At Maltego, we continuously learn and develop new use cases based on our interactions with customers and end users. This is how the following example of an investigation into insider threats affecting warehouses came about. But first, some context.
Stores, whether online or brick-and-mortar, rely on their warehouse facilities to satisfy their customers’ demands. It is precisely at these locations that they themselves are susceptible to insider threats i.e. employees stealing merchandise. Motivations for this type of activity are broad and can range from employee dissatisfaction to gullibility and lack of better judgement in the face of offers made by criminal networks. In fact, the recruitment of employees has become a very attractive alternative for criminals as increasing physical and cybersecurity measures are being put in place by companies.
With the ever-present potential for inventory to go missing, actions must be undertaken for the investigation, attribution, and remediation of such cases. So, can Maltego help warehouse staff fight off this type of insider threat? The answer is yes. But how? The example provided below relies on criminal tendency to sell the stolen articles on other online marketplaces, and this type of activity can be traced using Maltego.
Preparing for E-Commerce Insider Threats Investigation 🔗︎
For this example, we will assume that small numbers of our inventory have gone missing and we want to figure out if the individual products are being sold off on a third-party Webshop, who may be behind this, and, where the offers are geographically coming from. If this is the first time we are using Maltego for this type of investigation, it is very likely that we will need to do a bit of preparation in the form of Transform writing and Entity creation in order to query the data we require.
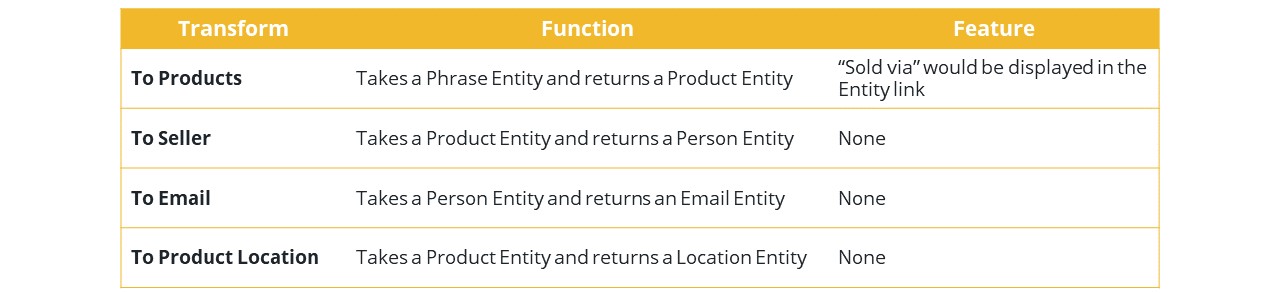
Based on the goals described in the previous paragraph, and after studying the type of data that we need to query for our investigation, we will write the following Transforms:
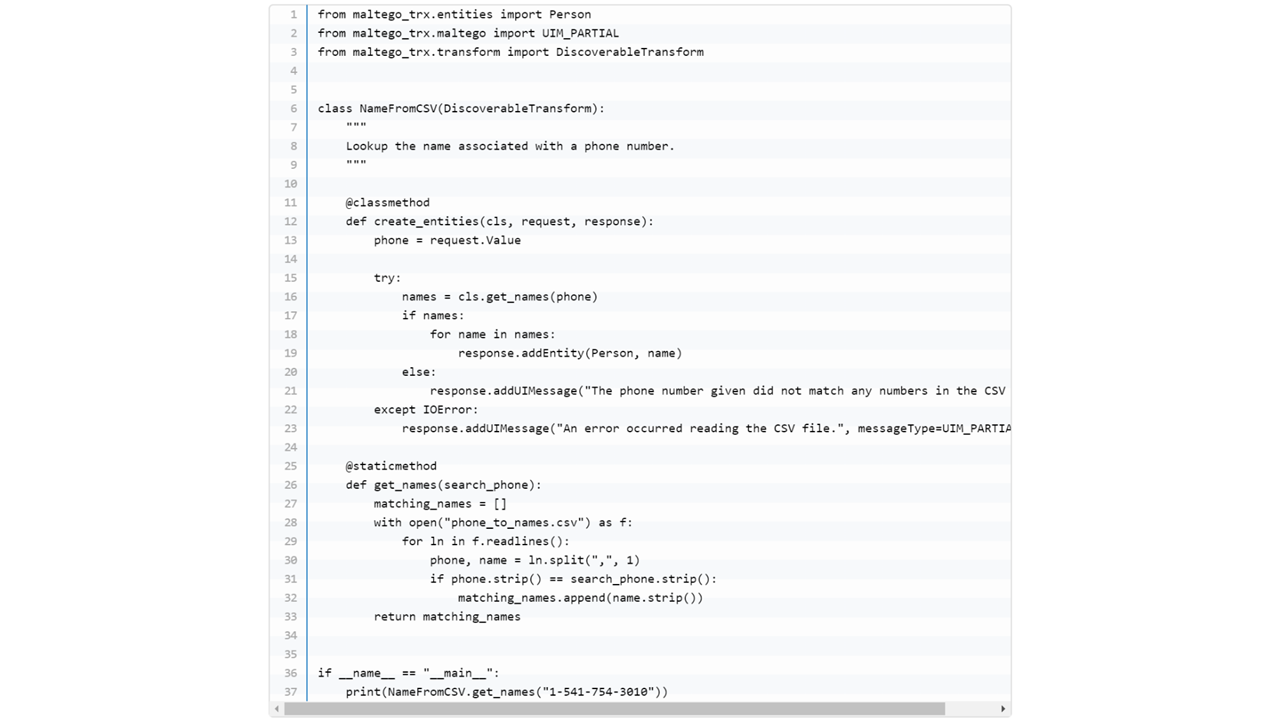
There are several methods of writing Maltego Transforms (a list of them are available here), however, in this example, we will stick to our Maltego TRX Library for Transform writing. The TRX Library provides the advantage of allowing for the same code to be used for writing Local and TDS Transforms.
