
Security researchers have discovered a new backdoor called WhiskerSpy used in a campaign from a relatively new advanced threat actor tracked as Earth Kitsune, known for targeting individuals showing an interest in North Korea.
The actor used a tried and tested method and picked victims from visitors to a pro North Korea website, a tactic known as a watering hole attack.
The new operation was discovered at the end of last year by researchers at cybersecurity company Trend Micro, who have been tracking Earth Kitsune activity since 2019.
Watering hole attack
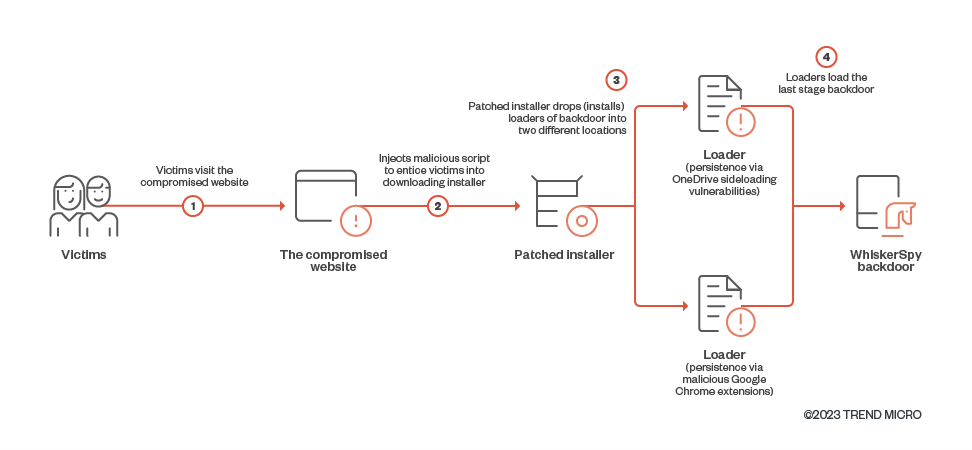
According to Trend Micro, WhiskerSpy was delivered when visitors tried to watch videos on the website. The attacker compromised the website and injected a malicious script that asked the victim to install a video codec for the media to run.
To avoid suspicions, the threat actor modified a legitimate codec installer so that it ultimately loaded “a previously unseen backdoor” on the victim’s system.
source: Trrend Micro
The researchers say that the threat actor targeted only visitors to the website with IP addresses from Shenyang, China; Nagoya, Japan; and Brazil.
It is likely that Brazil was used only for testing the watering hole attack using a VPN connection and the real targets were visitors from the two cities in China and Japan. Relevant victims would be served the fake error message below that prompts them to install a codec to watch the video.
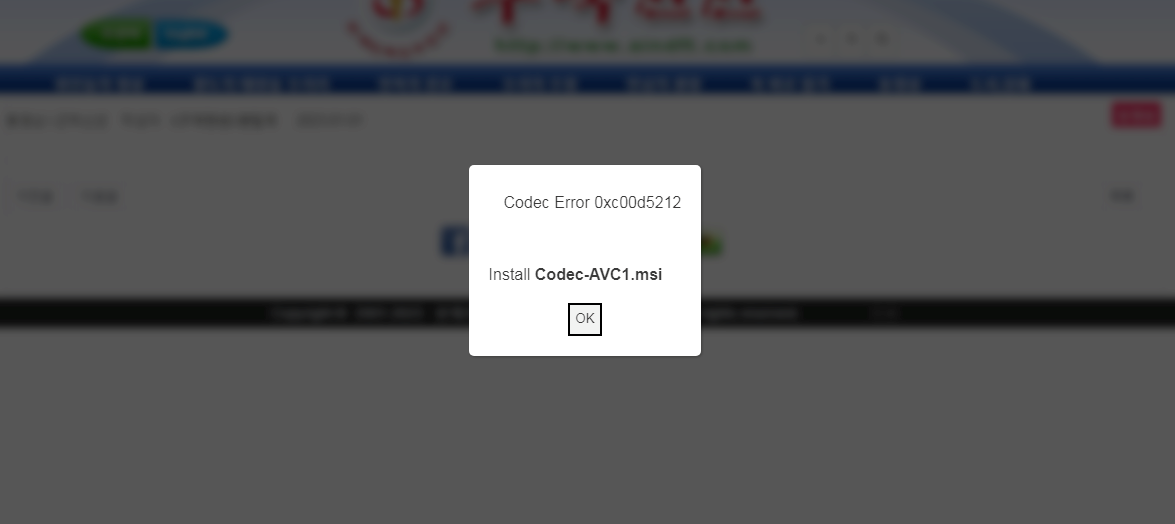
In reality, the codec is an MSI executable that installs on the victim’s computer shellcode that triggers a series PowerShell commands that lead to deploying the WhiskerSpy backdoor.
