As COVID-19 continues to spread, hackers are taking advantage of the pandemic to launch COVID-19 related cyber-attacks. These attacks come in various forms, such as phishing, scam websites, viruses, ransomware and many others.
In response, cybersecurity experts have come together to fight back against threat actors. One such group, the COVID-19 Cyber Threat Coalition (CTC), is a global volunteer community dedicated to stopping cybercriminals. The group also has an Open Threat Exchange Threat Intel feed. CTC publishes threat intelligence datasets in two forms: vetted (CTC verified threat intel data) and unvetted (unexamined threat intel data). The datasets contain COVID-19 related observables, each category contains 4 Indicators of Compromises, namely: IPs, Hashes, Domains and URLs. Threat intelligence analysis is a complex process that involves collection and analysis of information related to cyberthreats. In this article, using the CTC data as an example, we look at how Maltego enables investigators, forensics experts and cybersecurity researchers to take full advantage of the extensive OSINT data integrations available in Maltego Standard Transforms to enrich threat intel data. We also give a glimpse into how our data partners can help take such an investigation to the next level.
Case Study 🔗︎
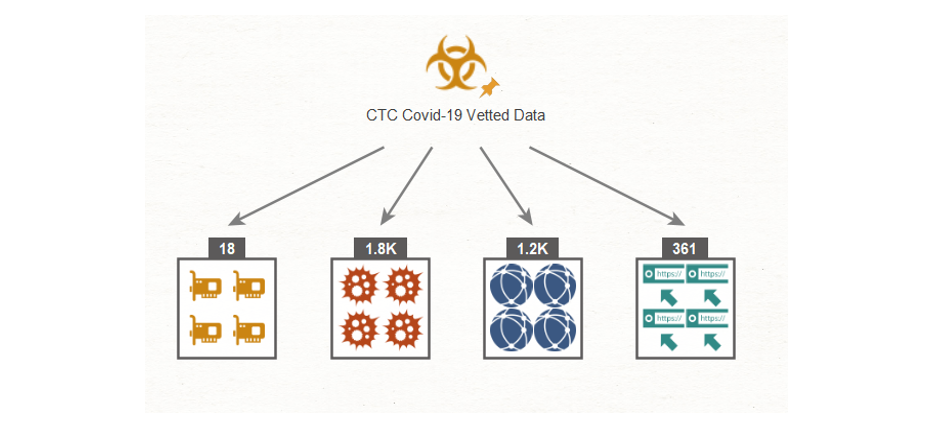
At the time of writing, the CTC vetted data points were 361 URLs, 1200 Domains, 1800 Hashes and 18 IP Addresses as shown below.
To follow along, you can download the domain data and import it into Maltego.
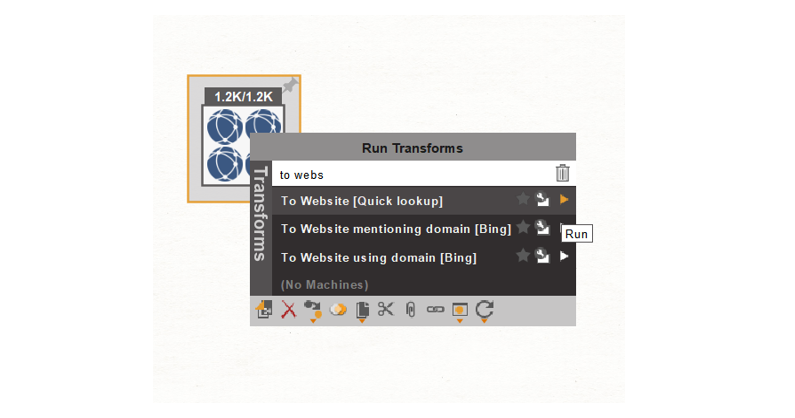
Let’s take a look and see if these domains intersect, meaning, whether they share infrastructure or other significant features. First, we copy the Domain Entities from above to a new graph, select all of them and run the “To Website [Quick Lookup]” Transform, which prefixes “www” to the domain and checks if there is a record in the DNS configuration.
