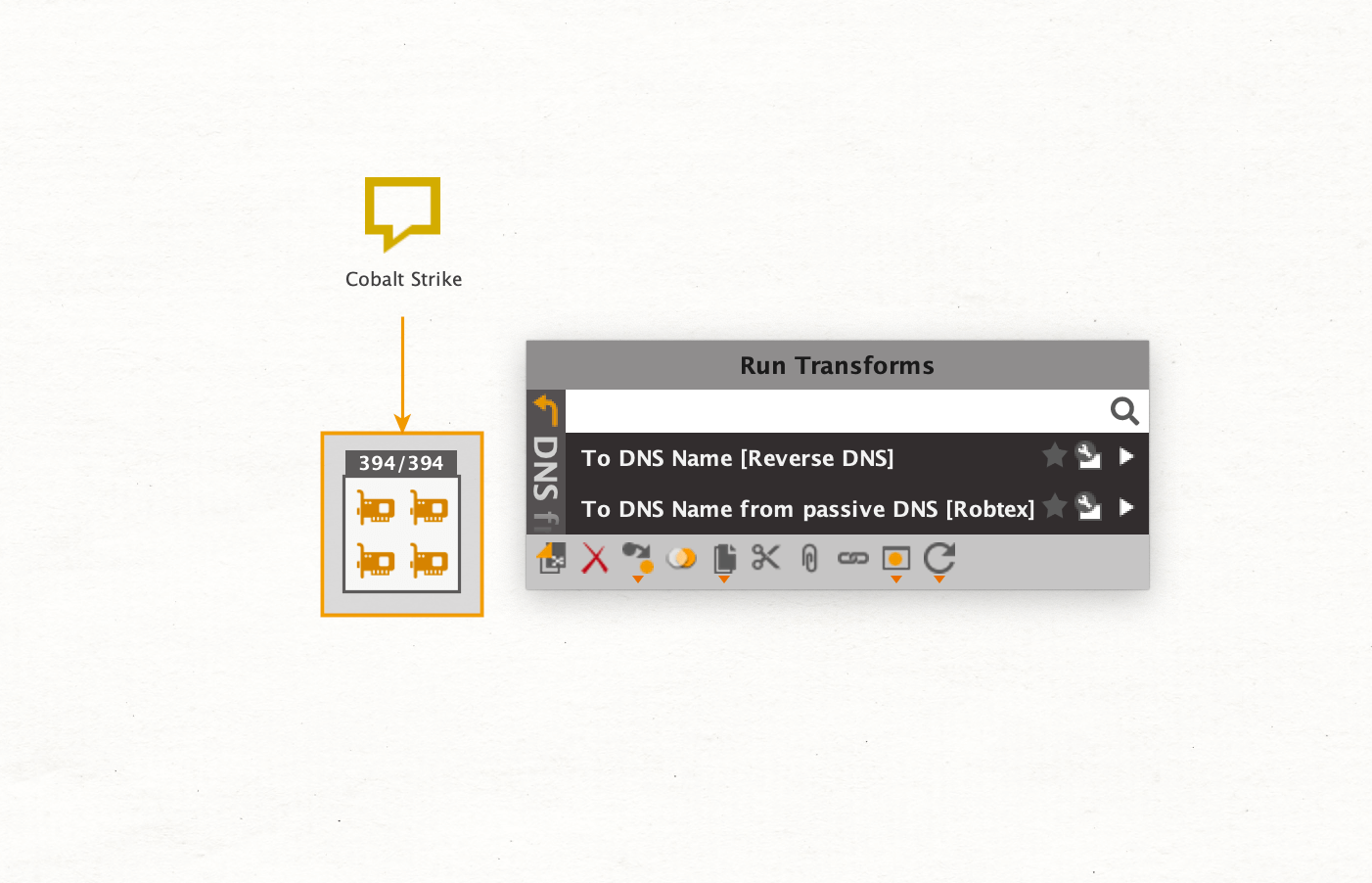
Our results tell us that the returned IP Addresses are related to Cobalt Strike software. To learn more about the scanner’s systems, we will run the To DNS Name [Reverse DNS] Transform which is part of the Maltego Standard Transforms. This query returns the resolved DNS names for each IP Address.
