The National Vulnerability Database from the National Institute of Standards and Technology is the authoritative resource for vulnerability management. Its database on Common Vulnerability and Exposures (CVEs), is used by organizations worldwide to perform risk and vulnerability assessments, manage compliance, protect digital infrastructure, and respond to cybersecurity incidents.
Empowering Maltego users to protect their organizations from cyber threats is one of our primary goals, and we hope to achieve just that with our new NIST NVD Transforms!
What information can be found in the National Vulnerability Database? 🔗︎
In the National Vulnerability Database, NIST catalogs a CVE’s description, security checklist references, severity using the Common Vulnerability Scoring System, and—using the Common Platform Enumeration (CPE)—the products affected. The CPEs are especially useful to assess your organization’s exposure to threats.
NIST also classifies vulnerabilities by their instigating (software or hardware) weaknesses, or Common Weakness Enumeration (CWE), thus helping users understand the cause of vulnerabilities.
What type of information can be discovered using the NIST NVD Transforms? 🔗︎
All the information mentioned above! These Transforms use the existing maltego.CVE Entity, as well as two additional new Entities: maltego.CPE and maltego.CWE.
Also, the maltego.Phrase Entity can be used to search for CVEs and CPEs in the NIST Database. This way, it is possible to, for example, search for all the CVEs affecting a particular vendor or product.
You can use the Get CVE details [NIST NVD] Transform to retrieve additional information on CVEs in your graph, including a description, references, links back to the NIST NVD database, and the CVSS Score. This score is also represented by colored overlays, which range from green to red, depending on their severity.
From a CVE Entity you can also lookup its corresponding CPEs and CWEs.
Note
Since the maltego.CVE Entity inherits from the maltego.Phrase Entity, you can also run the Search for CPEs [NIST NVD] and Search for CVEs [NIST NVD] Transforms on these, however, you may not always be able to retrieve meaningful results. For a more reliable way to find the CPEs of products or platforms affected by a specific CVE, you should run To CPE [NIST NVD] on the CVE Entity instead.
As with the CVE Entities, you can use the Get CPE details [NIST NVD] to obtain further information on the CPEs under investigation.
CPEs are useful to understand what products might be the most vulnerable, especially if we discover through our investigation that there are multiple vulnerabilities impacting certain products.
You can also find other CVEs this product might be vulnerable to by running the To CVE [NIST NVD] Transform.
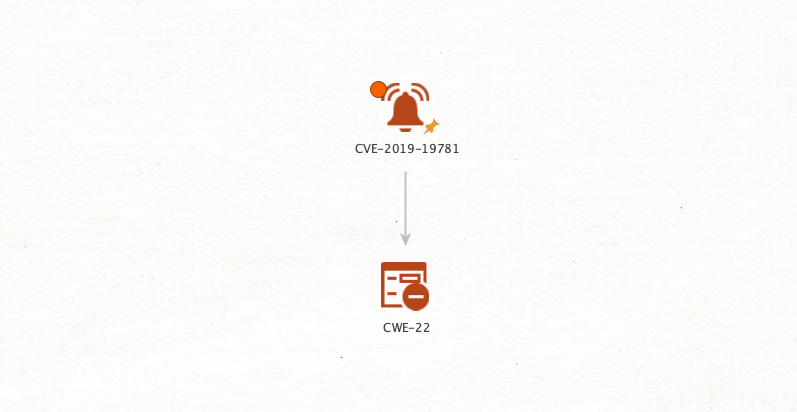
CWEs describe the software or hardware weaknesses that expose products to vulnerabilities. CWEs are especially handy when developing your own product, to raise awareness of common mistakes in development and to help prevent them.