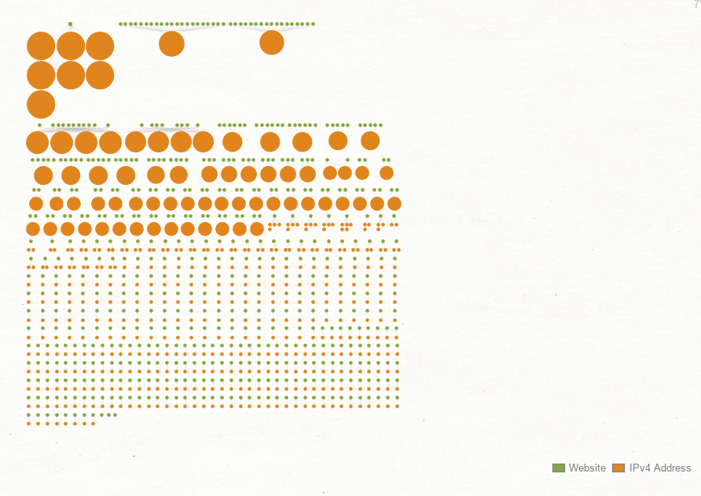
We can see out of the approximately 1.2k domains we had in our dataset that 560 do not contain a “www” DNS record. Now, these domains could have already been shut down, or they could be registered for legitimate use. On the other hand, they could also serve as tools in a threat actors’ arsenal.
To remove data we do not need, we delete all the Domain Entities from our graph. Next, we run the “To IP Address [DNS]” Transform on the