
A massive ad fraud operation dubbed ‘Vastflux’ that spoofed more than 1,700 applications from 120 publishers, mostly for iOS, has been disrupted by security researchers at cybersecurity company HUMAN.
The operation’s name was derived from the VAST ad-serving template and the “fast flux” evasion technique used to conceal malicious code by rapidly changing a large number of IP addresses and DNS records associated with a single domain.
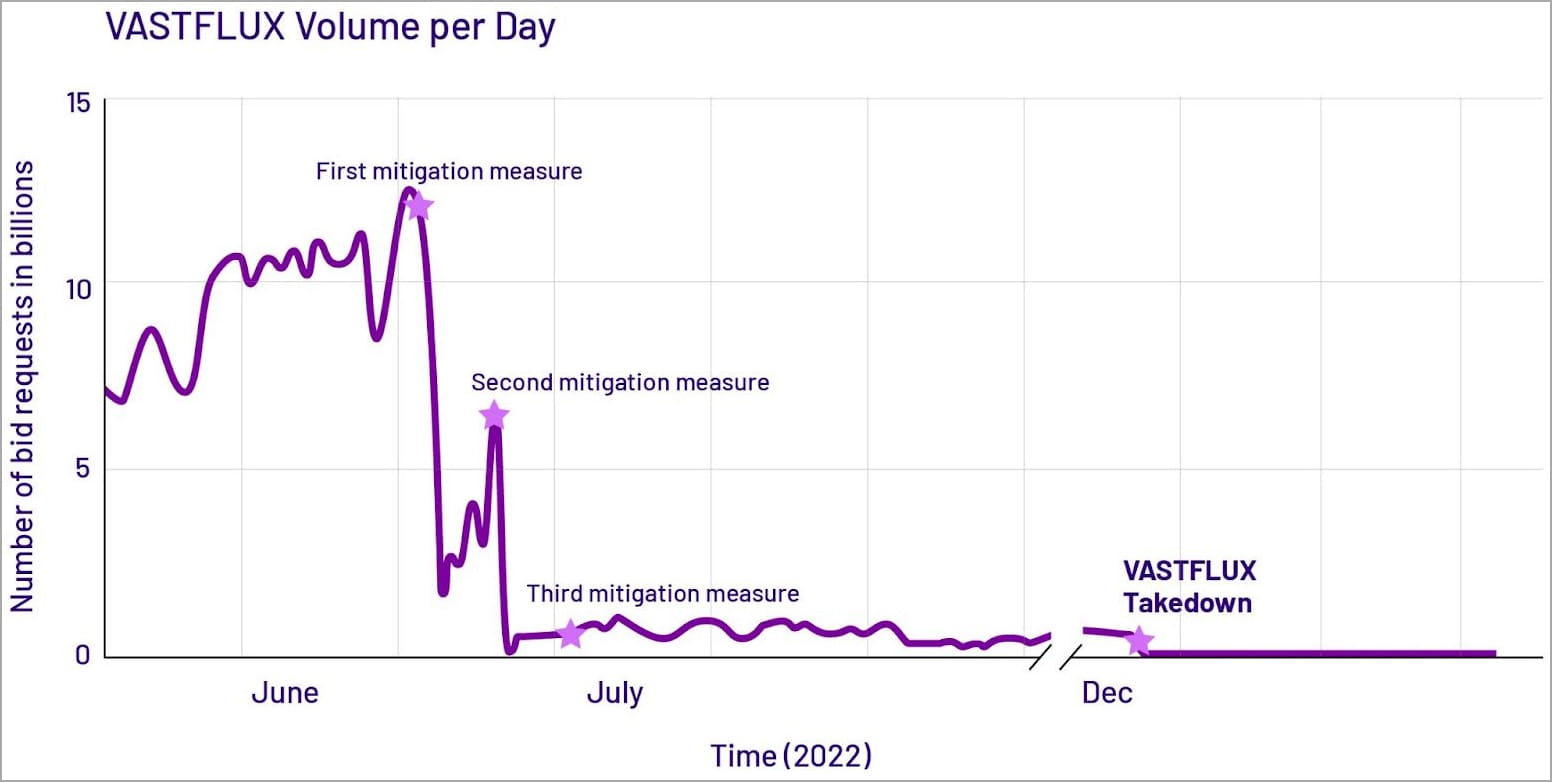
According to HUMAN’s report, Vastflux generated over 12 billion bid requests per day at its peak and impacted almost 11 million devices, many in Apple’s iOS ecosystem.
Vastflux details
The research team at HUMAN (Satori) discovered Vastflux while investigating a separate ad fraud scheme. They noticed noticed that an app was generating an unusually large number of requests using different app IDs.
By reverse engineering the obfuscated JavaScript that operated in the app, the Satori team discovered the command and control (C2) server IP address it was communicating with and the ad-generating commands it sent.
Vastflux generated bids for displaying in-app ad banners. If it won, it placed a static banner image and injected obfuscated JavaScript into it.
The injected scripts contacted the C2 server to receive an encrypted configuration payload, which included instructions on the position, size, and type of ads to be displayed, as well as data for spoofing real app and publisher IDs.
Vastflux stacked up to 25 video ads on top of one another, all generating ad view revenue, but none of them was visible to the user as they were rendered behind the active window.
To evade detection, Vastflux omitted the use of ad verification tags, which allows marketers to generate performance metrics. By avoiding these, the scheme was made invisible to most third-party ad-performance trackers.
Vastflux takedown
Having mapped the infrastructure for the Vasstflux operation, HUMAN launched three waves of targeted action between June and July 2022, involving customers, partners, and the spoofed brands, each delivering a blow to the fraudulent activity.
Eventually, Vastflux took its C2 servers offline for a while and scaled down its operations, and on December 6, 2022, the ad bids went down to zero for the first time.
While ad fraud does not have a malicious impact for the app users, it causes performance drops for the device, increases the use of battery and internet data, and can even lead to device overheating.
The above are common signs of adware infections or ad fraud in the device, and users should treat them with suspicion and try to pinpoint the app(s) that account for most of the resource consumption.
Video ads consume much more power than static ads, and multiple hidden video players aren’t easy to hide from performance monitors, so it’s crucial to always keep an eye on running processes and look for signs of trouble.