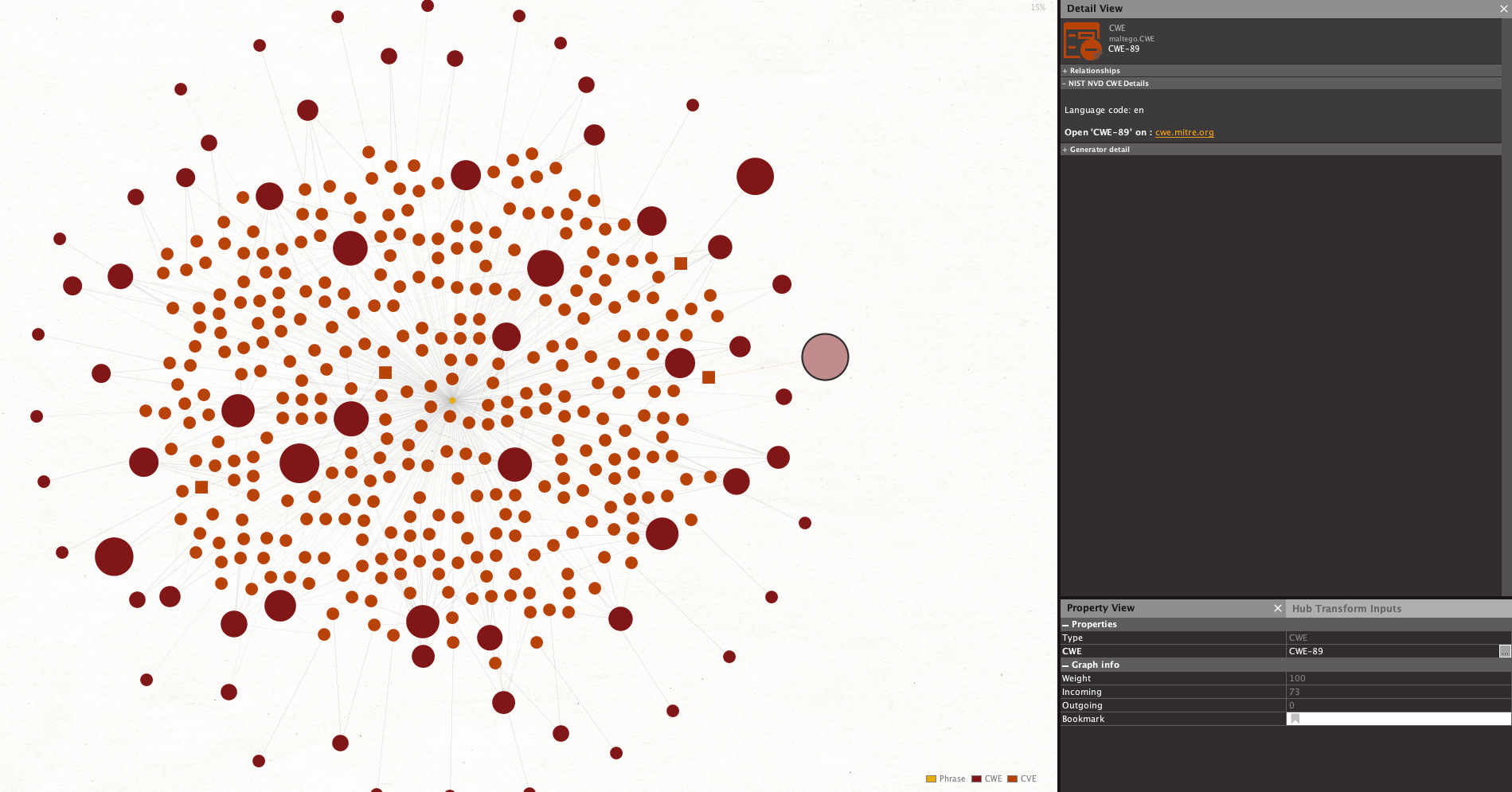
For example, by running the To CWE [NIST NVD] Transform on CVEs with a critical CVSS Score published in the last 90 days, we can see that their most common causing weakness is the CWE-89 (SQL injection).
