
North Korean hackers have found a way around U.S.-imposed sanctions to launder the cryptocurrency proceeds from their heists, according to evidence discovered by blockchain analysts.
The Lazarus Group, as the threat actor is typically referred to, has laundered about $100 million in stolen Bitcoin since October 2022 through a single crypto-mixing service called Sinbad.
Lazarus behind major crypto heists
Last year, the U.S. Treasury’s Office of Foreign Assets Control (OFAC) announced sanctions against the cryptocurrency mixing services Blender and Tornado Cash, which Lazarus had used to launder close to $500 million in illicitly obtained cryptocurrency.
The measure was taken after more than $600 million in crypto assets were stolen from Axie Infinity’s cross-chain bridge in a hack later attributed to the North Korean Lazarus group.
Hackers often use cryptocurrency mixers/tumblers because, for a fee, they allow hiding the origin and owners of the funds by blending the assets of a larger number of users.
source: Elliptic
While the OFAC sanctions did not stop Tornado Cash, they put a stop to Blender, whose operator disappeared after reportedly taking from the mixer almost $22 million in Bitcoin.
According to blockchain analysis company Elliptic, Blender’s operator very likely started in early October 2022 a new service called Sinbad, which is being used by Lazarus to launder assets.
Switching to new mixer
Tom Robinson, Elliptic co-founder and chief scientist, told BleepingComputer that the connection emerged after the Harmony Horizon crypt heist in June 2022 that lead to about $100 million in losses.
Soon after the hack, Elliptic found strong links to Lazarus, something that the FBI confirmed earlier this year, by following the funds through the Tornado Cash mixing service.
Typically, the actor combined Tornado Cash crypto mixing with a custodial-based service, like Blender. This time though, they used another Bitcoin mixer called Sinbad.
source: BleepingComputer
Robinson says that although the Sinbad service is “relatively small,” it has been used to launder the funds stolen by the Lazarus group.
“Tens of millions of dollars from Horizon and other North Korea-linked hacks have been passed through Sinbad to date and continue to do so, demonstrating confidence and trust in the new mixer” – Elliptic
Strong links between Blender and Sinbad mixers
Unlike Tornado Cash, both Blender and Sinbad are custodial mixers, meaning that all cryptocurrency that goes into the service is under the control of the operator; so owners have sufficient confidence to give up command of their funds.
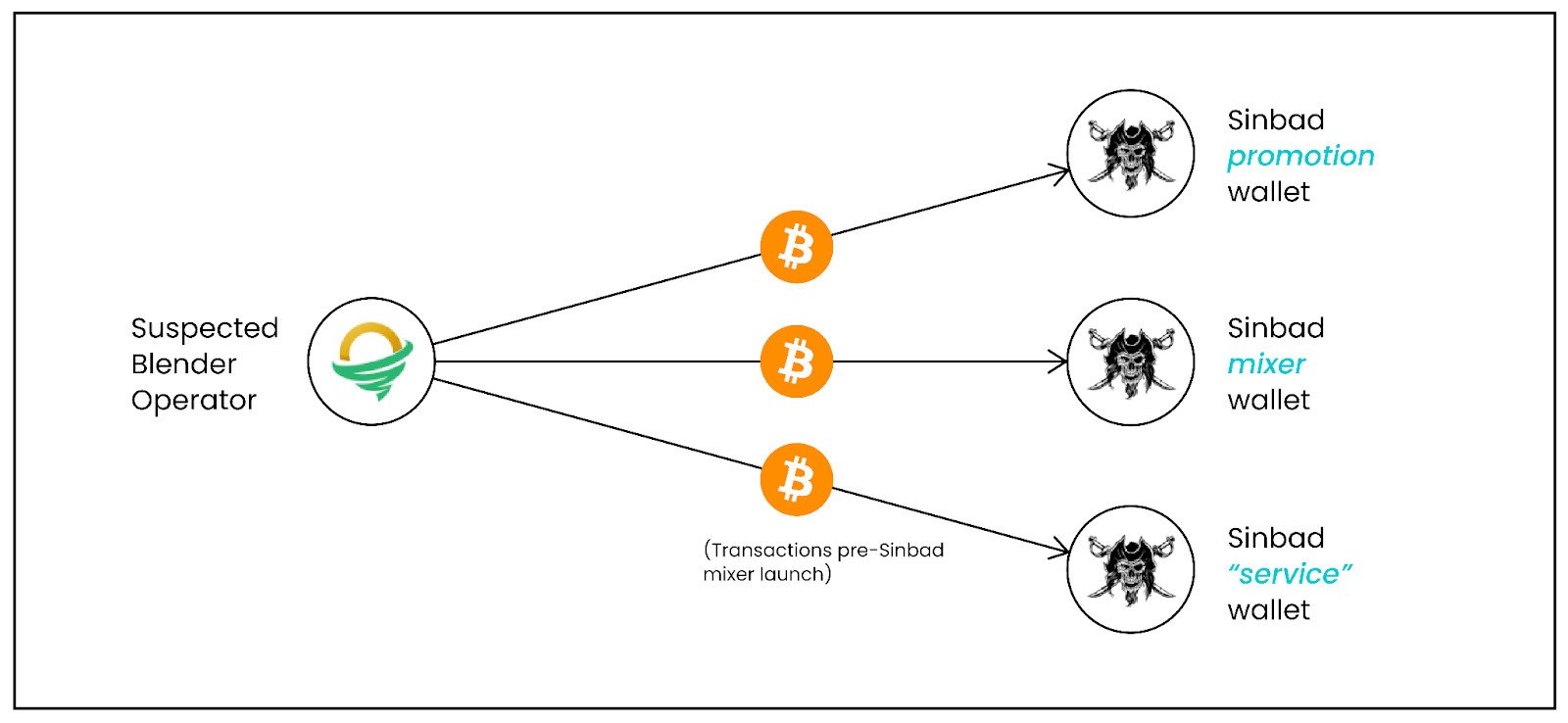
Elliptic’s analysis shows with high confidence that Sinbad is operated by the same individual or group that was behind Blender.
The researchers found that a “service” address on the Sinbad site received Bitcoin from a wallet believed to belong to the operator of Blender.
The same wallet was used to pay for promoting the new crypto mixer and to fund almost all initial transactions coming to Sinbad, about $22 million.
source: Elliptic
Apart from the wallet, the researchers also noticed a similar on-chain pattern behavior for both mixers, which includes specific characteristics of transactions.
“The way in which the Sinbad mixer operates is identical to Blender in several ways, including ten-digit mixer codes, guarantee letters signed by the service address, and a maximum seven-day transaction delay” – Elliptic
Other commonalities the researchers observed include strong similarities in the websites, use of naming conventions, language, and “a clear nexus to Russia, with Russian-language support and websites.”
Although referred to as one group, Lazarus defines multiple North Korean operators tasked by the government with collecting intelligence as well as stealing money to support national-level priorities and objectives.
Besides targeting cryptocurrency exchanges, North Korean threat actors also engaged in ransomware attacks using several locker strains against health sector organizations in the U.S. and South Korea.



