
Password salting is a technique for making passwords more difficult to crack by adding random values to the stored password hash.
In order to understand password salting and its benefits however, it is necessary to understand how Windows stores passwords and some of the risks that are associated with storing passwords in that way.
Password Hashing and where it falls short on security
When you create a user account within Windows, the operating system does not actually store the account’s password. Otherwise, it would be too easy for malicious software, cybercriminals, or even rogue administrators to simply look up user’s passwords.
Instead, passwords are hashed prior to being stored. In other words, a mathematical formula is used to turn passwords into hexadecimal strings. It is those strings, or hashes, that are stored rather than the password itself.
When a user attempts to log into a system they are prompted for a username and password. When the user types their password, the password that they have entered is hashed by using the same formula that was used to create the stored password hash.
At that point, the hash of the password that the user has just entered is compared against the stored password hash. If the two hashes are identical, then the user has entered the correct password and is therefore allowed to log into the system.
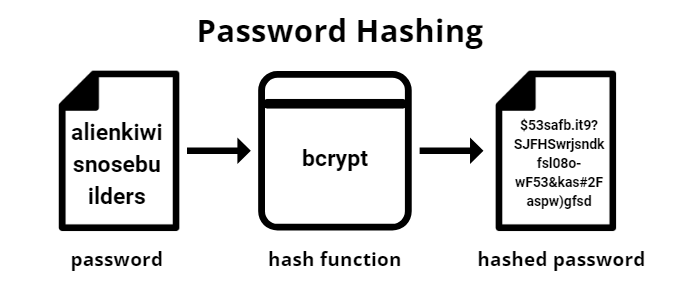
The problem with password hashes is that they can make it easier for an attacker to figure out a user’s password. Lengthy passwords can make brute force password cracking impractical or impossible. However, an attacker can use a password hash as is, skipping the brute force cracking altogether.
The reason why this is possible is because Windows does not use a unique hashing algorithm on each system.
Suppose for a moment that you created an account and then you looked up the hash for that account’s password. If you were to then create a different account on a completely different system, but used the same password as before, then the two accounts would have identical password hashes.
Cyber criminals know this and have created massive databases of passwords and their corresponding hashes. This means that if an attacker wants to crack an account’s password they need only to check to see if the password’s hash is listed in their password database.
If the hash is present in the database, then they can use a simple table lookup to find the password that corresponds to the hash, without the hassles of a brute force crack.
Increasing the security of your AD stored passwords
This is where password salting comes into play. A salt is a value that is added to the user’s password. This happens behind the scenes without the user’s knowledge.
The addition of a salt causes the password’s hash to change, making it far more difficult to use a table lookup as a way of cracking the password.
When properly implemented, salts are random, with a different salt being used for each user. This means that even if two users in your organization have identical passwords their password hashes will differ from one another because a different salt was used for each.
Drawbacks of password salting
Using password salts can be a highly effective way to protect user accounts in your organization. Even so, password salting does have at least a few disadvantages.
- Password salting isn’t quick
First, the salting process is computationally intensive. As such, salting may slow down the user authentication process, particularly in situations where domain controllers are under provisioned or large numbers of users are attempting to log on at the same time.
- Password salting isn’t a beginner-level protocol
Another disadvantage to password salting is that it can be difficult to implement. The Windows operating system does not natively include a salting mechanism. According to Microsoft, “Neither the NT hash nor the LM hash is salted”. As such, salting will require the use of third-party software.
Secure alternatives to password salting
Of course, it is possible to keep your organization’s passwords secure without having to resort to using password salting. Specops Password Policy for example, contains tools to prevent users from using weak passwords.
This not only means enforcing password complexity requirements (even beyond what is possible using Windows alone), but also preventing users from choosing passwords that are susceptible to dictionary attacks that password salting would ordinarily prevent.
More importantly, Specops maintains a database consisting of over 3 billion passwords that are known to have been compromised.
Specops Password Policy actively compares user’s passwords to this database to see if the user is using a compromised password, and then forces a password change if necessary. You can test out Specops Password Policy in your Active Directory with a free trial, anytime.
Remember, table-based lookup attacks are only effective if the user’s password hash is listed in the table. Specops Password Policy can help to prevent users from using any passwords that are known to be vulnerable to these types of attacks.
The result is a level of protection that is comparable to that of password salting, but without the hassles of managing salts.
Sponsored and written by Specops Software



