For the cyber intelligence community, MITRE ATT&CK has become the standard for modelling and communicating adversarial tactics and techniques based on real-world observations. Provided and maintained by the MITRE organization, the ATT&CK Matrices are enabling numerous communities to develop more effective cybersecurity practices.
In the same communities, MISP needs little introduction. The MISP threat sharing platform is free and open-source, facilitating information sharing of threat intelligence including cybersecurity indicators. The MISP Project has developed models, formats, and taxonomies to standardize the documentation and sharing of IOCs in an automated fashion.
For some time now, Christophe Vandeplas has been the force behind an effort to bring ATT&CK and MISP Transforms to Maltego, and we are happy to announce that these Transforms are now officially part of Maltego’s Transform Hub.
ATT&CK, MISP and Maltego 🔗︎
There are many communities out there with different focuses, and organizations contributing to them. One place to start is here: https://www.misp-project.org/communities/. You will need a link and an API key for a community in order to use the MISP Transforms, however, the ATT&CK Transforms do not require these. For this blog, we are going to be using data from a community established around the COVID-19 cybercrime events. MISP is agile and flexible enough that you can add almost any information to it, and this community contains both medical data such as the number of active cases for different countries, but also cyber threat information such as for phishing attacks. We will be focussing our discussion on the latter.
The center point for information in MISP is the “Event”. An event has an ID, and associated with this are various attributes, objects, tags, and a concept called a Galaxy (documentation also available here): a collection of events or attributes, expressed as key-value pairs clustered together.
In your investigations, you may come across some information such as a Domain, DNS Name, email address or IP Address that seems suspicious. The MISP Transforms allow you take any information you can get in Maltego (any Entity type) and look it up in the MISP community to see if it has already been recorded.
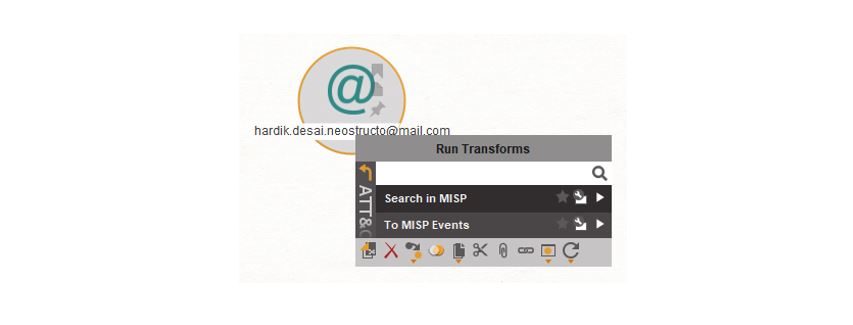
Let us start with an email that our Spam-trap has detected. The source email is given as hardik.desai.neostructo[at]mail.com. We continue our investigation of this email address by adding it to a new graph. In the Transform menu, under the ATT&CK and MISP Transform group, we use the “To MISP Events” Transform to find any related events.
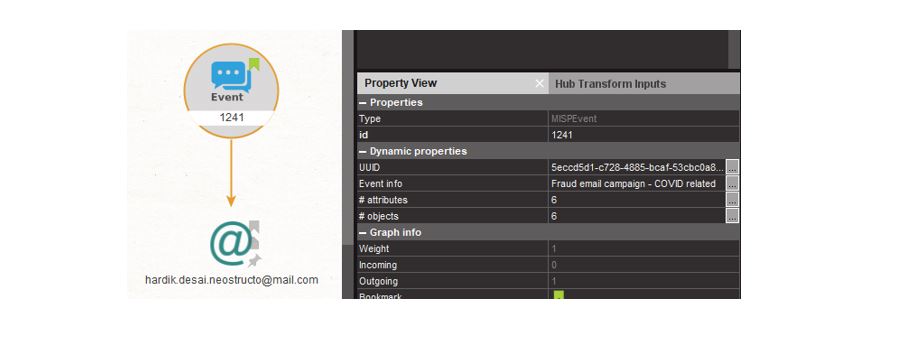
Sure enough, the email has been recorded as an attribute of event with ID 1241. The Event info detail in the Property View of Maltego also tells us that this is associated with a COVID-related fraud email campaign, and that there are six other attributes and objects known about this event.