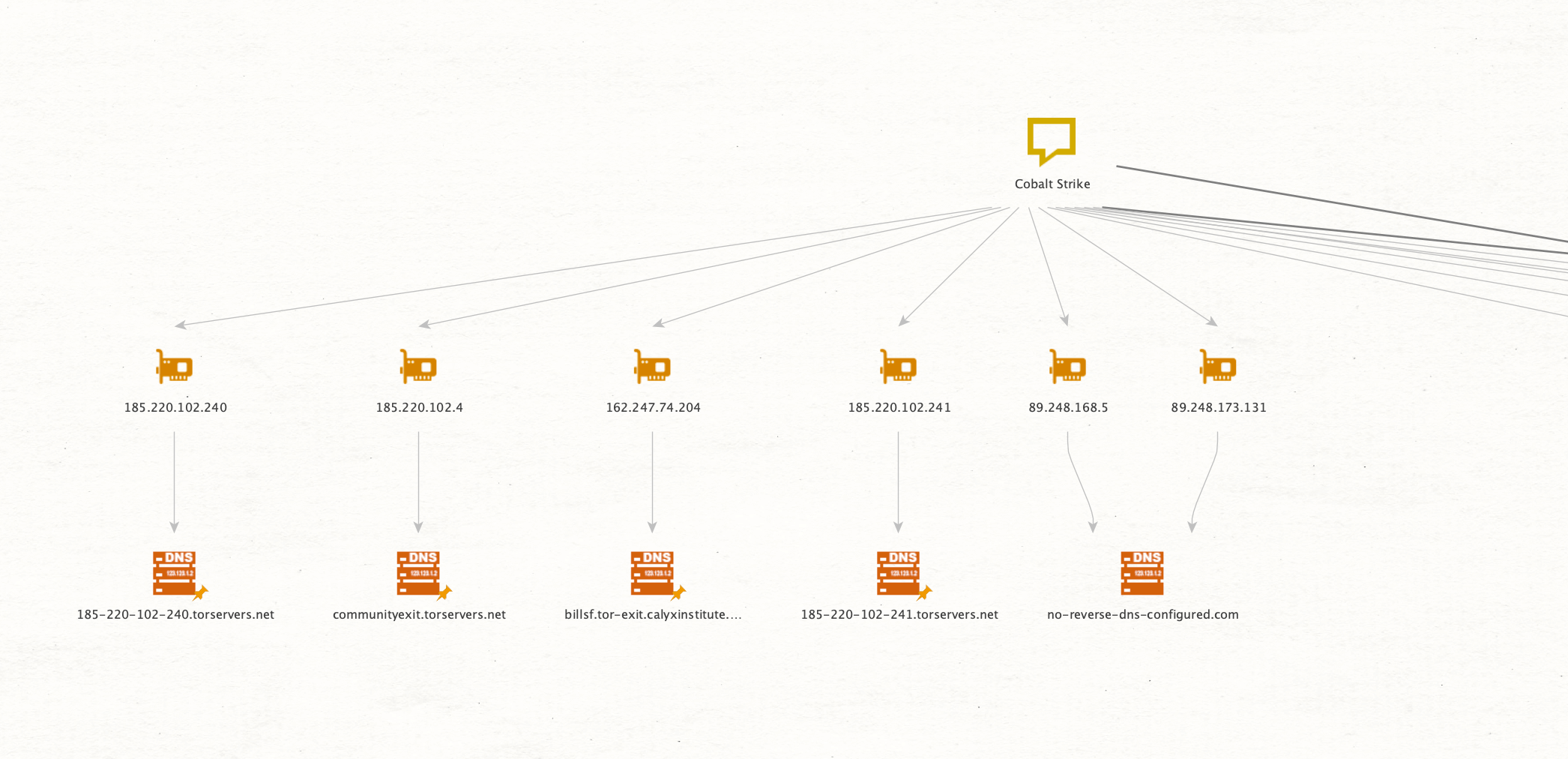
Now we can easily identify public Tor Exit Nodes by inspecting the DNS Names.