remaining Website Entities. This Transform resolves each DNS Name (in this case a website) to an IP Address.
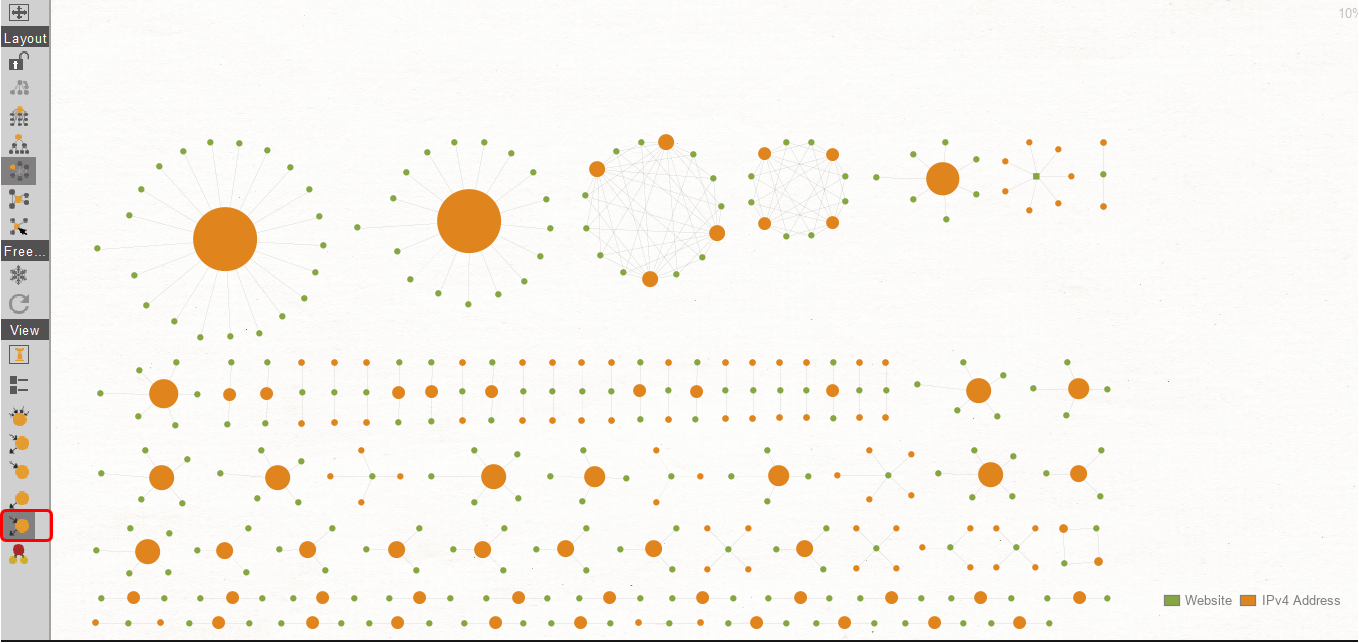
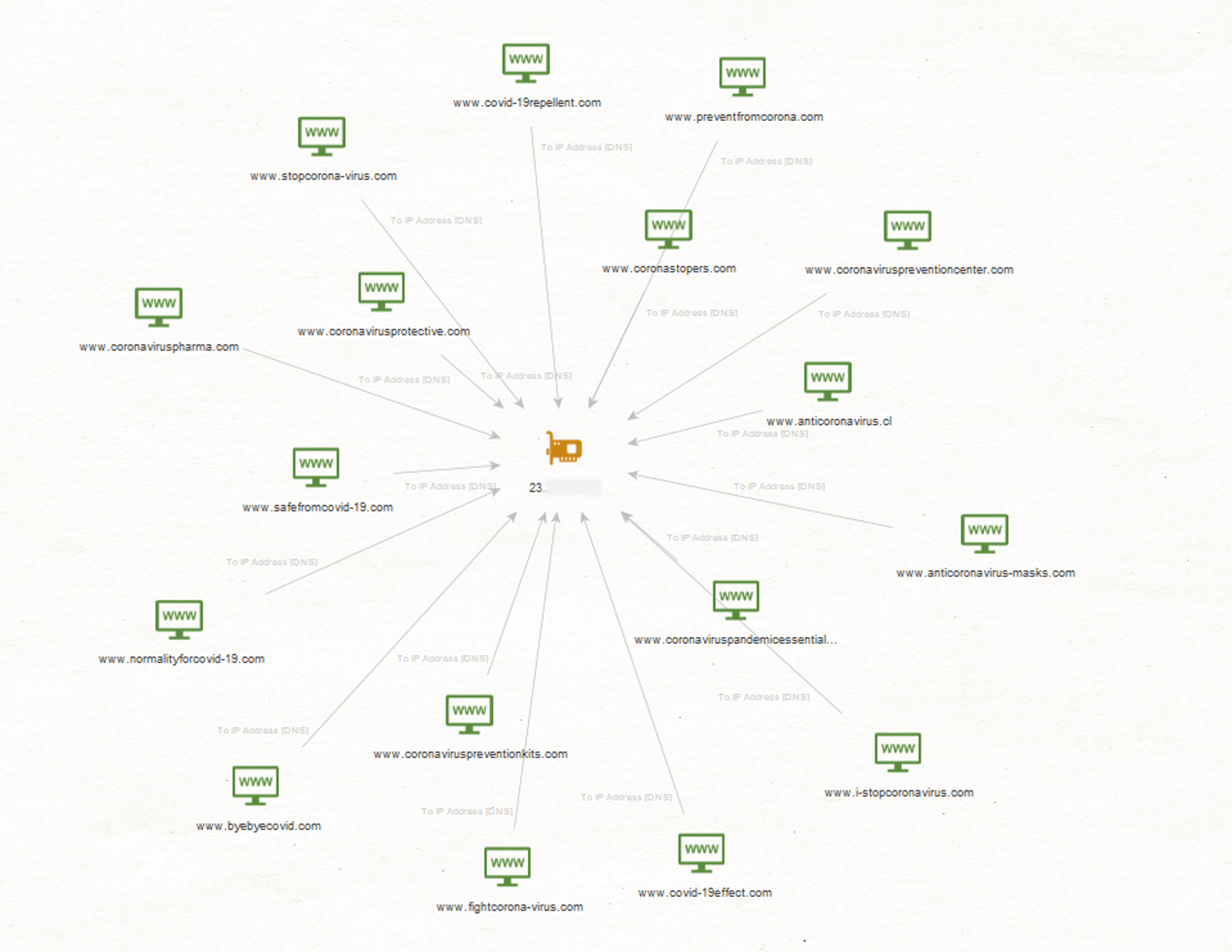
In the default Block layout, it can be hard to see relationships between Entities clearly. Let’s switch to the Organic view and select Ball size by Rank under the View menu on the left side – This arranges the Entities by the number of its links and its neighbors’ links as shown below.