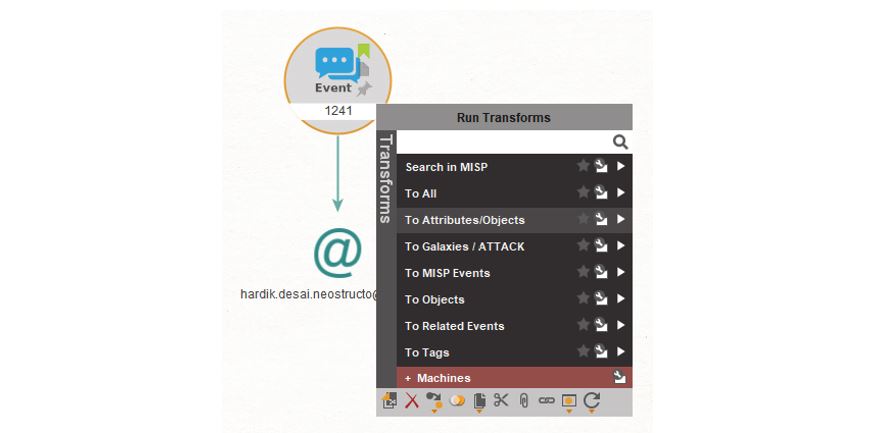
Next, we would like to see what else is known about this event, and for that, we can use the “To Attributes/Objects” Transform.
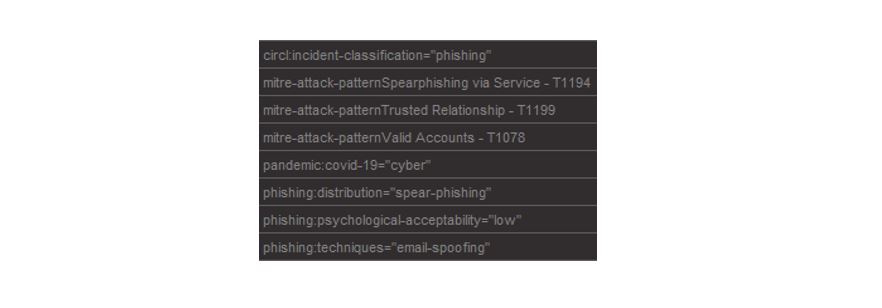
Running this Transform quickly brings back the list of attributes and objects, including IP addresses, URLs and domains, and a link to a VirusTotal report. From the Event Entity there are further steps you could take, such as finding related events, or pulling a list of the tags. Running the “To Tags” Transform, we learn that this event is classified as being a cyber threat, part of a spear-phishing campaign, and that it makes use of email spoofing (shown here in the List view of Maltego).
We also see some ATT&CK patterns associated with this event, which is the next topic of this post.
Exploring the ATT&CK 🔗︎
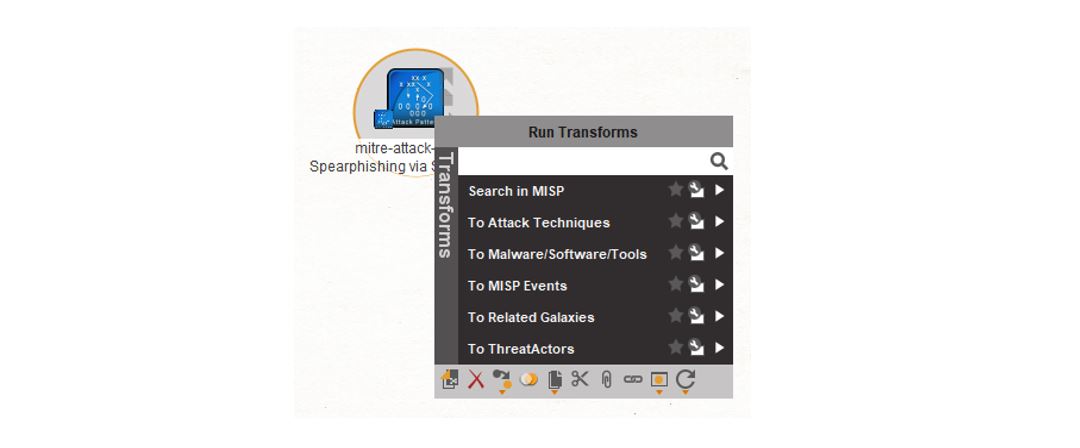
Using the MITRE ATT&CK framework data we can arm ourselves with the information that we need to better protect ourselves against this kind of attack and test our readiness to deal with such an attack in the future. In Maltego, we can look up some of the details for an attack technique. Selecting the “mitre-attack-pattternSpearphishing via Service – T1194” Entity from our graph, we find that we can look up details about the Malware, Software and Tools used in these attacks in the list of Transforms. In addition, we can find other MISP Events associated with this attack, and look for specific Threat Actors known to use this attack pattern.