One example of a Transform’s final code is shown below. The Product Entity can also be easily added during the Transform writing process by updating the “create Entities” method of the Transform class.
Worry not, this whole process is easy enough and, in case this is your first time, you will be able to find a detailed tutorial on how to write your own Maltego Transforms and add them to the Maltego Desktop Client in our documentation section. To see how, click here.
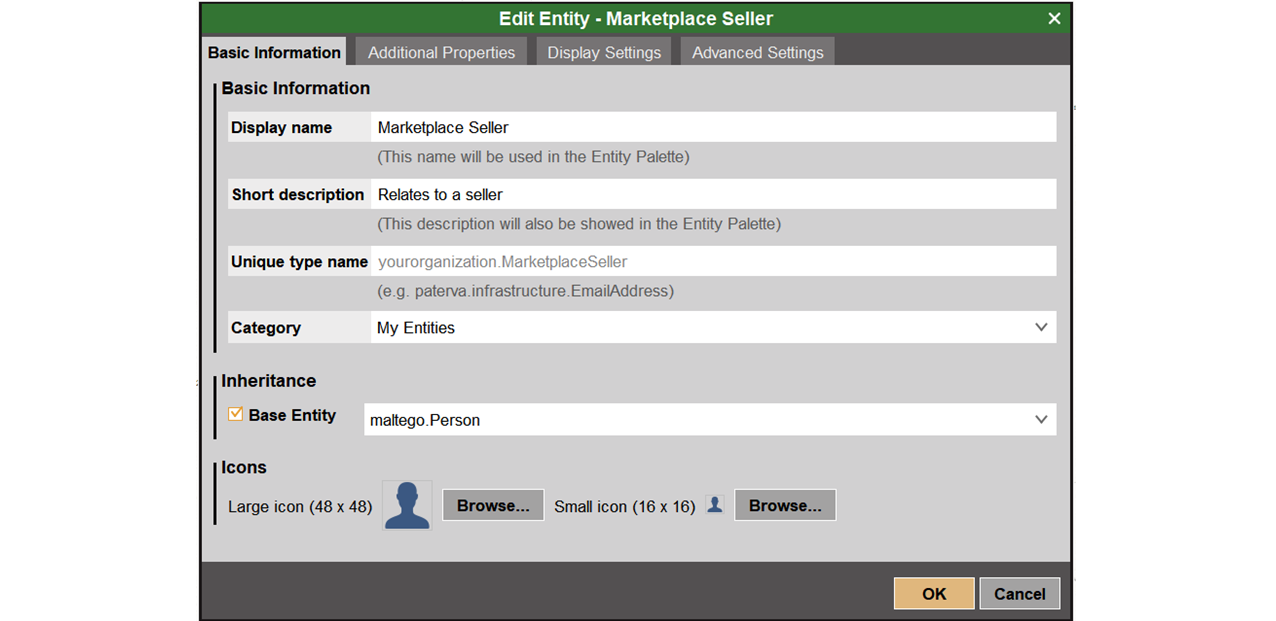
The properties of the Entities we have created (as well as any other Entity) can be easily edited directly from within the Maltego Client. All we need to do is select the Entities Tab, click on the Manage Entities option to open the Entity Manager pop-up window, and then on the ellipsis icon at the right end of the Entity we want to edit for the edit menu.