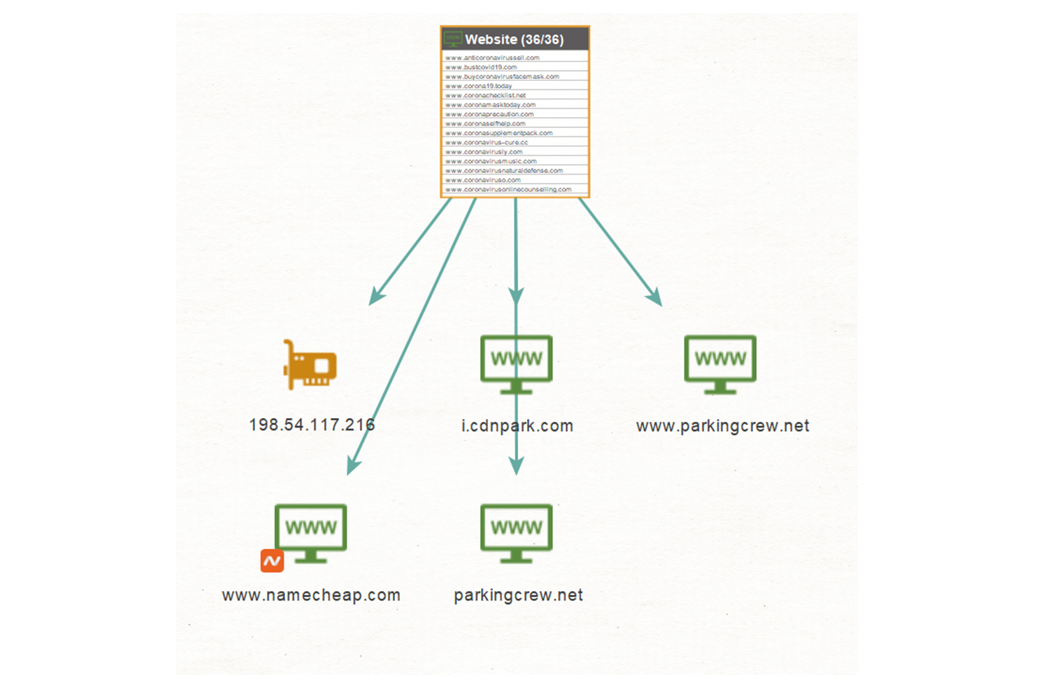
As we can see, Entities with the highest number of links are prominently visible which allows us to quickly pick out points of interest. The orange circles on the graph indicate IP addresses with multiple websites (green circles) pointing to them, making these great candidates for further investigation.
Taking the largest collection of Website Entities pointing to one orange IP Entity, we select the collection, and copy those to a new graph. To see where these websites link out to, we run the “Mirror External links Found” Transform.
We see these domains are parked at Namecheap hosting, most likely with the intention to redirect interested parties to buy the domains there. We can shift our focus to another IP Address Entity with multiple domains linking to it.