What are the Requirements to use the NIST NVD Transforms in Maltego? 🔗︎
You can use these Transforms with any version of Maltego! The NIST NVD Transforms do not require registration and are free to use by all our users.
What might an investigation using these Transforms look like? 🔗︎
As an analyst running a vulnerability scan on your organization’s systems, you may be able to use the Maltego Splunk integration to help you quickly sift through event data and evaluate it critically. Given some CVEs surfaced from your Vulnerability events data, this new NVD integration enables you to quickly glean context by using the Get CVE details [NIST NVD] Transform to evaluate the severity of the CVEs found.
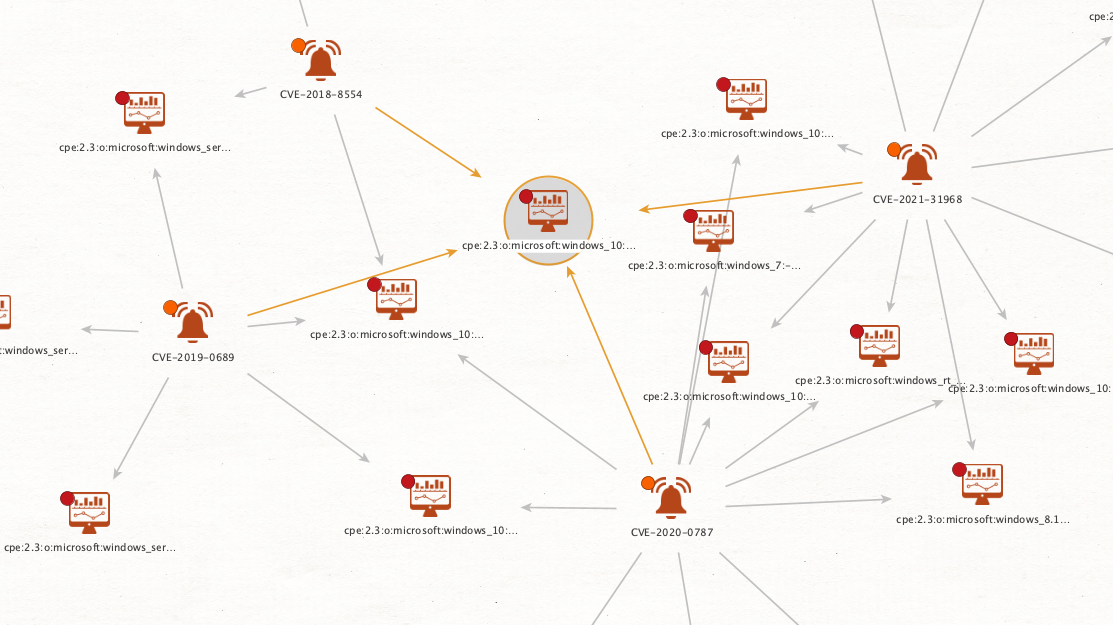
Then, you choose the CVEs rated “High” and “Critical” (identifiable by their orange and red overlays) and copy them to a new graph for further analysis. In the new graph, run the To CPE [NIST NVD] Transform to find which specific products might be affected by the vulnerabilities.
Finally, by visualizing the data using the Ball Size by Links (Incoming) View, you will notice that your organization’s computers that are running Windows 10 are exposed to the highest number of vulnerabilities. From there, you can create an actionable plan for those specific systems to be patched. You could even send your colleague a link to the relevant patches listed directly in the CVE’s Detail View in Maltego.
Using the NIST NVD Transforms, you have started with a group of CVEs sourced from simple Splunk event data, prioritized them by severity and found the affected systems and necessary patches in a manner of minutes.
Start using the NIST NVD Transforms to defend Your organization from Cyber Threats! 🔗︎
We hope you enjoy this article and benefit from the release of the NIST NVD data integration for Maltego.
Don’t forget to follow us on Twitter and LinkedIn and sign up for our email newsletter to stay updated on the latest news, tutorials, and events.