Investigating Stolen Merchandises from E-Commerce Warehouses 🔗︎
Once we have our Transforms up and running, we can start our Maltego investigation.
*Fair warning: the data you will see is the result of a simulation with a dummy database, we do not have access to a warehouse or its data.
*A reminder: The Transforms you are about to see are not available as a Hub item on the Maltego Transform Hub, they have been written for this specific purpose.
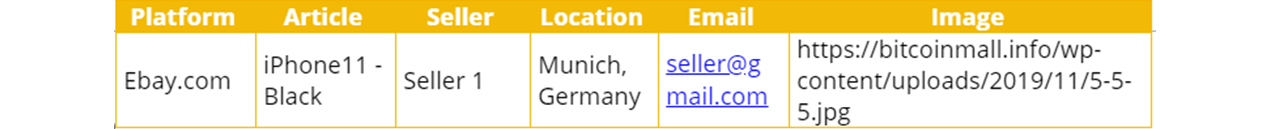
The structure of the CSV file we used for the dummy data is as follows:
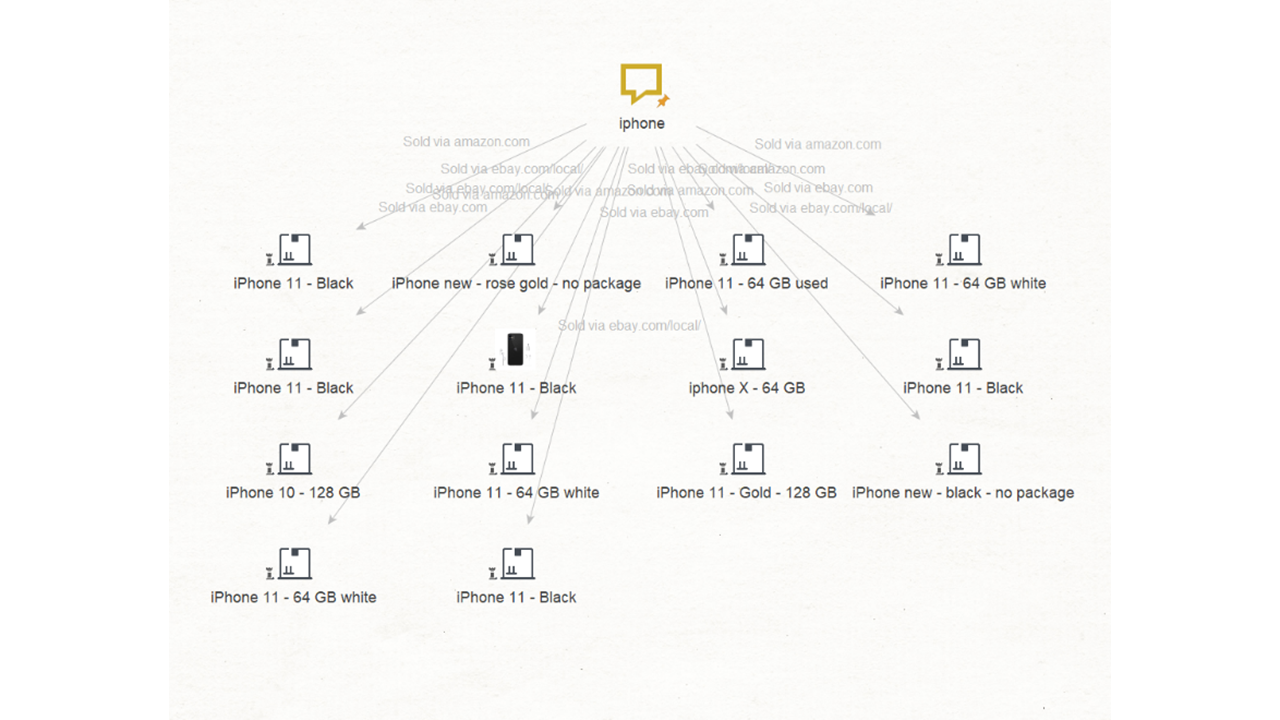
According to our inventory reports, one of the products that has been going missing is the newest iPhone. Our first step will be to drag a Phrase Entity from our Entity Palette, drop it into our working area and change its name to “iPhone”, and then run the “To Products” Transform.