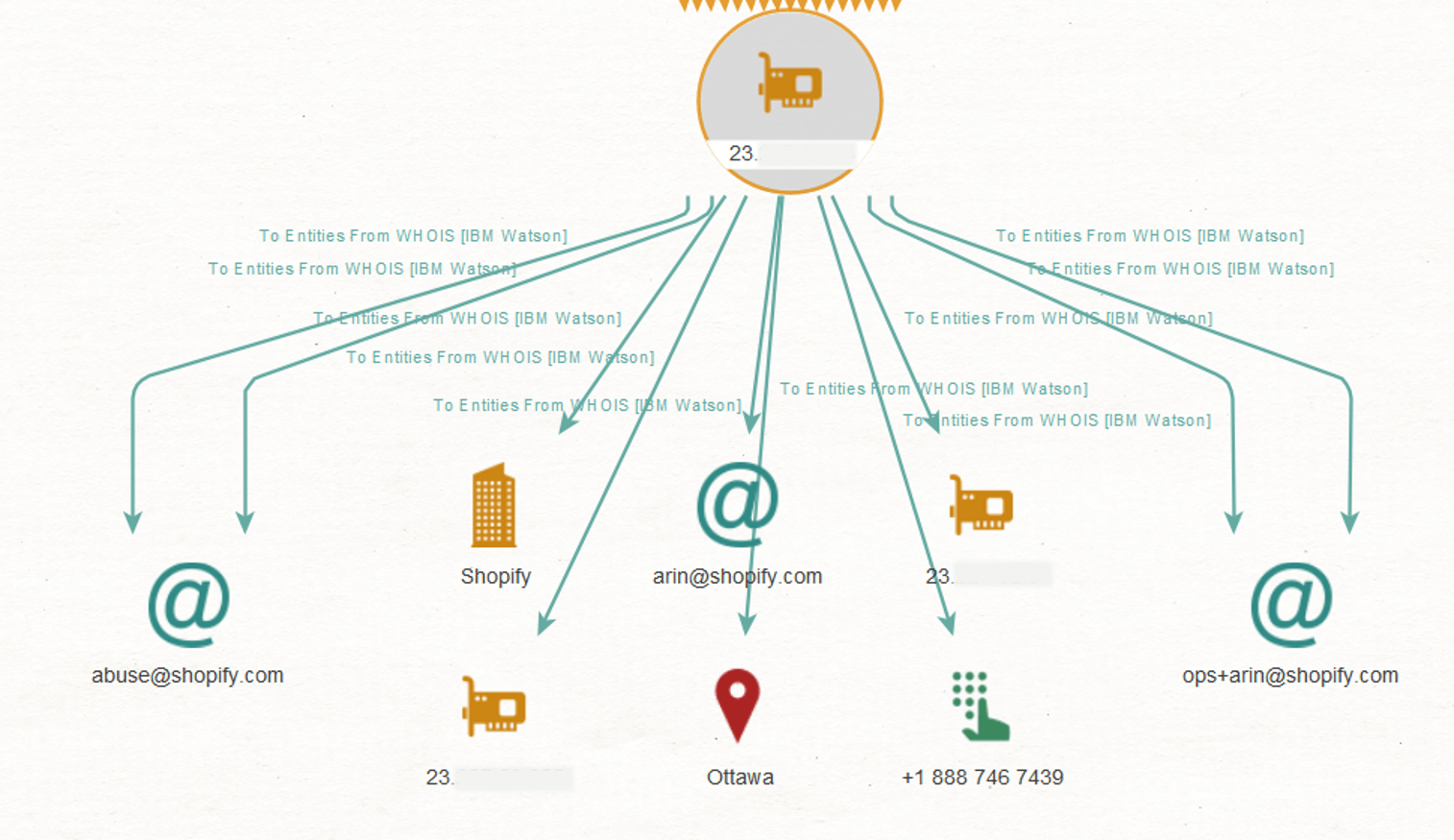
Taking another investigative angle, let us find out who owns the IP Address. We run the “To entities From WHOIS [IBM Watson]” Transform to query the organization assigned to the address. This shows us the IP address belongs to Shopify, which leads us to conclude that these websites are most likely shops hosted on the e-commerce platform.
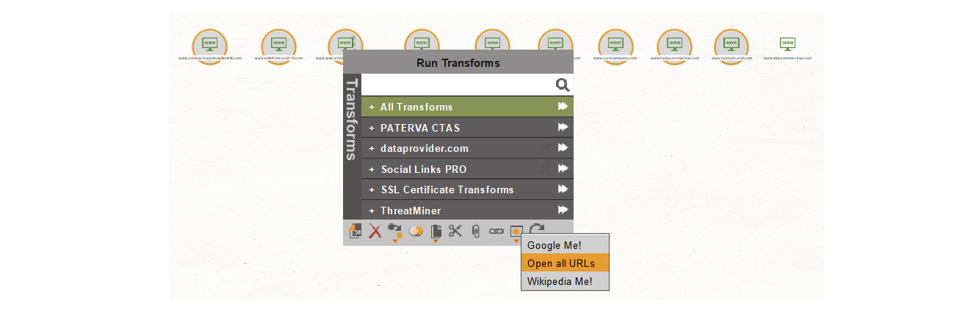
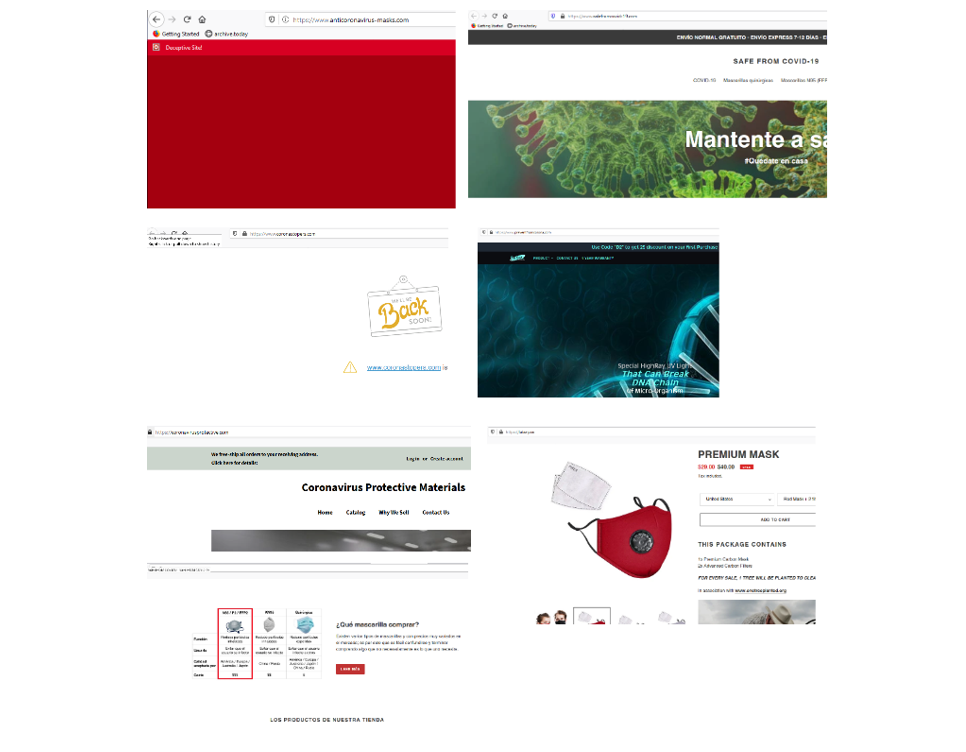
The quickest way to visually see what these shops look like on a browser in Maltego is through Actions. We simply select all the Website Entities, click the Actions Icon and select Open all URLs. This opens all the websites in the default browser set in the Maltego client settings.