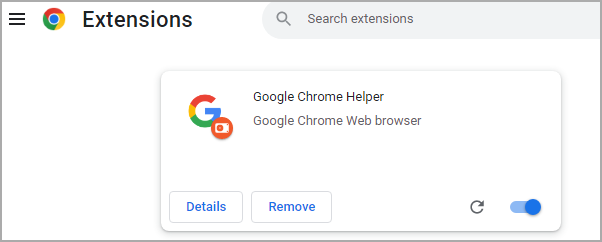
The researchers note that one persistence technique that Earth Kitsune used in this campaign abuses the native messaging host in Google Chrome and installs a malicious Google Chrome extension called Google Chrome Helper.
The role of the extension is to allow execution of the payload every time the browser starts.
The other method to achieve persistence is by leveraging OneDrive side-loading vulnerabilities that allow dropping a malicious file (fake “vcruntime140.dll”) in the OneDrive directory.
WhiskerSpy details
WhiskerSpy is the main payload used in the latest ‘Earth Kitsune’ campaign, giving remote operators the following capabilities:
- interactive shell
- download file
- upload file
- delete file
- list files
- take screenshot
- load executable and call its export
- inject shellcode into a process
The backdoor communicates with the command and control (C2) server using a 16-byte AES key for encryption.
WhiskerSpy periodically connects to the C2 for updates about its status and the server may respond with instructions for the malware, such as execute shell commands, inject code to another process, exfiltrate specific files, take screenshots.
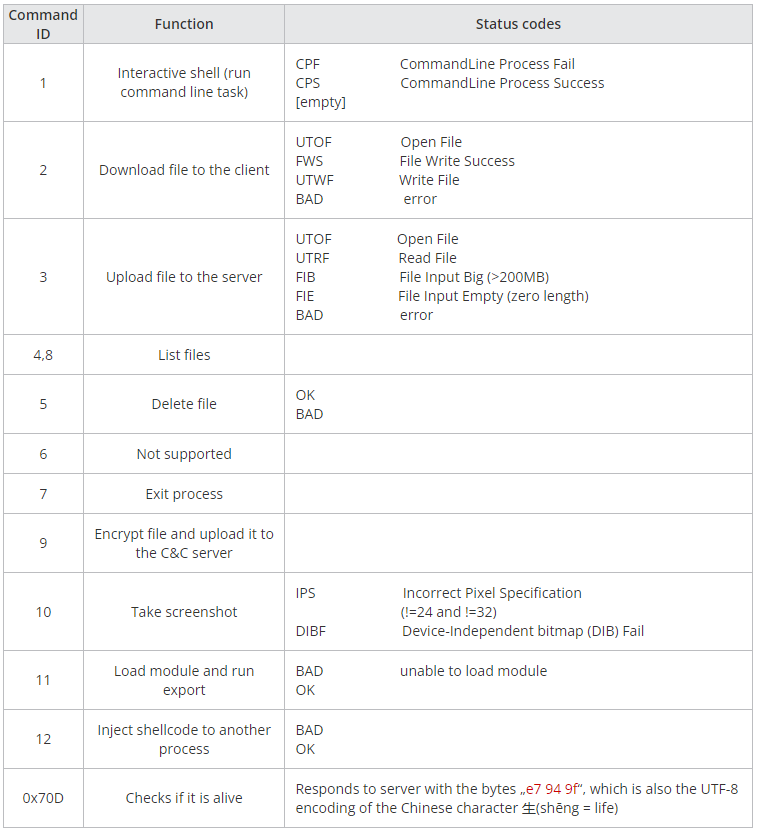
Trend Micro has discovered an earlier version of WhiskerSpy that use the FTP protocol instead of HTTP for C2 communication. This older variant also checks for the presence of a debugger upon execution and informs the C2 with the appropriate status code.
To note, the researchers’ confidence in attributing this watering hole attack to Earth Kitsune is medium but the modus operandi and the targets are similar to activities previously associated to the group.