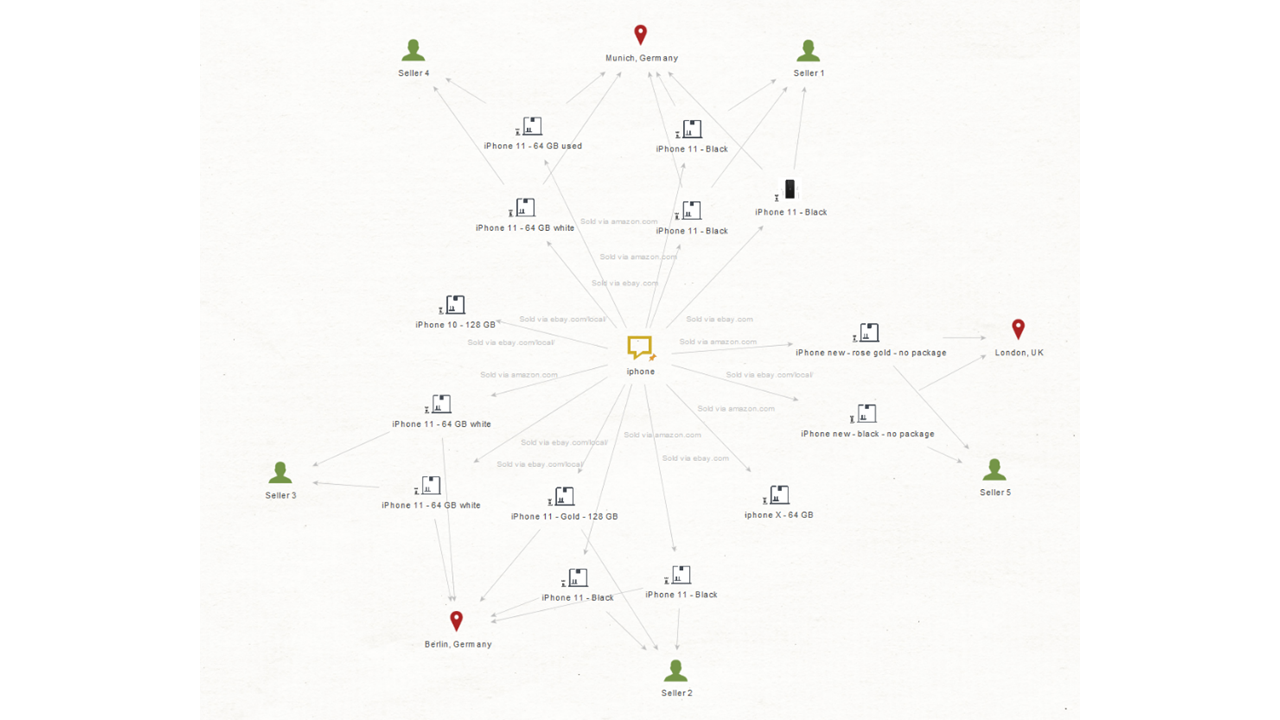
Here we can see the “sold via” feature displayed on the Entity link which shows us which products matching the description of our missing inventory are being sold off on marketplaces.
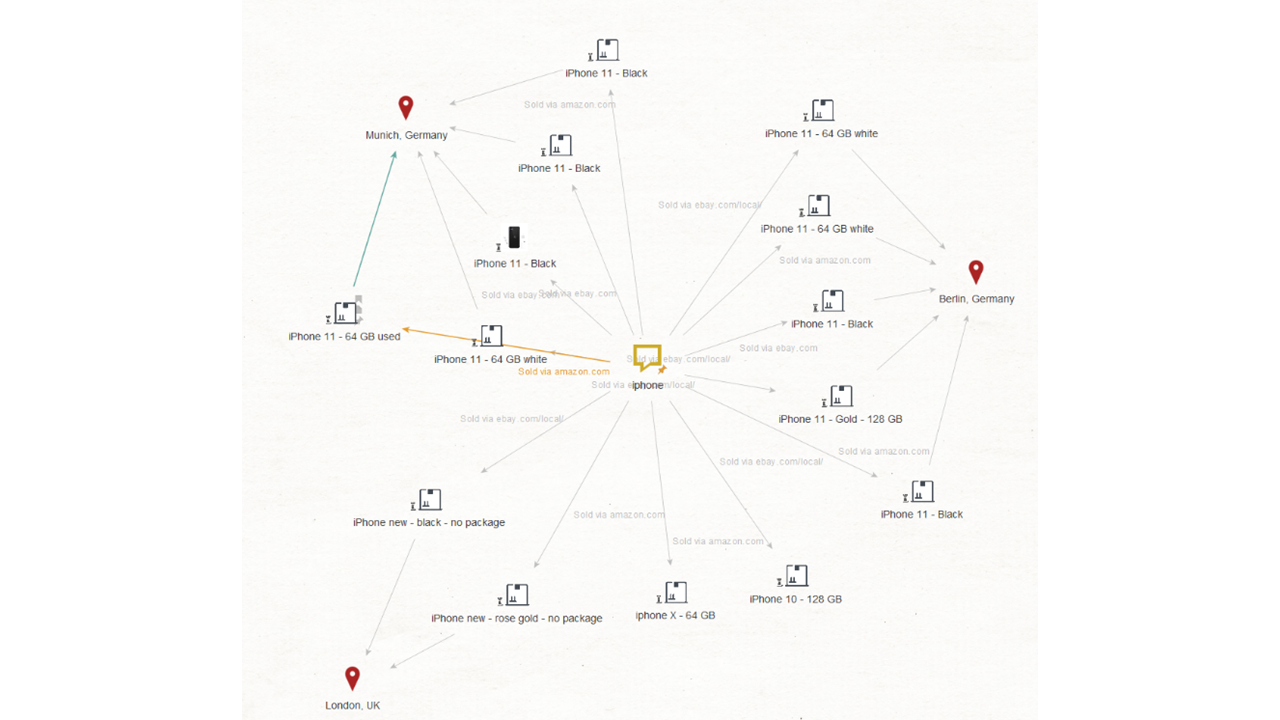
We want to proceed with the attribution part of our investigation, so we select the “iPhone 11” and “iPhone new” Entities and run a “To Sold Via” Transform to discover which specific websites are carrying these offers.
