This article focuses on campaigns which are attributed to the TA505 Threat Actor group and their methods, and how Maltego can be used to investigate them. But first, let us talk about types of threat groups that have achieved notoriety and what makes them dangerous.
What Are Advanced Persistent Threats (APTs)? 🔗︎
Previously used within the telecom sector, the term Advanced Persistent Threat (APT) has been in use within the cybersecurity community for over a decade. It generally refers to stealthy, non-opportunistic hacker groups that carry out highly customized, coordinated attacks with the goal of spying or stealing information and even committing ransomware.
APTs are generally perceived as state-sponsored groups, which have been known to originate from nations such as China, Russia or Vietnam, but this is not always the case. In fact, they can originate pretty much anywhere and not have a state affiliation, and instead dedicating their efforts to endeavors such as corporate espionage.
APT groups such as Lazarus and Red Apollo have become very popular. These attackers are becoming increasingly powerful and creative with each passing day.
What Makes APT Groups Dangerous? 🔗︎
These groups play the long game and have displayed a rate of success that makes them more dangerous compared to other threat types. The word “persistent” does not stand for them overrunning their target with constant, automated attacks and malware updates, but for maintaining long-term access to it. In fact, APTs often go undetected for months—even years—during which they have access to sensitive data.
Access is usually gained via malware as a result of social engineering, spear phishing, spamming, or other similar techniques. After gaining access, the APT group attempts to establish a foothold within the network by installing Remote Access Trojan (RATs) and creating new backdoors and tunnels.
Achieving this will allow the APT group to continue its propagation within the infrastructure undetected. Propagation will be done via privilege escalation, further infrastructure reconnaissance, and lateral movements within the infrastructure. The longer the APT remains undetected, the better it will propagate to accomplish its ultimate goal.
Using Maltego to Investigate Threat Actor Campaigns 🔗︎
There is no one-for-all solution against advanced persistent groups. In fact, their very nature makes them quite difficult to detect. However, in combination with other tools, Maltego can help analysts investigate these threats by mapping IOCs with publicly available security feeds, infrastructure footprints, and malware investigations, amongst others. In doing so, it may be possible to update system policies and better ensure organizational cyber resilience.
This article takes a look at a currently very popular group known as TA505, as well as the different steps that can be taken in Maltego to further enhance the information already available.
What is TA505? 🔗︎
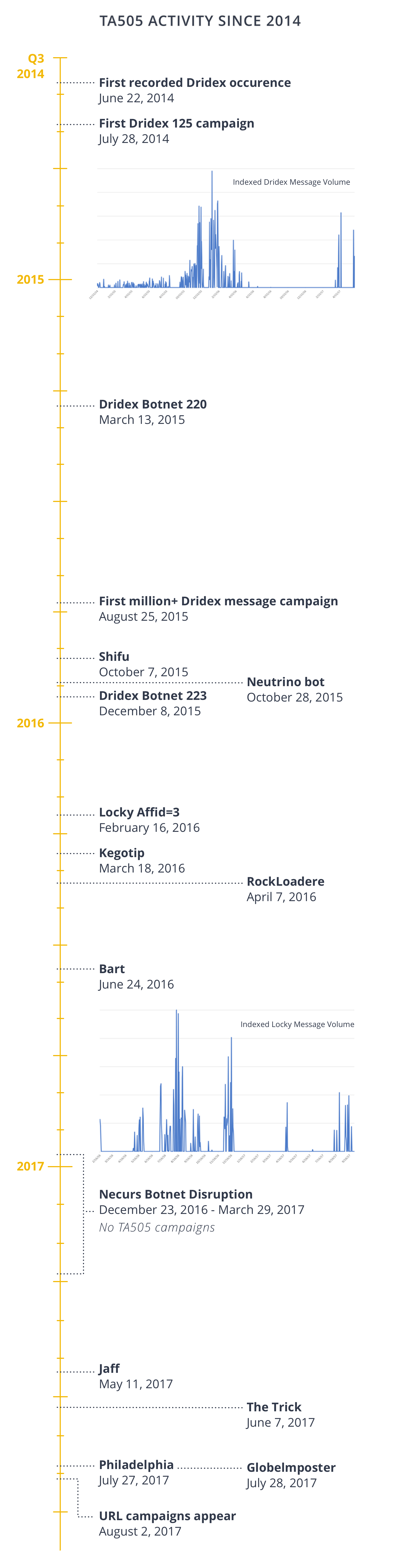
According to the definition by MITRE ATT&CK, “TA505 is a financially motivated threat group that has been active since at least 2014. The group is known for frequently changing malware and driving global trends in criminal malware distribution.” The image below shows a timeline of TA505’s activity between 2014 and 2017.
The Techniques Used by TA505 🔗︎
TA505 has taken to the stage again in 2020 with new attack techniques designed to take advantage of vulnerabilities caused by the coronavirus pandemic. This group has been known for using credential phishing, malicious attachments and links, business email compromise (BEC), fake landing pages, downloaders, spam, and malware, amongst other malicious activities and techniques.
