
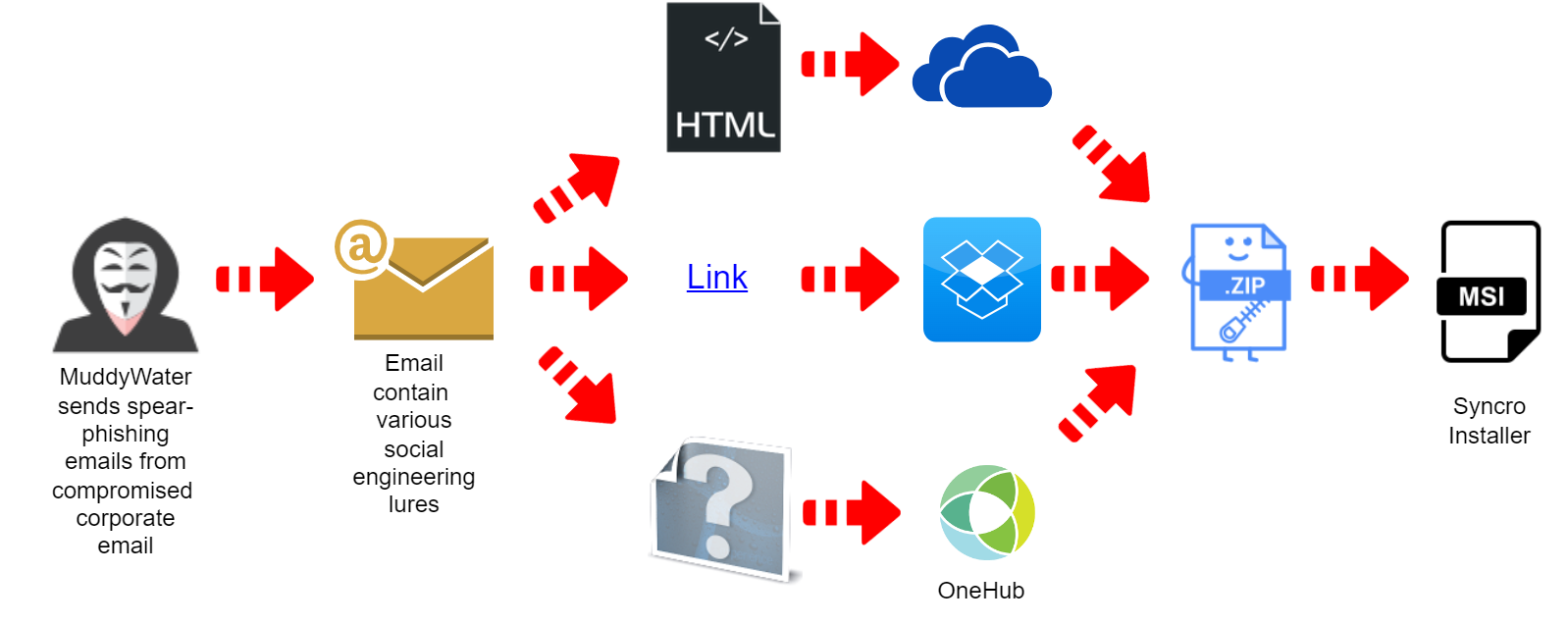
MuddyWater hackers, a group associated with Iran’s Ministry of Intelligence and Security (MOIS), used compromised corporate email accounts to deliver phishing messages to their targets.
The group adopted the new tactic in a campaign that might have started in September but wasn’t observed until October and combined the use of a legitimate remote administration tool.
From one MSP tool to another
MuddyWater has used legitimate remote administration tools for its hacking activities in the past. Researchers discovered campaigns from this group in 2020 and 2021 that relied on RemoteUtilities and ScreenConnect.
In another campaign in July, the hackers continued with this tactic but switched to Atera, as highlighted by Simon Kenin, a security researcher at Deep Instinct.
Deep Instinct researchers caught a new MuddyWater campaign in October that used Syncro, a remote administration tool designed for managed service providers (MSPs).
