
A threat actor named InTheBox is promoting on Russian cybercrime forums an inventory of 1,894 web injects (overlays of phishing windows) for stealing credentials and sensitive data from banking, cryptocurrency exchange, and e-commerce apps.
The overlays are compatible with various Android banking malware and mimic apps operated by major organizations used in dozens of countries on almost all continents.
Being available in such numbers and at low prices, allows cybercriminals to focus on other parts of their campaigns, development of the malware, and to widen their attack to other regions.
Typically, mobile banking trojans check what apps are present on an infected device and pull from the command and control server the web injects corresponding to the apps of interest.
When the victim launches a target app, the malware automatically loads the overlay that mimics the interface of the legitimate product.
InTheBox provides up-to-date injects for hundreds of apps, researchers at threat intelligence company Cyble discovered.
.png)
According to Cyble’s analysis, as of January 2023 InTheBox lists the following web inject packages, updated as recently as October 2022:
- 814 web injects compatible with Alien, Ermac, Octopus, and MetaDroid for $6,512
- 495 web injects compatible with Cerberus for $3,960
- 585 web injects compatible with Hydra for $4,680
For those who don’t want to buy entire packages, InTheBox also sells web injects individually for $30 each. The shop also allows users to order custom injects for any malware.
InTheBox’s web inject packages include app icon PNGs and an HTML file with JavaScript code that collects the victim’s credentials and other sensitive data.
.png)
In most cases, the injects feature a second overlay that requests the user to enter credit card numbers, expiration dates, and CVV numbers.
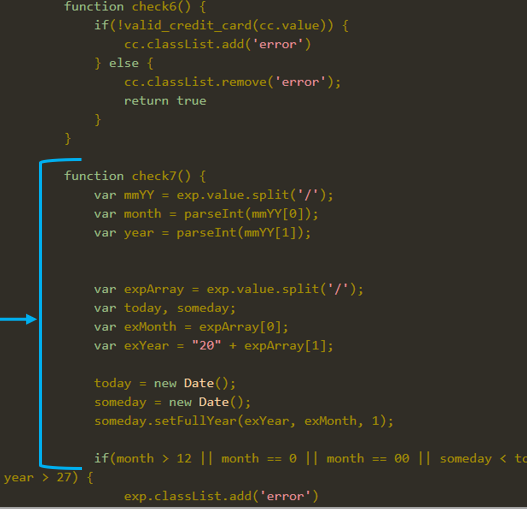
Cyble says that InTheBox’s injects can check the validity of the credit card numbers entered by victims using the Luhn algorithm, which helps Android malware operators filter out invalid data.
.png)
Finally, the stolen data is converted into string value and sent to a server controlled by the operator of the Android banking trojan.
InTheBox has been selling web injects for Android malware since February 2020, constantly adding new pages that target more banks and financial apps.
Cyble was able to confirm that InTheBox’s web injects have been used by the ‘Coper’ and the ‘Alien’ Android trojans in 2021 and September 2022, respectively, while the most recent campaign occurred in January 2023 and targeted Spanish banks.