Warning: Use this Action carefully, as you may wind up visiting malicious websites. We recommend opening each link individually in a secure sandbox/VM.
Most of these websites look like scams purporting to sell face masks, as previously seen in multiple COVID-19 related scams. Though these websites claim to sell protective materials – the shops do not have traceable contact details.
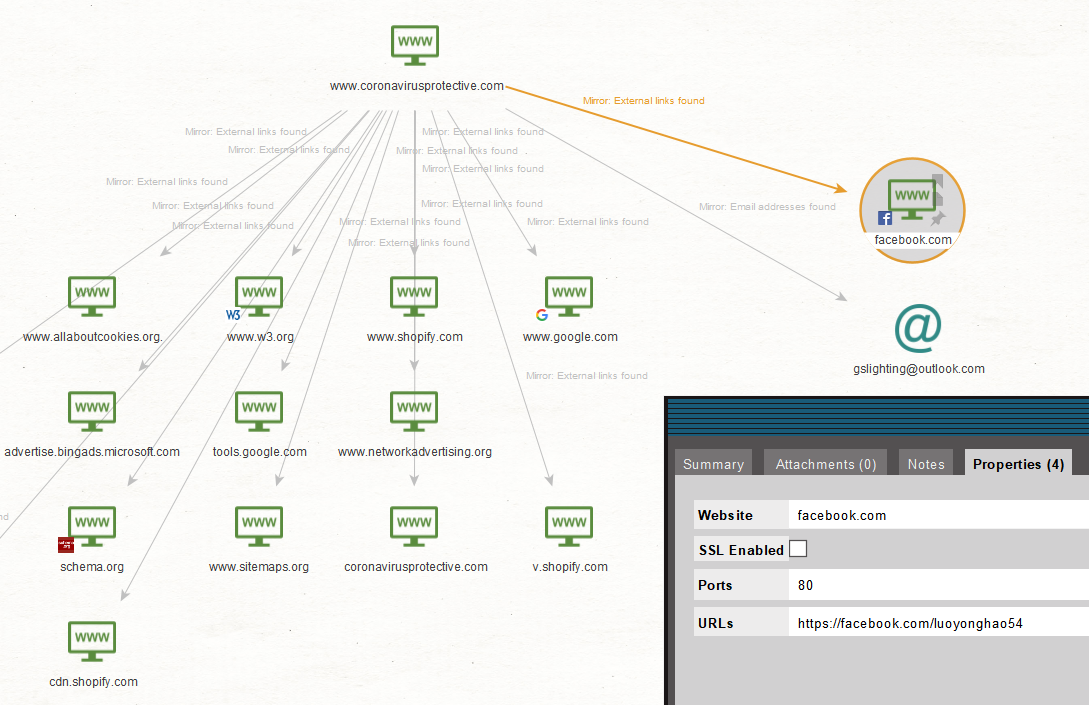
At this point, we would like to explore each Website Entity individually to see if there is any helpful information that we can glean to aid the investigation. On each website, we run the “Mirror: External links found” and “Mirror: Email Addresses found” Transforms: One website that contained personal identifiable information is coronavirusprotective[.]com, one of its outgoing links points to a Facebook profile and an email address.
