Phishing is one of the oldest and most common cyber threats. From individual online shoppers to corporation managers, any internet user can be potentially subjected to phishing attacks.
Phishing Attacks: A Two-Part Maltego Blog Series 🔗︎
As part of our celebration of Cybersecurity Awareness Month, we have created a two-part blog series to raise awareness of phishing tactics and how one can conduct simple but insightful phishing investigations with Maltego.
In Part 1 of this series, we will explain how phishing attacks are commonly carried out, what the goals of phishing are, and how to spot phishing content.
Infographic | What You Should Know About Phishing Activities 🔗︎
What is Phishing and Why is It Done? 🔗︎
A method used by malicious hackers, phishing is the act of stealing critical information and credentials or infiltrating a computer or system with a malware or virus by misleading targets into clicking on a phishing URL, sharing information at the phishing website, or opening a phishing attachment.
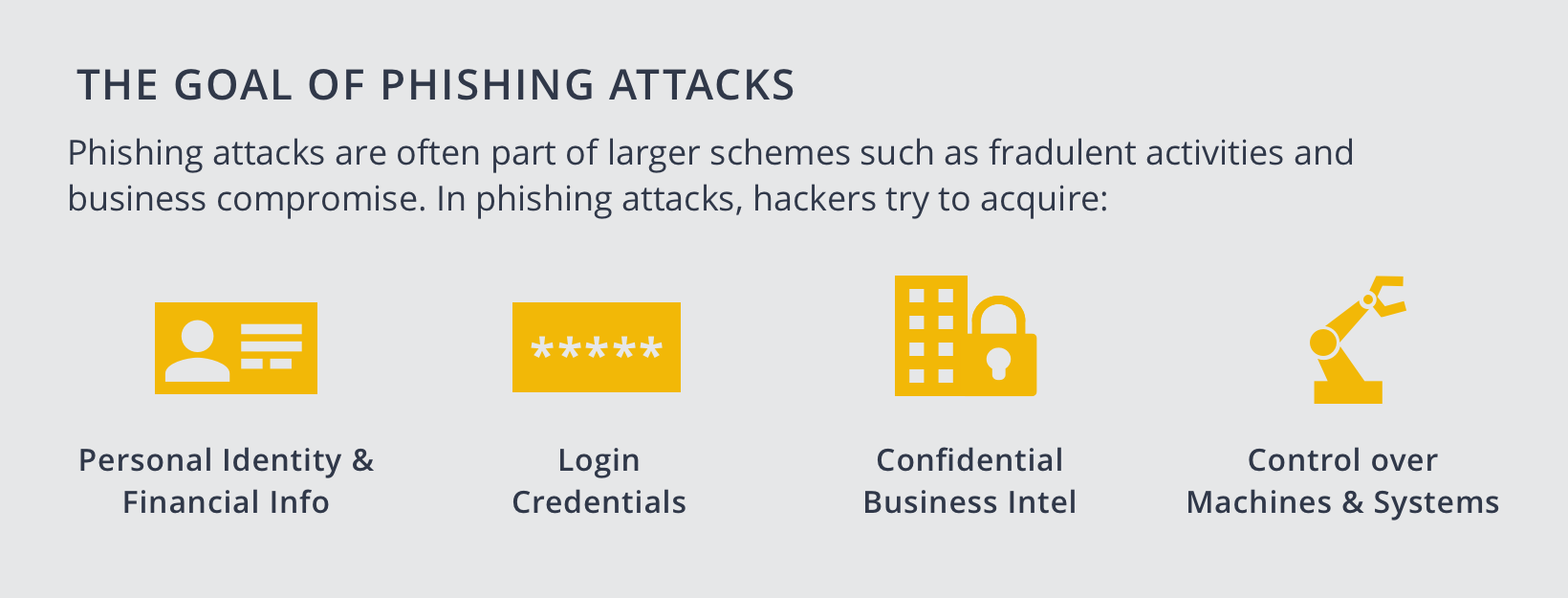
Generally, the goals of phishing attacks can be categorized into four types:
- Acquire personal identity or financial information
- Acquire login credentials to certain services or systems
- Acquire confidential business intelligence or internal data
- Acquire control over compromised computers or network systems
Once the hackers achieve one or more of these goals, they can use the stolen data to perform identity or financial fraud, make malicious configurations to systems, spy on competing companies or organizations, shut down critical system operations, and more.
