Unlocking the Power of Apepe: Enumerate Information From Android Apps
Are you a pentester or red teamer looking to extract crucial information from your target application effortlessly? Look no further than Apepe, the Python tool designed to streamline your information-gathering process. In this comprehensive guide, we’ll delve into the features, installation, and usage of Apepe, ensuring you can maximize its potential for your next project.
Apepe is a Python tool developed to help pen-testers and red teamers easily get information from the target app. This tool will extract basic information as the package name, if the app is signed, and the development language…
Installing / Getting Started
A quick guide on how to install and use Apepe.
1. git clone https://github.com/oppsec/Apepe.git
2. pip install -r requirements.txt
3. python3 main -f <apk-file.apk>Pre-requisites
Before diving into Apepe, make sure you meet the following prerequisites:
- Python Installed: Apepe relies on Python, so ensure it’s installed on your machine.
- APK File: You’ll need the .apk file from your target mobile app to begin your information-gathering journey.
Unveiling Apepe’s Features
Apepe boasts an impressive array of features that set it apart from the competition. Let’s explore its capabilities:
1. Detect Mobile App Development Language
Apepe’s intuitive algorithms can swiftly identify the development language used in the target mobile app. This insight can be invaluable for tailoring your penetration testing strategies.
2. Information Gathering
Effortlessly gather essential information, including the package name and whether the app is signed. This is the core function of Apepe, simplifying your reconnaissance process.
3. Blazing Speed
Apepe is designed to be exceptionally fast, ensuring you can extract information swiftly and efficiently without unnecessary delays.
4. Resource-Efficient
With low RAM and CPU usage, Apepe won’t bog down your system’s performance, allowing you to focus on what matters most – analyzing the gathered data.
5. Powered by Python
Built using Python, Apepe benefits from the versatility and robustness of this programming language, making it a dependable choice for your pentesting needs.
Real-Life Example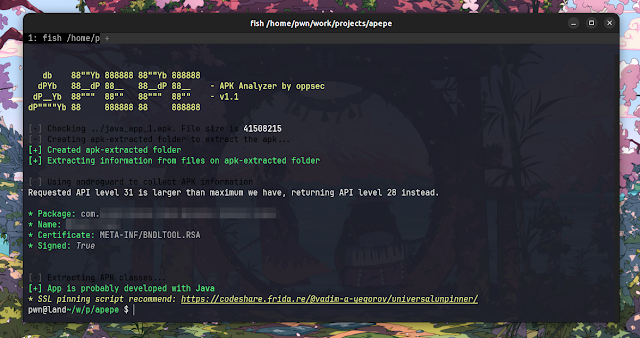
Let’s take a look at a practical scenario to illustrate Apepe’s utility:
Imagine you’re tasked with analyzing a mobile app for potential vulnerabilities. With Apepe, you can quickly ascertain the app’s development language, extract key information about the app, and proceed with a targeted assessment.
What’s Next on Apepe’s Roadmap
Apepe’s developers are committed to enhancing its capabilities further. Here’s a sneak peek at what’s on their to-do list:
- Support for .ipa Files (iOS): Apepe’s future updates will include compatibility with .ipa files, expanding its scope to iOS applications.
- Detect Certificate Libraries: Enhance your analysis by identifying the certificate libraries used by the target app, offering deeper insights into its security measures.
- SSL Pinning Scripts: Look forward to an added argument that returns a list of potential SSL Pinning scripts, aiding your assessment of app security.
- Common Vulnerabilities Check: Apepe’s developers are exploring options to incorporate checks for common vulnerabilities, further empowering your testing efforts.
Contributing
A quick guide on how to contribute to the project.
1. Create a fork from Apepe repository
2. Download the project with git clone https://github.com/your/Apepe.git
3. cd Apepe/
4. Make your changes
5. Commit and make a git push
6. Open a pull requestDisclaimer
It’s crucial to note that the developer of Apepe disclaims any responsibility for any malicious use of this tool. Always use Apepe responsibly and adhere to ethical hacking practices.
In conclusion, Apepe stands as a valuable asset for pen testers and red teamers seeking efficient information gathering in their assessments. With its user-friendly installation process and powerful features, Apepe empowers you to uncover insights into your target mobile apps. Remember to use it responsibly and contribute to its development to make it even more robust and effective. Happy pen testing!





10 Responses
I’ve been receiving threats and blackmail attempts from an unknown individual. I need your expertise to identify the person behind this and gather evidence to stop them.
My elderly mother, Marguerite, has fallen victim to a deplorable financial scam that has had devastating consequences for her. This unfortunate incident occurred through a WhatsApp group she joined via her church’s communication channel. The group, seemingly harmless and connected to her faith community, ultimately led her into a trap orchestrated by unscrupulous individuals.
Marguerite is a devout member of her church, and the WhatsApp group appeared to be a place of spiritual connection and support. It pains us to think that the very platform that should offer solace and community became the source of her financial distress.
The scammers within this group managed to gain her trust and manipulate her into parting with her hard-earned savings. The exact details of how this transpired are still unclear, but we know that the financial loss has left her emotionally shattered.
We have reported the incident to local law enforcement, but the complex nature of online scams makes it difficult to trace the perpetrators. We are reaching out to your expertise to help us in tracking down these criminals, recovering the stolen funds, and, if possible, bringing them to justice.
Marguerite’s well-being, both financially and emotionally, is our utmost concern, and we are willing to do whatever it takes to support her in this trying time. We understand the importance of working within the bounds of the law, and we place our trust in your ethical and professional capabilities.
I’m having issues setting up Apepe
I recently lost access to my important password file on my MacBook due to accidental deletion. I’m looking for assistance in recovering it to regain access to my accounts and sensitive information.
A family member has been unjustly treated at work and convicted for a crime they didn’t commit. We are seeking your assistance to gather evidence and overturn the judgment.
My child is being cyberbullied, and we need help identifying the bullies and gathering evidence to put a stop to the harassment.
My social media account was hacked, and I’m seeking help to recover it. I’d also like to uncover the identity of the hacker who’s causing me problems online.
My phone got hacked through Zoom chat, I was working for a group of developers on a blockchain project and I was hacked of all my cryptocurrency. I suspect it is through the mining node on my phone. I am using Samsung S23. How can I cleanse my phone and also find the intruder
I’ve been a victim of online stalking for a while now. I need your team to identify the stalker and help me put an end to this ordeal.
I suspect my business partner is doing dealings behind me but I am not bold enough to confront him without tangible evidence. Is there any way to hack his mobile phone? The phone model is Xiaomi 13T Pro.