A look at the Facebook profile shows it was opened in 2017 but had no activity until 31st March 2020. On the profile there is a video pointing to a YouTube channel that has one COVID-19 related video posted on the 4th April 2020 under the same name as the Facebook account.
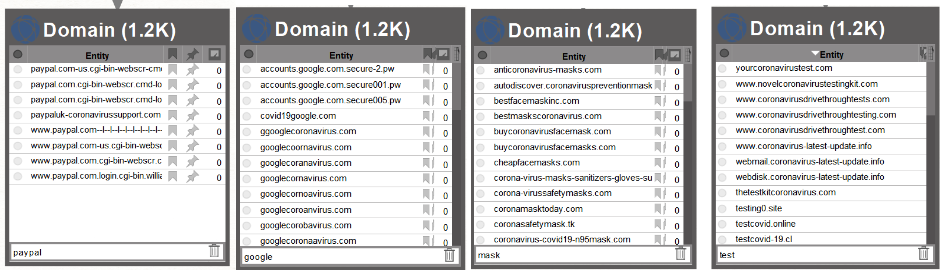
Other important features that can be used in such an investigation is the ability to filter out Entities of interest. For instance, in the CTC domain dataset, we can filter out interesting names such as “masks”, Google”, “PayPal”, or “test”, as shown below:
This can be a helpful starting point in investigating the Tactics, Techniques, Procedures (TTPs) used by threat actors related to a particular brand, topic or company.
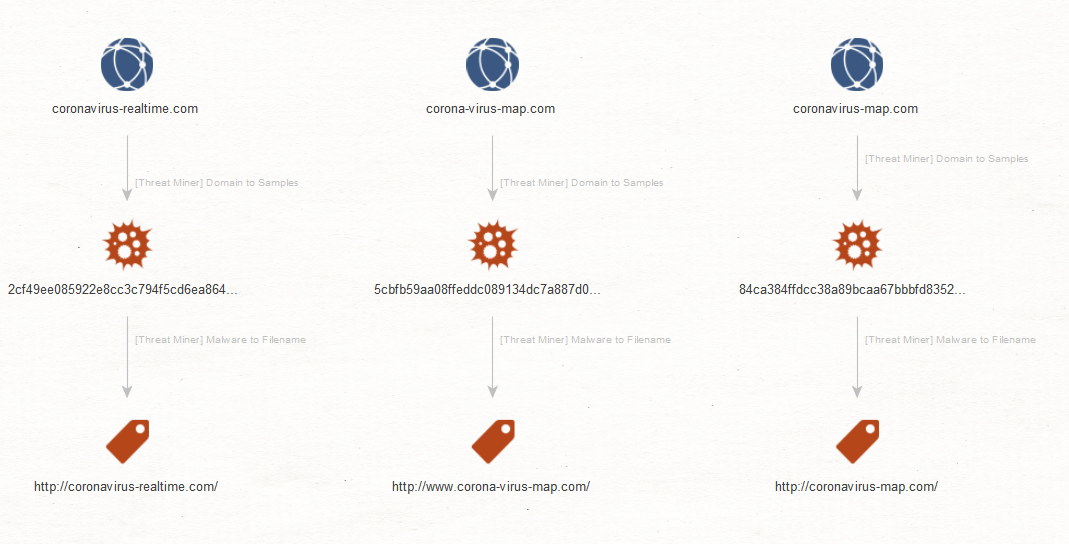
Lastly, it is possible to leverage the Transforms of Maltego’s data partners, which can be installed via the Transform Hub. For example, ThreatMiner, a data partner that focuses on threat intelligence and provides historical information on indicators of compromise (IOC) such as domains, IP address and malware samples.
After installing the ThreatMiner Hub item, we run the “[Threat Miner] Domain to Samples” Transform to find malware hashes that have been observed on the requested Domain Entity. After that we get the malware names through “[Threat Miner] Malware to Filename” Transform. These hashes and filenames could be used for further investigation or to check against other threat intelligence tooling and datasets within organizations.