For example, hackers may create a phishing website, misleading its users to log into their accounts and enter detailed credit card information. Once a phishing victim falls prey to that, the hackers will receive their login email, password as well as credit card information. They can then proceed to use the victims’ credit cards for fraudulent activities or hack into the victims’ social account with the login information acquired and spread more phishing messages.
How is Phishing Typically Conducted? 🔗︎
Although technology has evolved over the past years, the phishing process has not changed much.
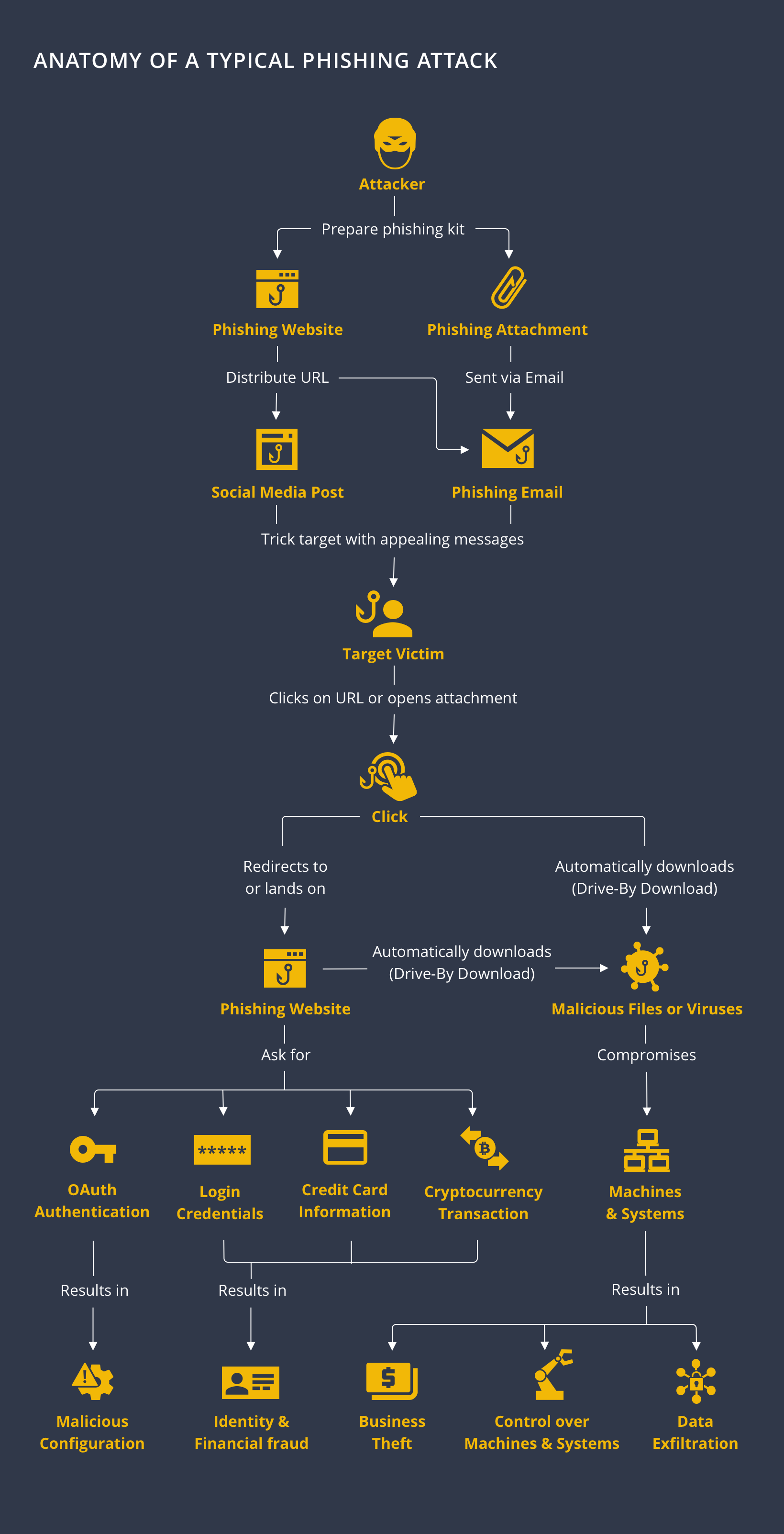
Start with A Website URL or An Email Attachment 🔗︎
Usually, attackers will build a phishing website as a trap, a fake celebrity or business social account, or store the malware in a file for email attachment.