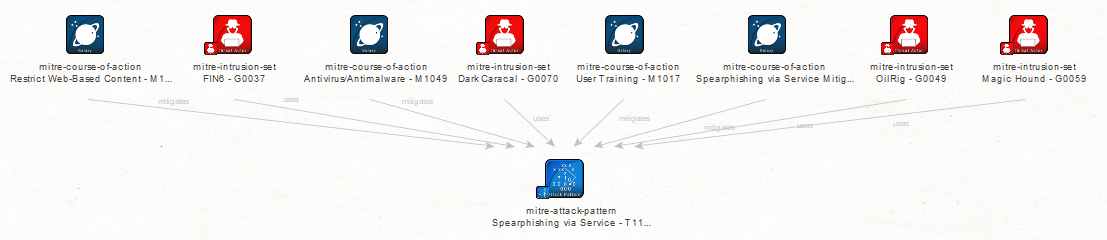
Running the “To Related Galaxies” Transform, we can pull in the details for this pattern, including the threat actors making use of it (e.g. FIN6, Dark Caracal, OilRig and Magic Hound). Through this, we can also discover suggested mitigation techniques to protect you against this kind of attack, such as using Antivirus/Antimalware software, performing User Training, and restricting web-based content.
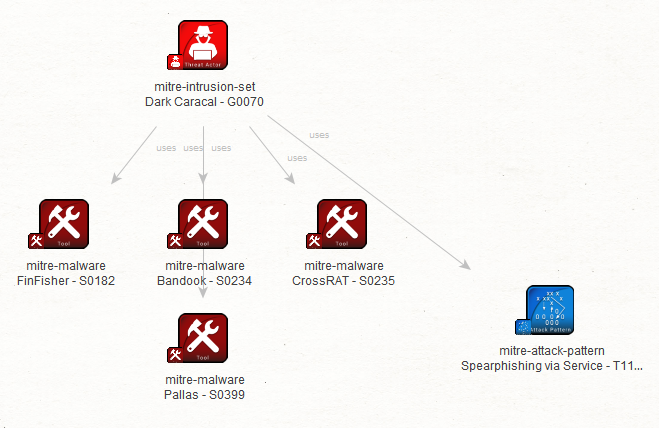
And finally, from a Galaxy there is of course a lot more information you can pivot to. For the sake of brevity, let us just look at one more example, and look up the Malware, Software and Tools that Dark Caracal tends to use, using the “To Malware/Software/Tools” Transform on the Threat Actor.
The Transform reveals their preference for FinFisher, Bandook, CrossRAT and Pallas Malware. As you can gather, there is quite a lot that you can do with the MITRE ATT&CK and MISP data integration using Maltego, and we encourage you to have a look at the GitHub page of the Maltego Transforms for ideas and inspiration.
We would like to extend a special thank you to Christophe Vandeplas for driving this effort, and for helping us integrate the Transforms with the Hub. As always, do not hesitate to reach out to us if you have suggestions, questions, or comments. Do not forget to follow our Twitter and LinkedIn pages or subscribe to our email newsletter.