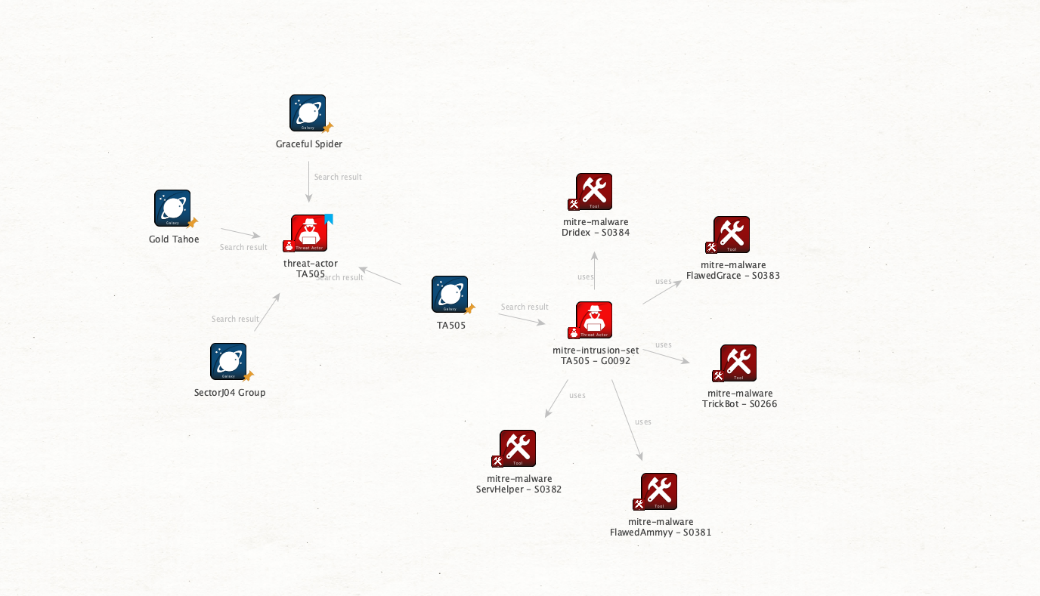
Now, leveraging the latest developments around the current pandemic, TA505 has used coronavirus lures from the “Locky ransomware” and the “Dridex banking Trojan” attacks (Proofpoint, 2020). The TA505 group specifically targets finance, healthcare, manufacturing, and pharmaceutical industries. Additionally, it is known to be associated with” Hive0065” (Mitre ATT&CK, 2019), “Graceful Spider”, “Sector J04 Group”, and “Gold Tahoe” (Malpedia, Frauenhofer Malware Identification Platform).
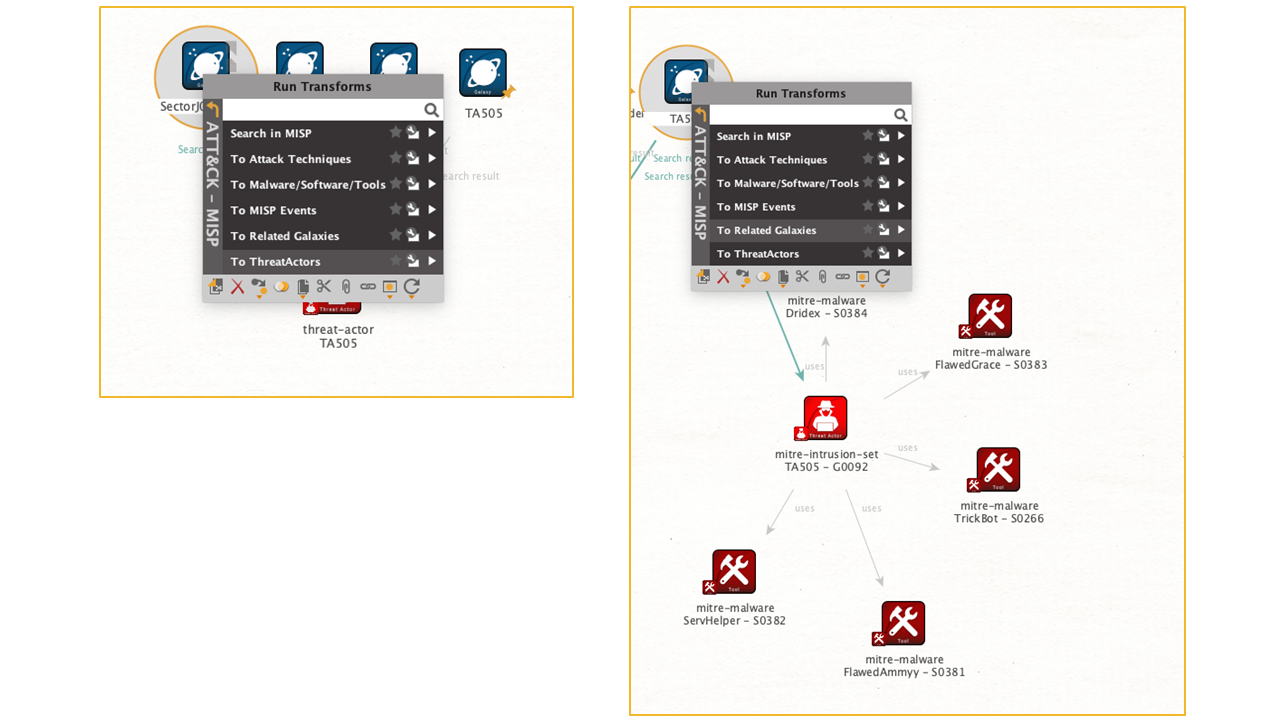
There are several techniques used by TA505. The full list of these techniques and software can be found at the Mitre ATT&CK threat actor group site. (Mitre ATT&CK, 2019). The images above shows the Maltego view in the Mitre ATT&CK Framework for the Actor Group.