We learn that the offers are coming from 3 locations: Munich and Berlin in Germany, and London in the UK. We now want to retrieve information on the merchants and for that we select again the Product Entities and run a “To Seller” Transform.
Remember, the results will point us to suspicious merchants, but this will not be an absolute confirmation of guilt.
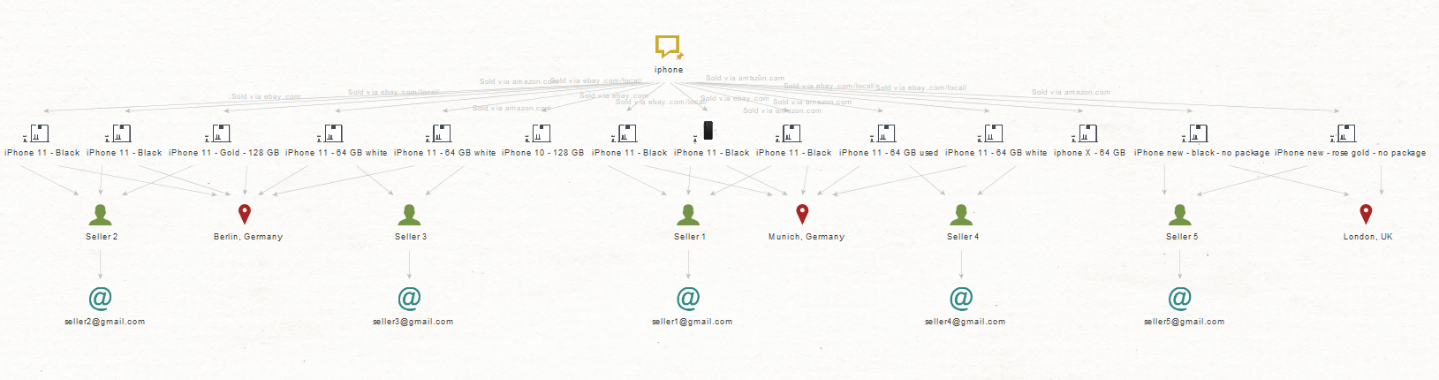
We find out that the iPhones being sold in Germany come from 4 different merchants and that the ones in the UK come from a single merchant. What we want to do now is retrieve the email addresses associated with each of the merchants. Therefore, we proceed to select the “Seller” Entities and run a “To Seller Email” Transform.
Now we have obtained the email addresses attached to the suspicious merchants. Given that this was a simulation, for this example we cannot pivot into Transforms for social media or person-of-interest profiling Transforms to enrich and contextualize the email addresses we just obtained, but we fully recommend it as a further step.
Another option would be to write a Transform that would allow us to pivot from the merchant back to other products on offer by this merchant or to their available merchant ratings – this would allow us to gain better context and decide whether or not the product being offered is in fact a stolen one.
Lastly, please remember this was only a small example and, as you can imagine, Maltego presents a multitude of options available for investigators who are looking for ways to tackle insider threats and the resulting offering of stolen items in online marketplaces.
If this use case was of interest to you and your team or you have any questions, do not hesitate to write to us at support@maltego.com. Follow us on Twitter and LinkedIn or subscribe to our email newsletter to stay tuned for new use cases, product updates and news!