Financial Damage of Fraud and Levers to Combat Fraud 🔗︎
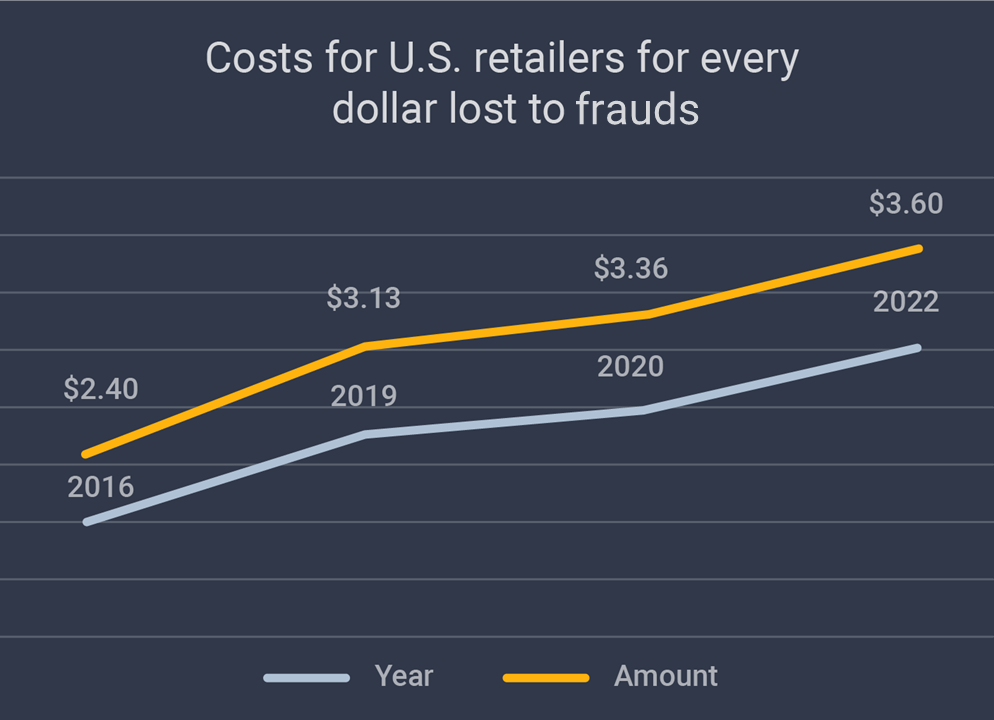
Virtually everyone in the developed world uses the internet, and every four out of five people worldwide admit to shopping online. Even if that only represents slightly over a quarter of the world’s population, it’s still quite impressive. ECommerce and Retail sector is set to see immense growth over the next decade or two. This means fraud will probably flourish, too. Retail ecommerce sales are set to reach $5.5 trillion in 2022. Currently, this represents about 21% of total retail sales worldwide. By 2025, it’ll likely make up a quarter of the total. The problem is that ecommerce presents an excellent opportunity for Fraudsters to take advantage of less tech-savvy people—which means that the more popular ecommerce is, the more common online fraud will be. As successful fraud attempts rise, so do the number of financial losses incurred by both businesses and individuals. In the US alone, the amount lost to fraud in 2021 was over 5 billion dollars. The per dollar cost of ecommerce fraud on retailers has also continuously increased, from $2.40 in 2016 to $3.13 in 2019, $3.36 in 2020 and $3.60 in 2021. See the Chart below for more detailed view of fraud cost and its growth.
Furthermore, based on the Federal Trade Commission’s Consumer Sentinel Report, the total amount lost to fraud in 2021 was $5,893,260,382 ($5.8 billion), an increase of more than 70% over the previous year. US retailers faced a 7.3% year-over-year increase in fraud costs and overall, it is estimated that online fraudsters will take more than $12 billion from businesses in 2022.
Money aside, fraud can also severely damage a company’s brand, as 40% of customers state that they will blame the retailer for their accounts not being properly looked after. So, a business could actually lose its consumer base to top it all off. It is a vicious cycle that could heavily impact the economy in the long term.
What are Typical Fraud Workflows? 🔗︎
With regard to fraud, we should differentiate between reactive and preventive measures. Reactive workflows are those which are taken once fraud has already been committed and, therefore, will need to be done under an intense amount of pressure, timewise. Preventive has more to do with company culture and habits, such as not opening spam emails, to prevent the crime before it occurs. With Maltego in particular, a preventive workflow is made up of due diligence, KYC, and attack surface management, among others.
Preventive Measures 🔗︎
In most ideal cases, one would want to prevent the fraudulent activity before it even occurred. In this instance, preventive measures can be taken to protect your data from cybercriminals.
- Risk assessment: The first step one should take to prevent fraud is to test fraud prevention security in your company. This will give you a clear indication of any possible “weak points” that may need addressing.
- Use all the available tools: Fight fire with fire and use technology to your advantage. Ensure that all systems are fully up to date, enable authentication and email filters, and make use of anti-phishing and anti-virus programmes.
- Social media protocols: Seeing as most hackers tend to gather information using social media, it is a good idea to place protocols on social media use in the office. This can include going as far as implementing blocks on certain websites which could be considered harmful.
Reactive Measures 🔗︎
There are situations where fraud has, unfortunately, already taken place before you could do anything to prevent it. However, this is not the time to panic as there are certain reactive measures that can be taken in these cases.
- Alert your team: This should be done immediately, so that all parties are aware of the danger and can react accordingly.
- Change passwords: To halt any more harmful activity in its tracks, it would be advisable to change all passwords on accounts which have been harmed or threatened.
- Implement additional authentication: Now that the harm has already been done, it is a good idea to improve security wherever possible. For example, a two-factor authentication process could help shield from further attacks.
How Fraud Relates to the Cyberspace 🔗︎
Cyber-Enabled Fraud and What it Entails 🔗︎
Internet fraud makes use of Internet-connected/enabled software and services to defraud and take advantage of victims. This type of crime can be done through a variety of methods, which separates it into a multitude of branches or types. Each type of fraud also has its own goals, some of which may overlap.
In this whitepaper, we outline the most commonly known cyber-enabled fraud, their goals, and how they impact an organization or business:
- Account Takeover
- Identity Theft
- Real-Money Trading
- Insider Threat
- Returns or Payment Fraud and Promo Abuse
- Fake Listings and Reviews
- Affiliate Fraud
- Triangulation Fraud
Download this whitepaper to gain insights to how each type of fraud is carried out and what goals malicious actors are trying to achieve.
Don’t forget to follow us on Twitter and LinkedIn and sign up to our email newsletter, so you don’t miss out on updates and news!
Happy investigating!