An Example of a TA505 Campaign 🔗︎
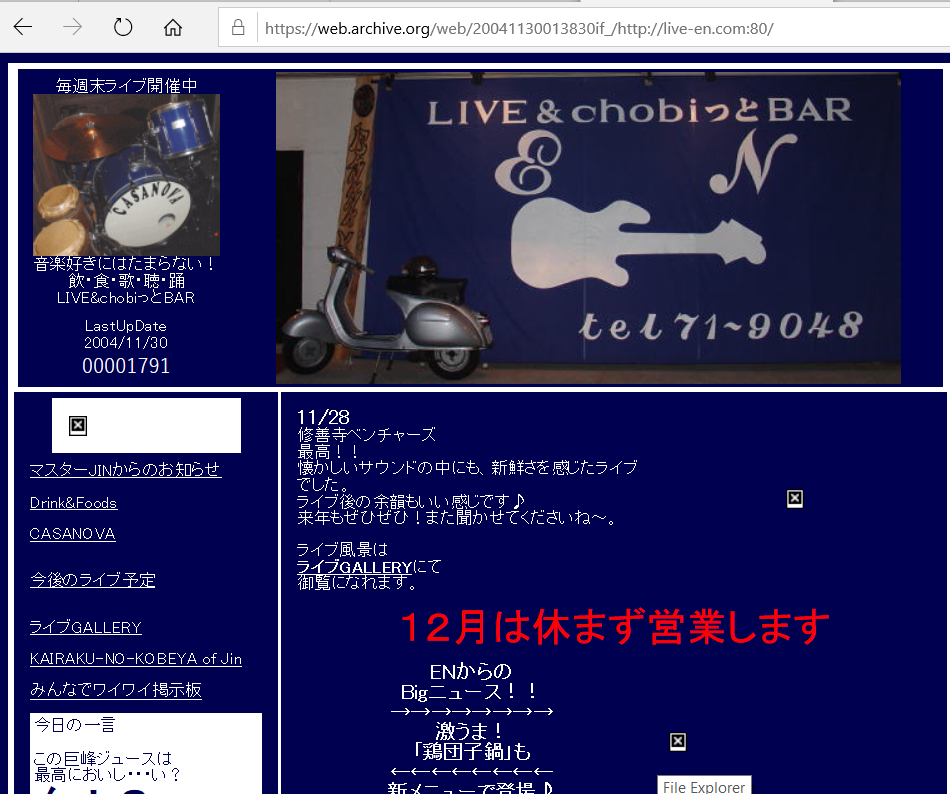
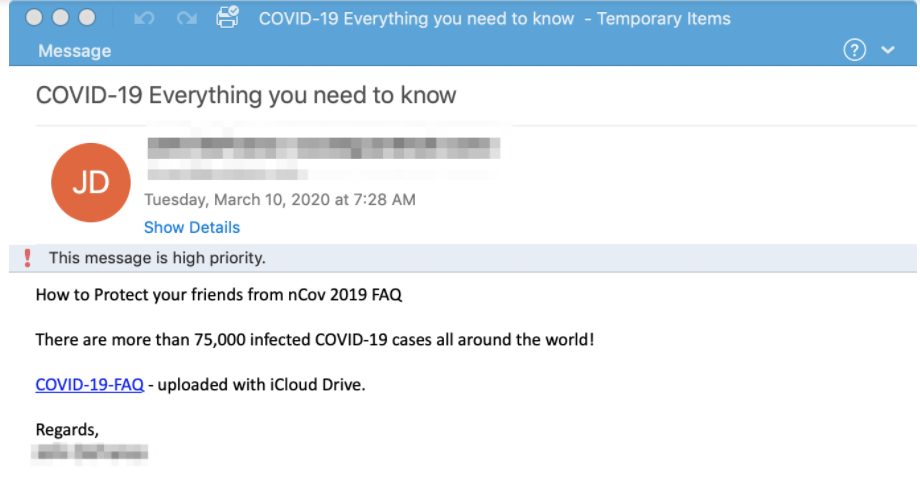
As most APT groups do, TA505 starts its attack with a phishing e-mail including a link to a malicious document. When the user open the link it directs to a site where a excel document can be downloaded. After a successful download and the user open the document (with macros enabled), the infection takes place through the embedded downloader, and the company’s IT systems are taken over little by little (see Resources [3] ). This scenario is illustrated below.