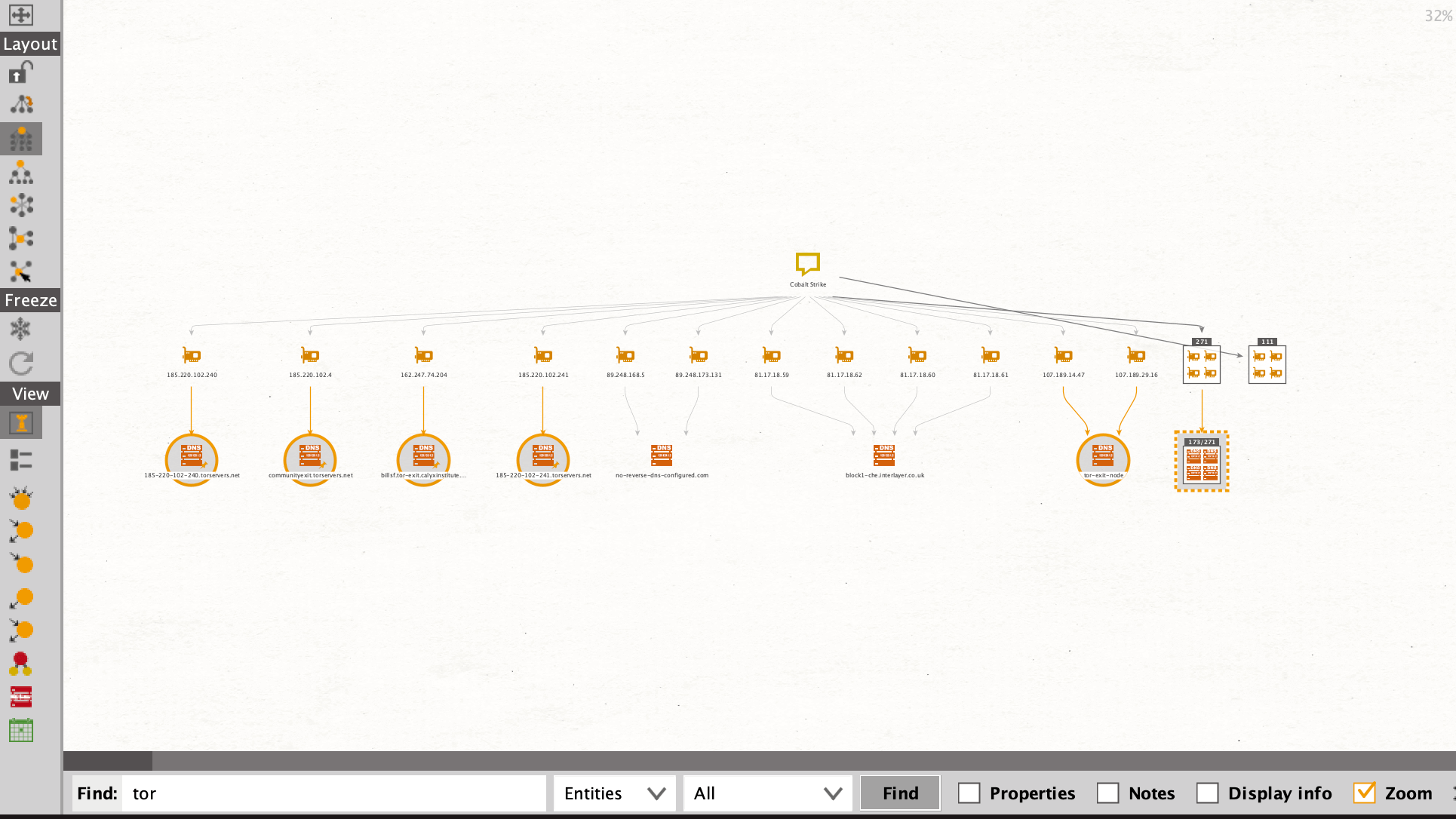
Through the use of Tor exit nodes, scanners can hide their source location. Since we want to find the origin location in this investigation, we will exclude all of these nodes by using the search function to find all “tor” substrings in DNS Entities. This will automatically select the Entities containing this pattern.
We will then add the Parent Entities to the selection, which selects the related IP Address Entities, and remove all of them from the graph.
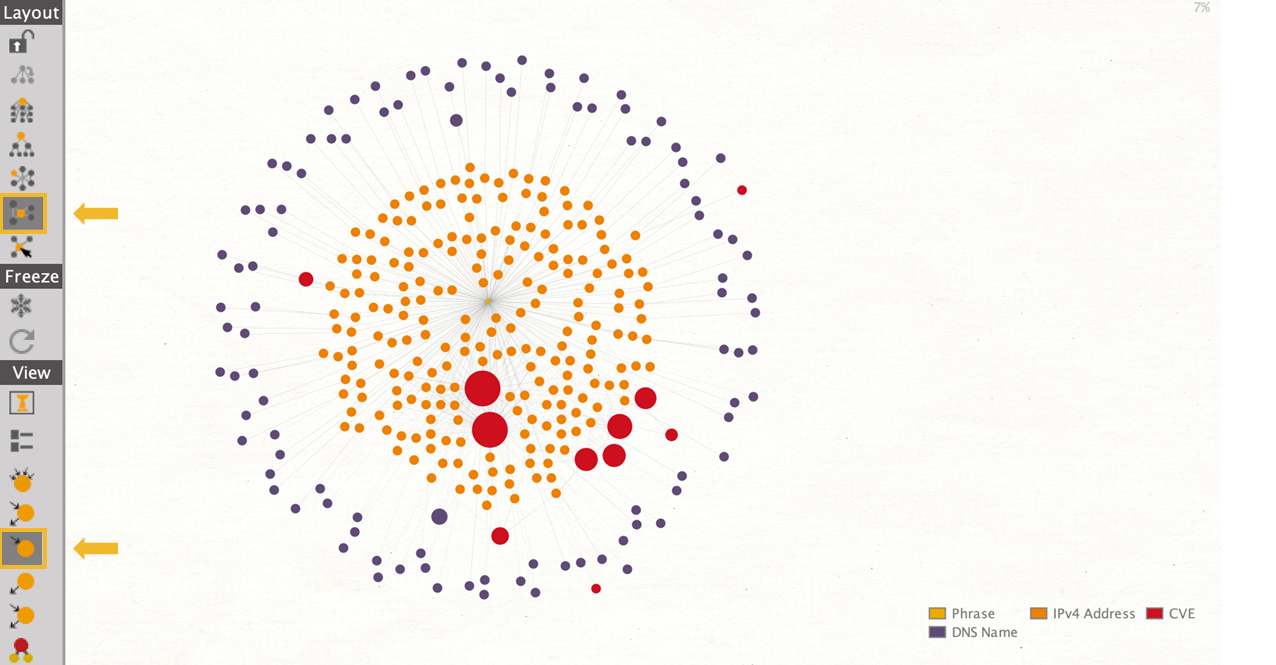
This declutters the graph, leaving us with 323 Entities remaining (at the time of this investigation).