Distributed through Social Media Platforms and Emails 🔗︎
Next, the attackers will distribute the URL or malware file via emails, social media posts, social media direct messages, online advertisements, and other online channels. The hooks used could: promise winning a prize or financial reward, be related to customer support matters such as failed payment notification or a change in bookings, or even a sign-up invitation to a webinar or a business proposal attachment.
All this aims to lure the recipient victim to click on the URL or open the email attachment.
Request of Information or Drive-By Download 🔗︎
Once a target clicks on the URL or open the attachment, two outcomes are possible: They will either be directed or redirected to the phishing website, or a drive-by download will start without the target even being aware.
Landing on the Phishing Website 🔗︎
If a target is led to the phishing website, they are likely to be prompted to log in and share certain private information like credit card credentials. After submitting the information, the targets may or may not be redirected to the legitimate website—so that they remain unalerted—while the data collected is sent to the attackers.
Drive-By Download of Malwares and Viruses 🔗︎
Drive-by download is a method used to plant a malware or a virus in the target’s computer without the computer notifying the user or detecting the download activity. The malware or virus will either start compromising the machine and infecting any connected network or stay silent in the system until receiving instructions from the attackers.
How Can We Spot and Avoid Phishing Activities? 🔗︎
Phishing websites are usually copy-cats of the original websites of the banks, businesses, or service providers. As are the phishing social accounts which display seemingly legitimate user handles and profile pictures.