Kenin notes in a report today that the initial infection vector is phishing sent from a legitimate corporate email account that the hackers compromised.
source: Deep Instinct
The researcher told BleepingComputer that while the official signature of the company was missing from the phishing message, victims still trusted the email since it came from a legitimate address belonging to a company they know.
Among the targets in this campaign are two Egyptian hosting companies, one of them breached to send out phishing emails. The other was the recipient of the malicious message.
“This is a known technique to build trust. The receiving end knows the company who sent the mail,” Kenin explains in a report today.
To lower the chance of getting detected by email security solutions, the attacker attached an HTML file containing the link to download the Syncro MSI installer.
“The attachment is not an archive or an executable which doesn’t raise the end-user suspicion because HTML is mostly overlooked in phishing awareness trainings and simulations” – Deep Instinct
The tool was hosted on Microsoft’s OneDrive file storage. A previous message sent from the compromised email account of the Egyptian hosting company stored the Syncro installer on Dropbox.
However, the researcher says that most Syncro installers used by MuddyWater are hosted on OneHub’s cloud storage, a service the actor used in the past for its hacking campaigns.
Syncro has been used by other threat actors such as BatLoader and LunaMoth. The tool has a trial version valid for 21 days that comes with the complete web interface and provides full control of a computer with the Syncro agent installed.
Once on the target system, the attackers can use it to deploy backdoors to establish persistence as well as steal data.
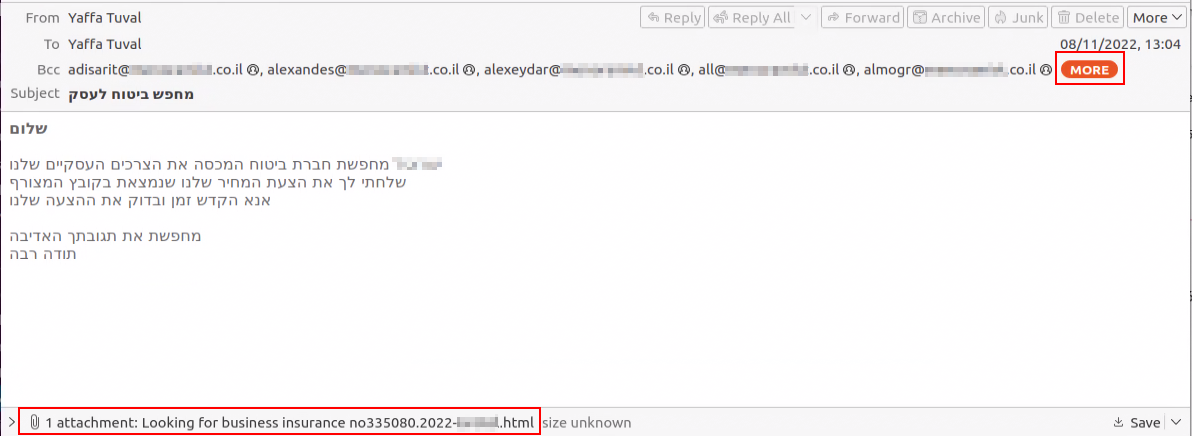
Other targets in this MuddyWater campaign include multiple insurance companies in Israel. The actor used the same tactic and delivered the emails from a hacked email account belonging to an entity in the Israeli hospitality industry.
Under the pretense of looking for insurance, the hackers added an HTML attachment with a link to the Syncro installer hosted on OneDrive.
source: Deep Instinct
Kenin observes that while the email was written in Hebrew, a native speaker could spot the red flags due to the poor choice of words.
MuddyWater’s tactics are not particularly sophisticated, yet show that freely available tools can be effective for hacking operations.
The actor is tracked by different names (Static Kitten, Cobalt Ulster, Mercury) and has been active since at least 2017.
It typically engages in espionage operations that target both public and private organizations (telcos, local governments, defense, oil and gas companies) in the Middle East, Asia, Europe, North America, and Africa.