Now, we want to learn which CVEs the scanners are interested in. To do so, we will run the Transform To Scanned CVEs [GreyNoise]. Since we are interested in the most frequently searched vulnerabilities, we change the view to Ball size by incoming links and then change the layout to organic.
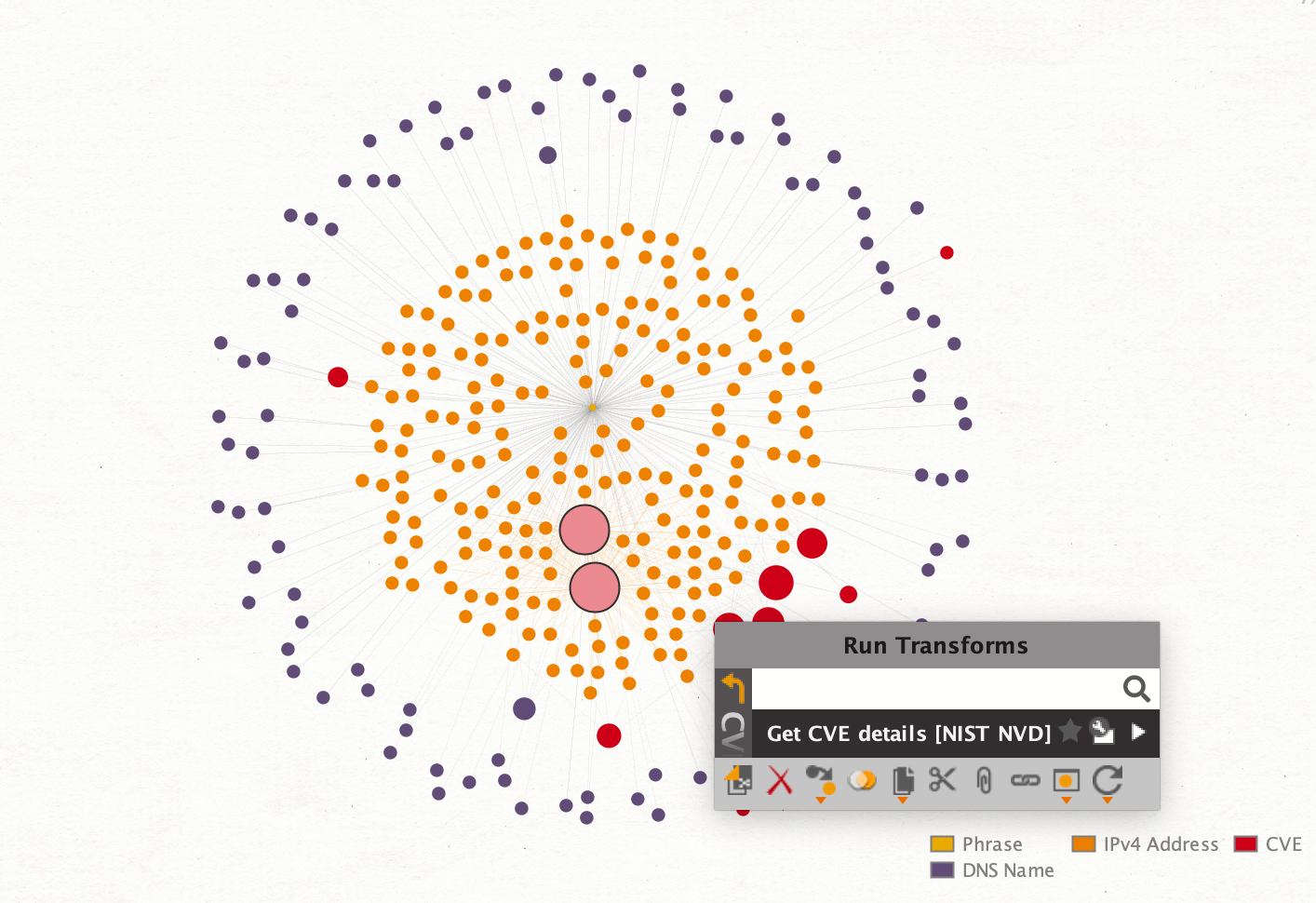
Through this change we can make the most out of the link analysis capabilities of Maltego easily identifying the most frequently searched CVEs (indicated by the large red nodes in the graph).