However, phishing scams often include obvious tell-tale signs or subtle traits that set them apart from legitimate activities. If you take a closer look at the phishing website or email, you can usually spot the clues.
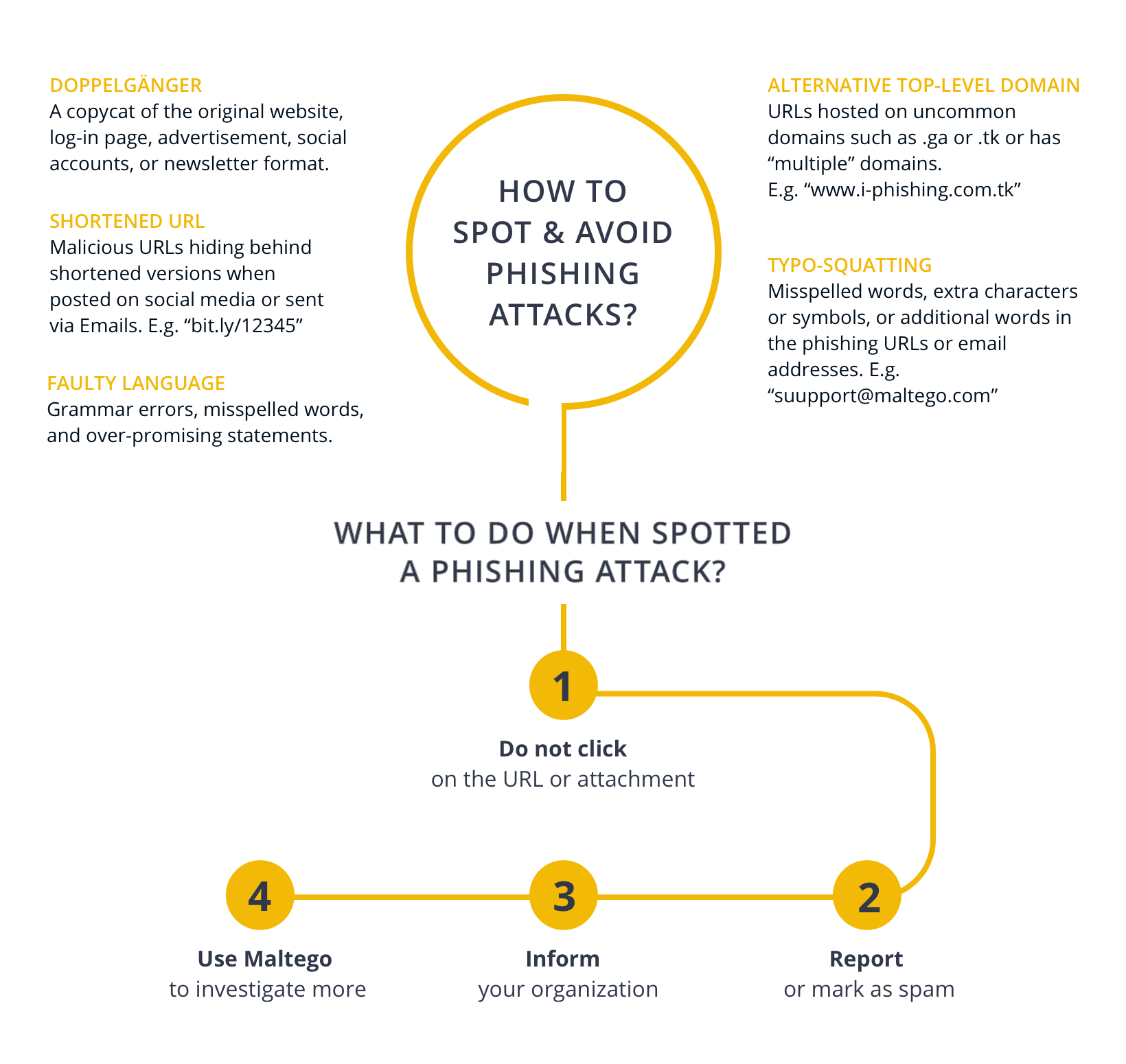
Typo-Squatting 🔗︎
Because attackers cannot use the legitimate website domain or email address—unless they hijack the whole system—they often include misspelled words, extra characters or symbols, or additional words in the phishing URLs or email addresses. E.g. “suupport[at]maltego.com” or “Maltego-support[at]maltego.com” instead of support@maltego.com.
Shortened URL 🔗︎
When sharing the phishing URLs on social media platforms, phishing attackers almost always hide the suspicious-looking URLs behind shortened versions. E.g. “bit[.]ly/12345” instead of “www[.]Maltego-phishing[.]com”
Alternative Top-Level Domains 🔗︎
Phishing attackers also often use top-level domains that are uncommon or similar to country domains—such as .ga or .tk—or even include “multiple” top-level domains in the URLs. E.g. “www[.]i-phishing[.]com[.]tk”
Faulty Language 🔗︎
Very frequently seen in email phishing attacks, the content may contain simple grammatical errors and misspelled words.
What You Should Do When Encountering a Phishing Attack 🔗︎
Do not click on the phishing URL or open the attachment, not even out of simple curiosity. Additionally, there are a few counter- actions you can take when encountering a phishing attack.
What You can Expect in Part 2 of our Phishing Attacks Series 🔗︎
In Part 2 of our Phishing Attacks blog series, we will introduce these counteractions and walk you through a simple but insightful phishing investigation conducted with Maltego. Stay tuned!
Don’t forget to download the infographic about phishing attacks to share it with your connections and industry.
Follow us on Twitter or LinkedIn or subscribe to our email newsletter to stay updated for Part 2 and more tutorials, use cases, and Maltego tips to come!