Individuals within the targeted industries need to be well-trained and aware of the dangers involved when dealing with phishing attacks. For this reason, institutions need to place great emphasis on end-user awareness training.
As you can see from the email example, the campaigns are designed to encourage people to click on the malicious link or attachment by appealing to them in a crisis situation with information that appears to be helpful and urgent. Now that we have identified a suspicious incident, we can investigate further and for this, we will use Maltego to find the Indicators of Compromises (IoCs) related to TA505.
Investigation of TA505 Domains in Maltego 🔗︎
In our investigation within Maltego, we focus on three main domains provided by Alienvault as well as a URL stated on Proofpoint’s research, as listed below:
- Filesharess[.]com
- Live-en[.]com
- See-back[.]com
- hxxp[:]//www[.]agt[.]net/~mnpicker/2jgmu9r/h9a6kn.html
The URL corresponds to the COVID 19 campaign.
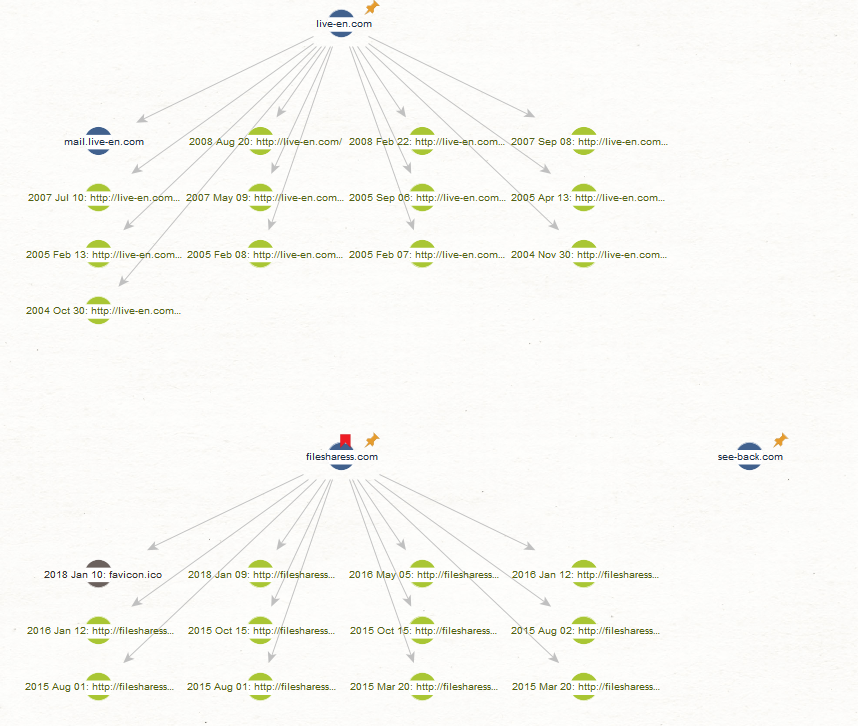
Discovering Associated URLs to TA505 Domains 🔗︎
To start the investigation, we first need to install the VirusTotal Public API Hub item. VirusTotal Public API Transforms allow users to discover and query information regarding observed artifacts including hashes, domains, URLs, and IP addresses. All Maltego users can acquire a free API key by registering on VirusTotal website here: https://www.virustotal.com/gui/join-us
Once we have acquired the API key, we will attempt to obtain the IP addresses of these TA505 domains by running the [VTPUB] Domain Resolutions Transform. The IP addresses can then be flagged and blocked to prevent future attacks.