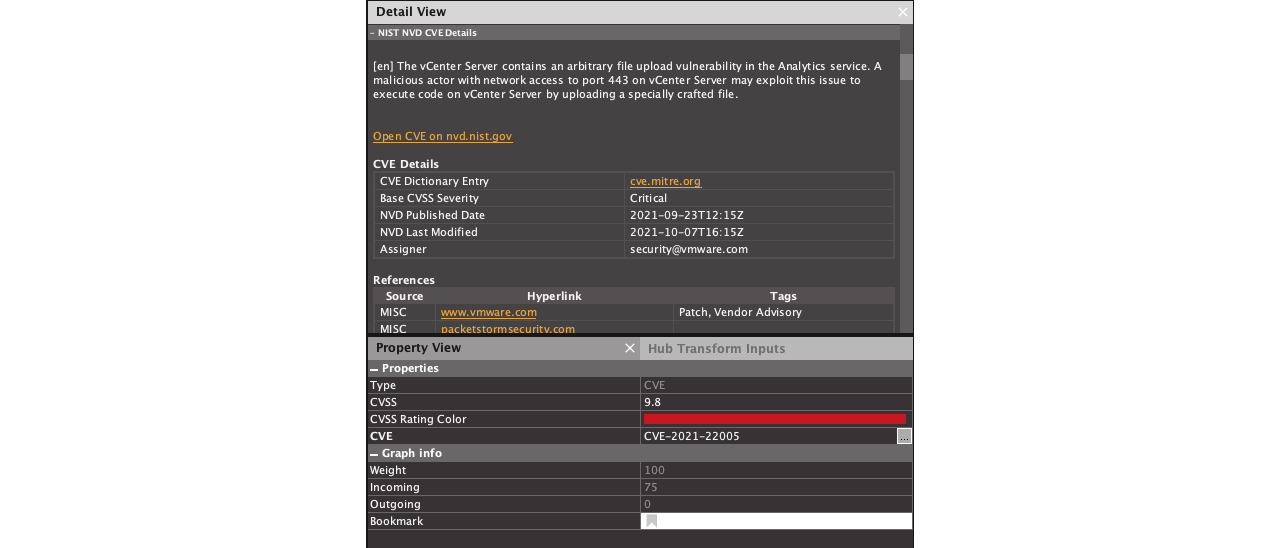
To gain more information on the CVEs, we run the Get CVE details [NIST NVD] Transform, from the NIST NVD Hub Item.
This Transform enriches the CVE Entity with information from NIST’s National Vulnerability Database and helps assess the risk of a specific vulnerability. The CVSS for the most searched CVEs in this investigation is 9.8 for CVE-2021-22005 and 5.3 for CVE-2021-22017 (on a scale of 10.0).
Upon looking up Information about the vulnerabilities, we find that the actor behind these scans is looking for already documented exploits. At the time of this investigation, a technical writeup from Randori Security Team and a working POC is described on Twitter by the user wvuuuuuuuuuuuuu.
By now, we have answered the first question of our investigation and found the vulnerabilities tagged with Cobalt Strike that have been searched for the most by scanners according to the GreyNoise dataset.
Next, we will look for the origins of these scans.