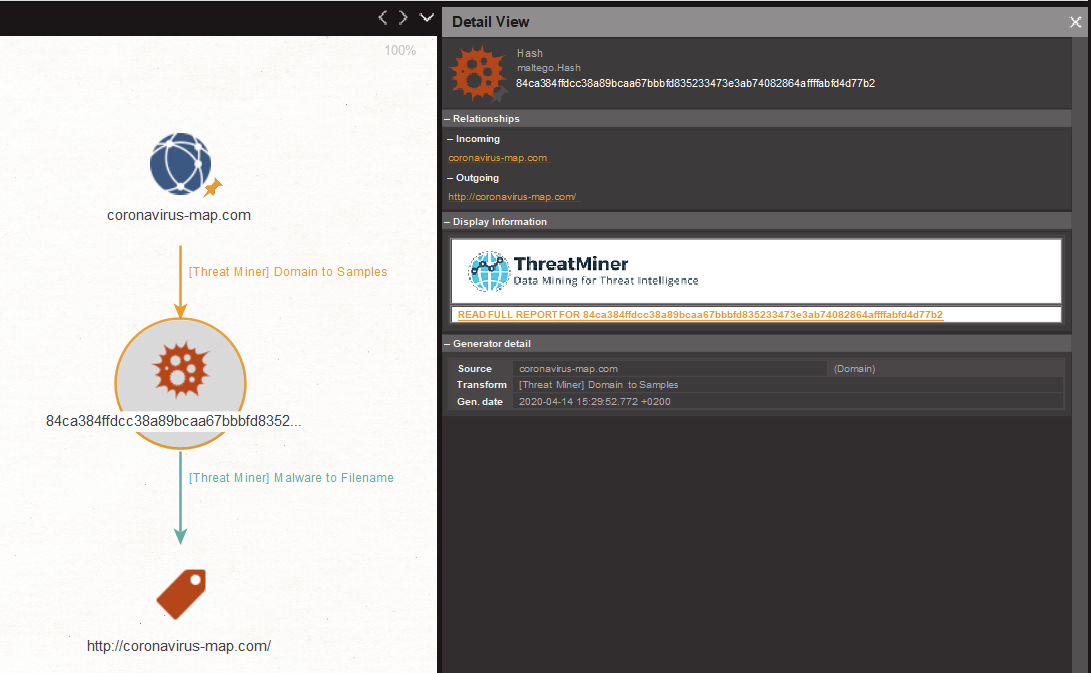
To view the full report on ThreatMiner, let’s select a Hash Entity on the graph. Then in the Detail View on the right side of the Maltego, click the ThreatMiner external link, as shown below.
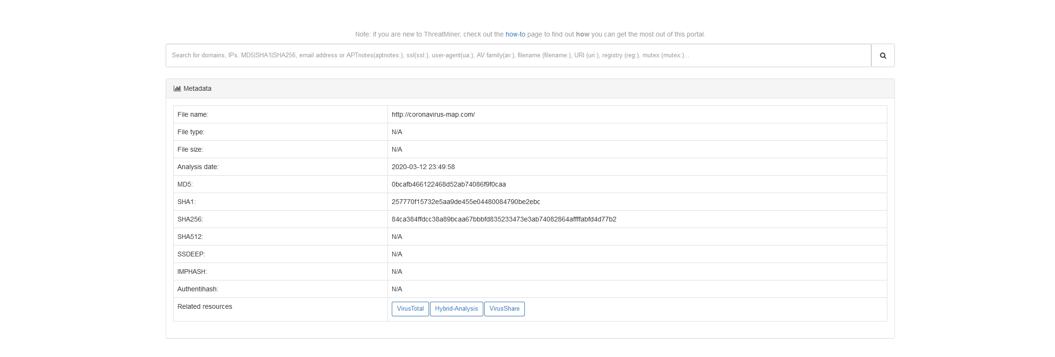
On the ThreatMiner website we can see various antivirus vendor reports on the malware sample, which provide more useful information related to the sample.
We hope this case study was instructive in showing how Maltego can be leveraged to simplify and accelerate cyber threat intelligence investigation and research.
We applaud the efforts of the team at Covid-19 Cyber Threat Coalition. It is wonderful and inspiring to see communities innovatively coming together in times of crisis to help each other!
We are currently accepting applications for a 2-month free Maltego commercial license for investigators combating challenges posed by COVID-19. To apply, simply complete this form.
We would love to hear from you! If you have a dataset or data you wish to integrate into Maltego, please get in touch with us using this form.