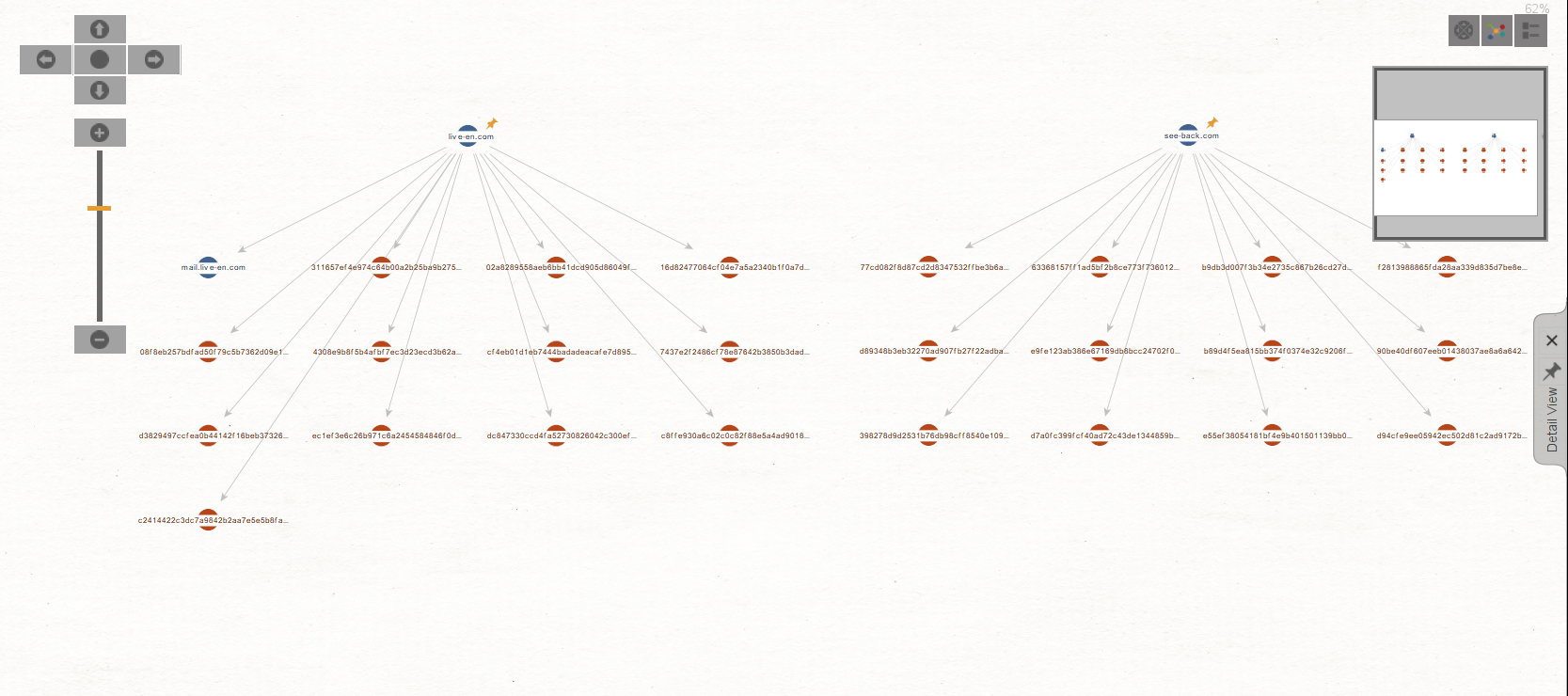
As shown in the image below, we ran the [VTPUB] Detected URLs Transform and discovered a number of URLs associated with or belonging to the TA505 group’s domains.
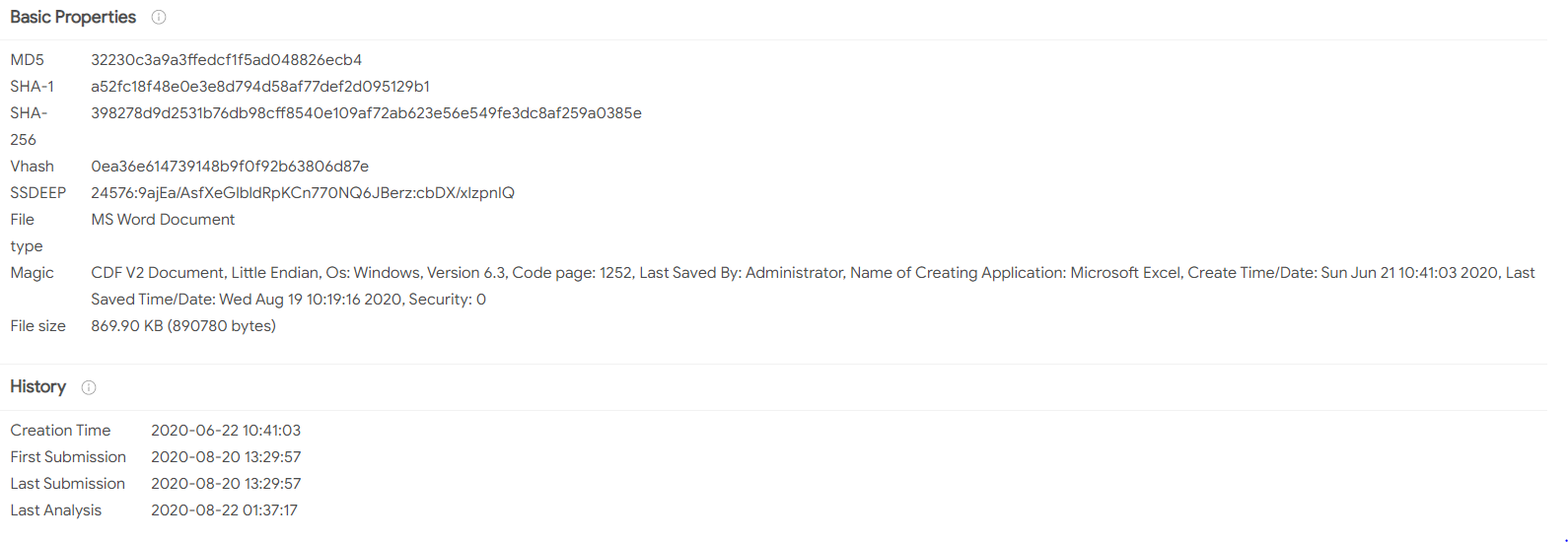
Identifying Relevant Hashes to Update System Security Policies 🔗︎
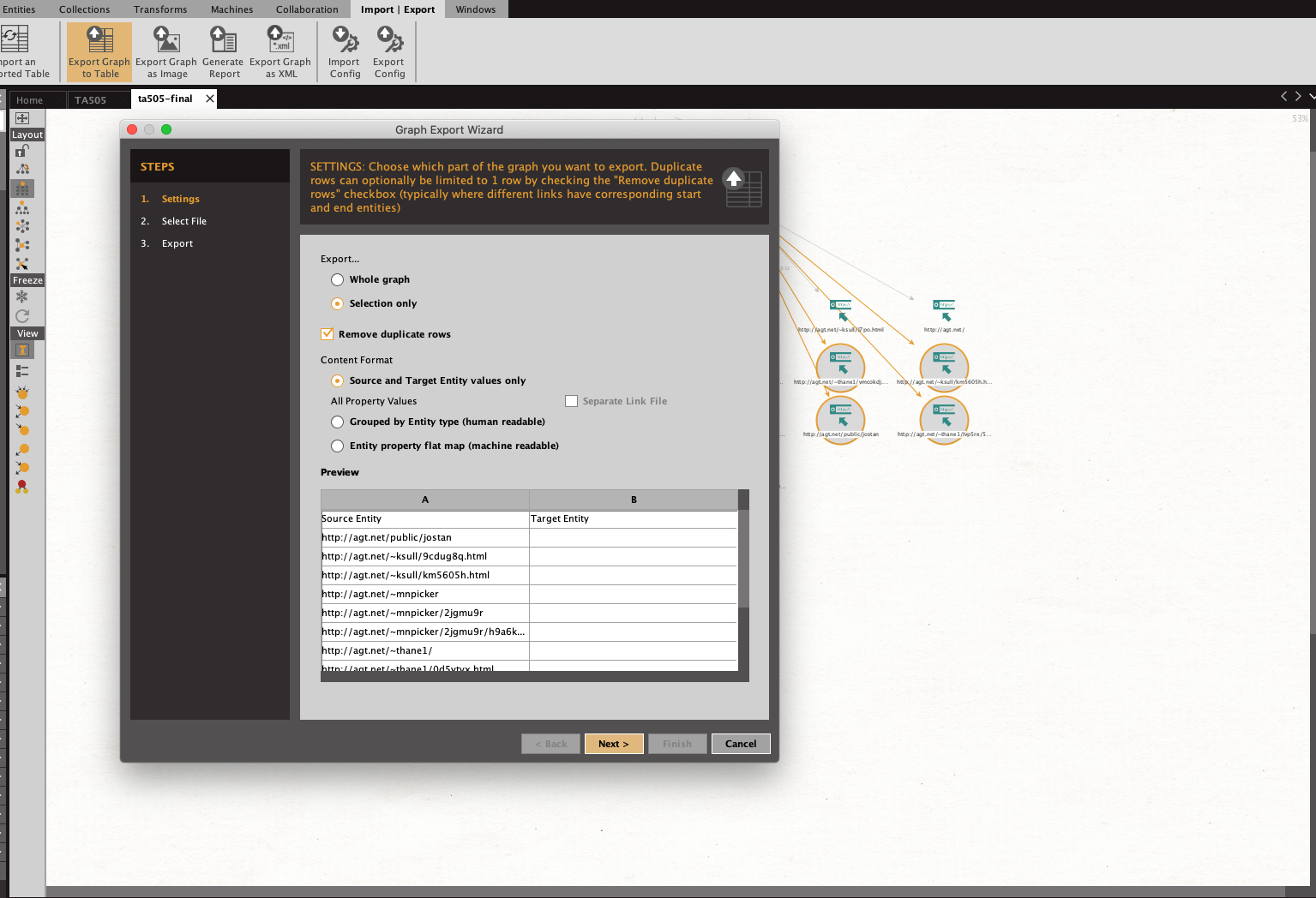
We are able to see the malwares related to this domain by using Maltego’s Hybrid-Analysis Hub item. The shown IOC’s (MD5 Hashes and URLs) can be used to add artifacts to update your systems’ security policies. This can be easily achieved with export functionality of Maltego.
Please note that malware can be modified, so this does not constitute a permanent fix for your detection rules. As you may know, detection rules in security systems run on a constant feedback loop dependent on results from previous event investigations.