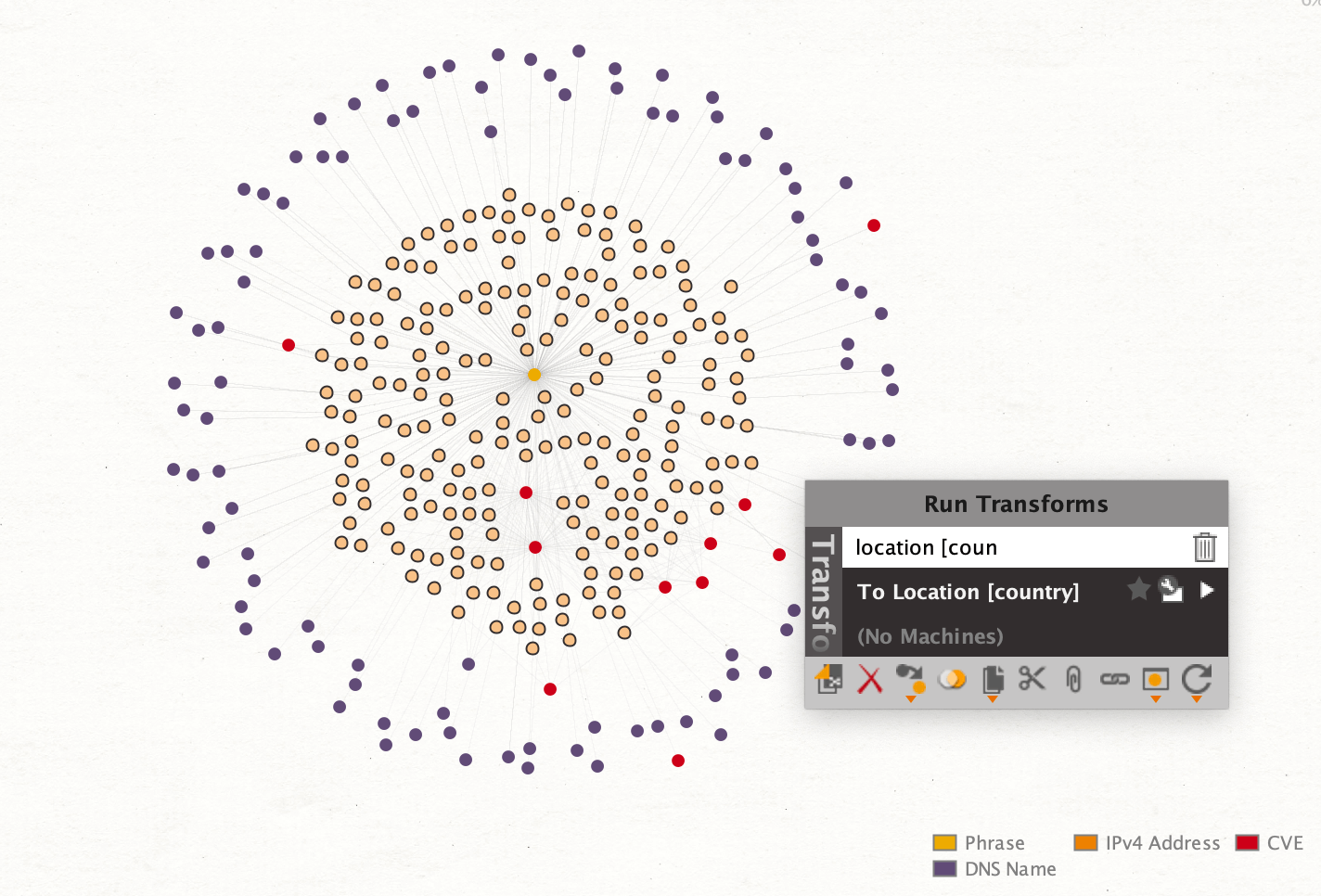
First, we select the two CVE Entities and add the Parent Entities—the IP Addresses related to these CVEs—to the selection. We then run the To Location [country] Transform on these Entities.