Cross-Referencing Threat Intelligence in VirusTotal & Talos Intelligence 🔗︎
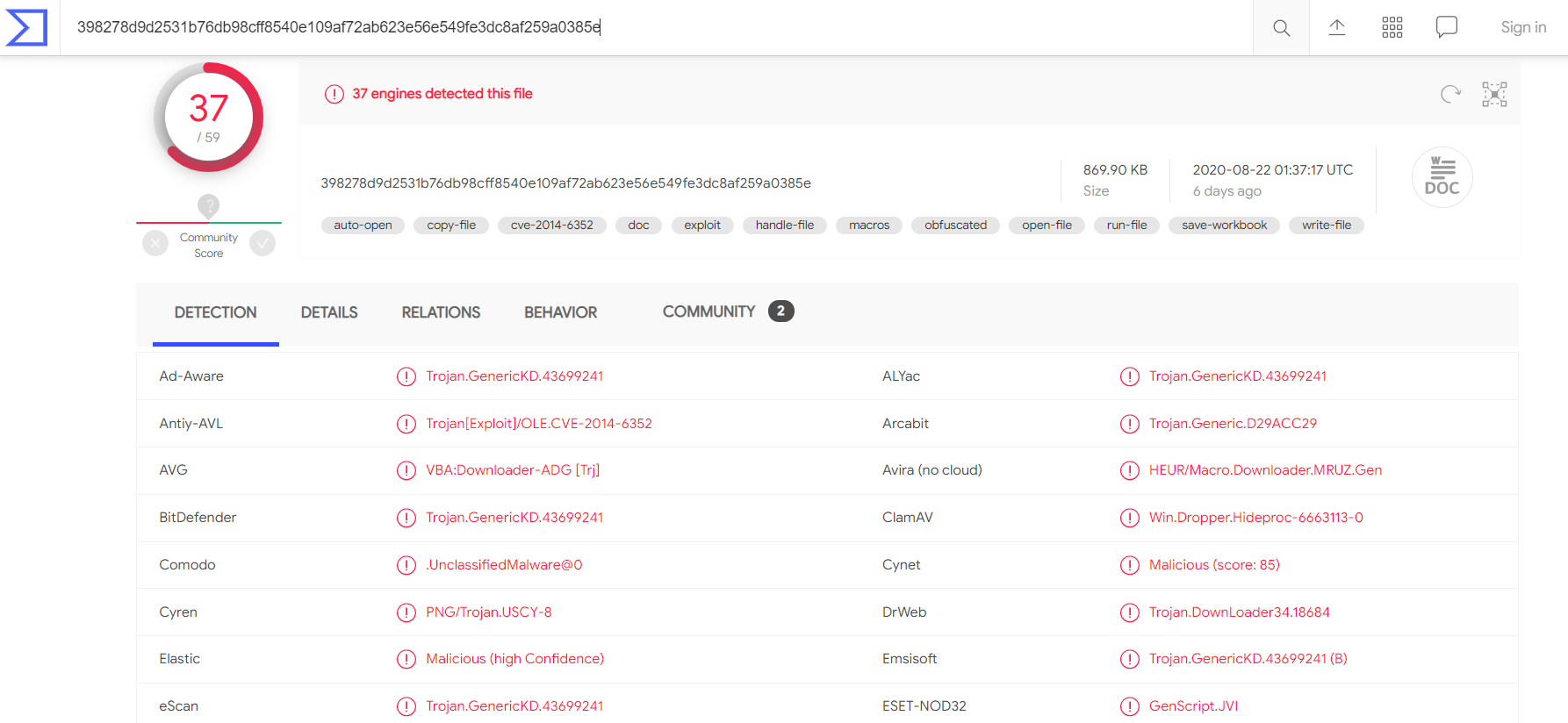
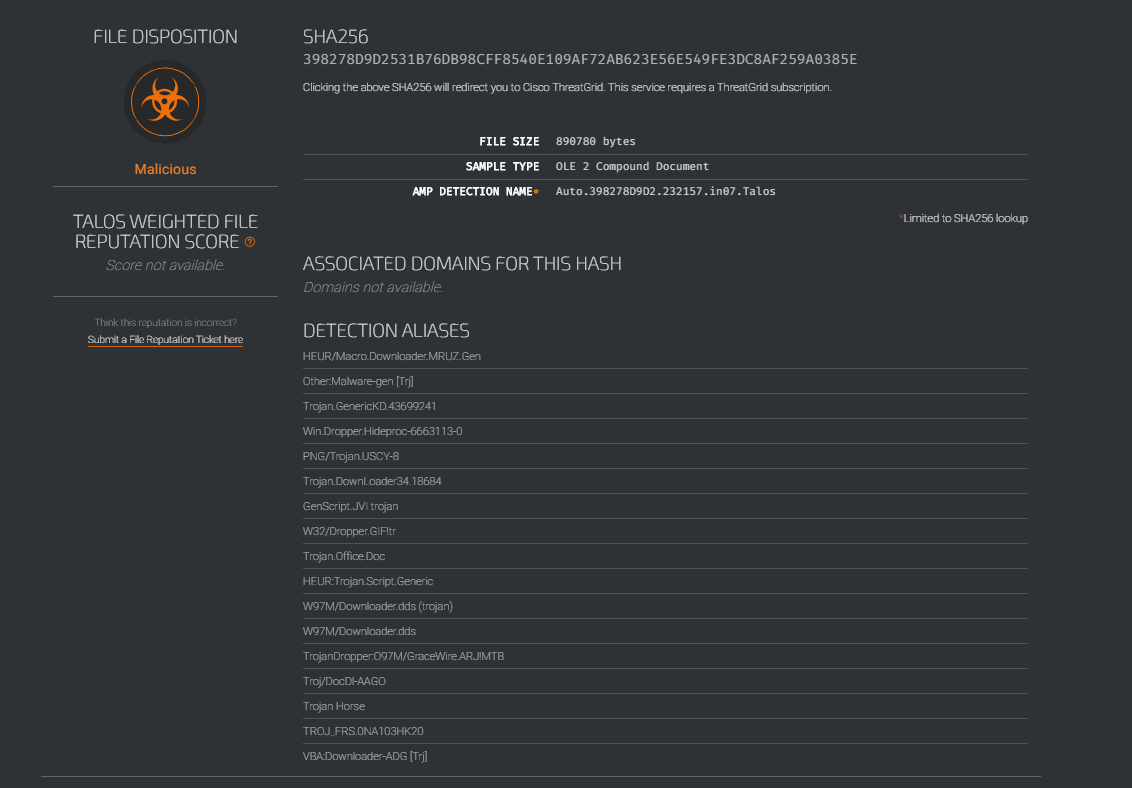
We then choose one of the MD5 hashes at random and checked it on VirusTotal and Talos Intelligence. The results are shown below.
In these two searches, we can see the Malware details, such as Malware type, SHA256, file type, and so on.
Tracing the Source of Known Threats 🔗︎
Content on the internet rarely remains the same, especially when it comes to that used by threat actors as part of their phishing campaigns. A useful Maltego Transform in this case is the To Snapshots [Wayback Machine] Transform, which can help you trace back the source of the threat.
The information discovered with Maltego may help us by providing context and insights into possible threat actors and their activities when we are trying to piece together the different elements that may be part of a potential threat to our organization. Therefore, organizations can use these indicators for analysis and prevention of future threats based on uncovered information about relationships between the threats and their analysis.
We hope this case study has provided you with some ideas on how to incorporate Maltego to your Threat Intelligence investigations.
Don’t forget to follow Maltego on Twitter and LinkedIn and subscribe to our email newsletter to stay updated on new tutorials, use cases, and news!
About the Author 🔗︎
Ata Şahan Erdemir is a cyber security analyst and academic researcher from Istanbul, Turkey, specialized in OSINT, IoT and Advanced Persistent Threat (APT) Groups. In this article, Ata investigates campaigns which are attributed to the TA505 Threat Actor group and their methods. Follow Ata on Twitter and LinkedIn.
Resources 🔗︎
- [1] Mitre Attack (2019), “TA505”, Retrieved from: https://attack.mitre.org/groups/G0092/#:~:text=TA505%20is%20a%20financially%20motivated,trends%20in%20criminal%20malware%20distribution. Access date: 08.21.2020
- [2]Proofpoint (2020), “TA505 Malware Threat Insights”, Retrieved from: https://www.proofpoint.com/us/blog/threat-insight/ta505-and-others-launch-new-coronavirus-campaigns-now-largest-collection-attack#:~:text=New%20TA505%20Malware%20and%20Campaign%20Examples&text=Once%20delivered%2C%20attackers%20can%20then,volumes%20of%20messages%20they%20send. Access date: 08.21.2020
- [3] Proofpoint (2020), “Coronavirus Cyber Threat Landscape Update”, Retrieved from https://www.proofpoint.com/us/threat-insight/post/coronavirus-threat-landscape-update
- [4] Alienvault OTX (2020), “TA505 Updated Domains” Retrieved from: https://otx.alienvault.com/pulse/5f2af3438e6633b8cd59afac. Access Date:08.26.2020
- [5] VirusTotal search results. https://www.virustotal.com/gui/file/398278d9d2531b76db98cff8540e109af72ab623e56e549fe3dc8af259a0385e/detection. Access Date: 08.28.2020
- [6] Talosintelligence search results. https://talosintelligence.com/sha_searches. Access Date: 08.28.2020
- [7] ZDNet (2020), “APT groups aren’t all from Russia, China, and North Korea” Retrieved from https://www.zdnet.com/article/apt-groups-arent-all-from-russia-china-and-north-korea/
- [8] Malpedia TA505 Actor Profile, https://malpedia.caad.fkie.fraunhofer.de/actor/ta505


![[VTPUB] Detected URLs Transform](https://www.maltego.com/images/uploads/ta-006.png)