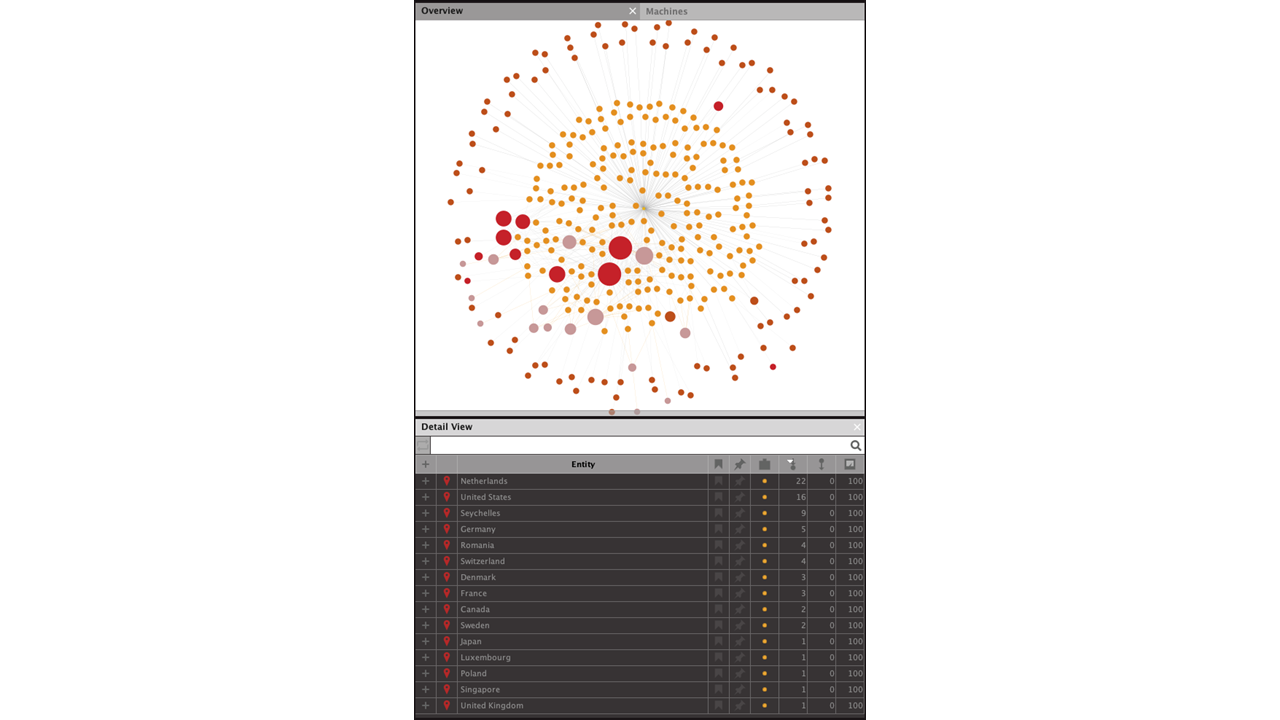
By running the Transform, the graph will be enriched with the IP Address’s geolocation and originating country.
This allows us to answer our second question for this investigation: Where did those scans come from?
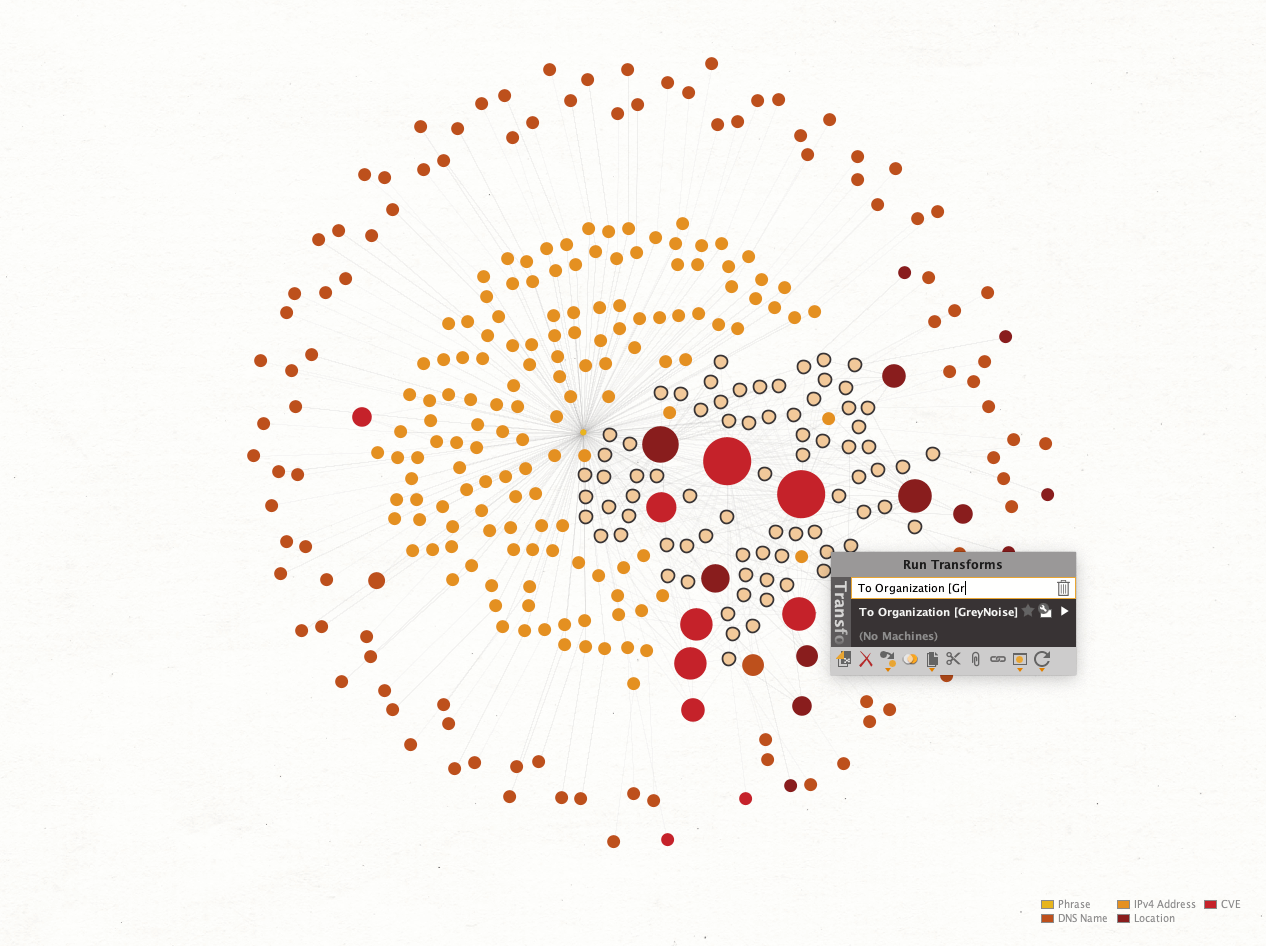
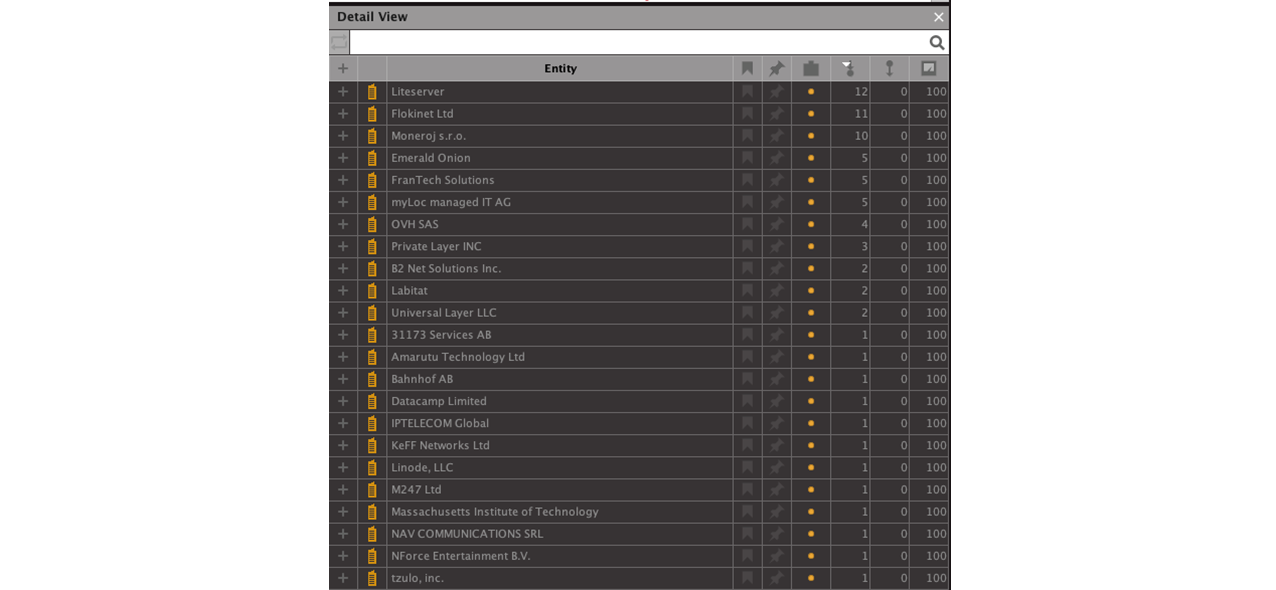
Finally, we want to see which companies are associated with the IP addresses and can be contacted to carry out a takedown. We also want to find out which hosting services are used by the threat actors. Again, we select the IP Addresses related to the CVEs and run the To Organization [GreyNoise] Transform.
With the list of companies in hand, we can further pivot into company databases such as OpenCorporates or Orbis to obtain more information on the company structure and stakeholders.
Start Using the GreyNoise Enterprise Transforms to Accelerate Your Threat Hunting Investigations in Maltego! 🔗︎
GreyNoise Enterprise provides investigators with the powerful capability to search for active-scanning IP addresses, ASs that are known to harbor scanners, and more.
We hope you enjoy the release of the GreyNoise Enterprise data integration for Maltego.
Don’t forget to follow us on Twitter and LinkedIn and sign up for our email newsletter to stay updated on the latest news, tutorials, and events.
Happy Threat Hunting!