A while ago, Simone (@evilsocket) published his awesome ditto tool for checking a domain for active imposter attacks, and I finally found some time to play with it.
With the ditto Transform server, multiple analysts can run Transforms to check domains for active imposters without calculating the variations and checking them on their own machine, but on a dedicated server instead. The server can take care of throttling the external lookups to avoid being rate limited. In addition, future updates could add a queuing mechanism.
In Part 1 of the DittoTRX release, I walked through the setup and codes for the data integration. In this article, I will demonstrate how to use these Transforms in Maltego.
Releasing DittoTRX for Maltego 🔗︎
This 2-part article series will walk you through the release of the ditto Transform server, setting up the server, and how to use the Transforms in Maltego.
Using DittoTRX Transforms in Maltego to Investigate IDN Domains 🔗︎
So lets go and check some domains!
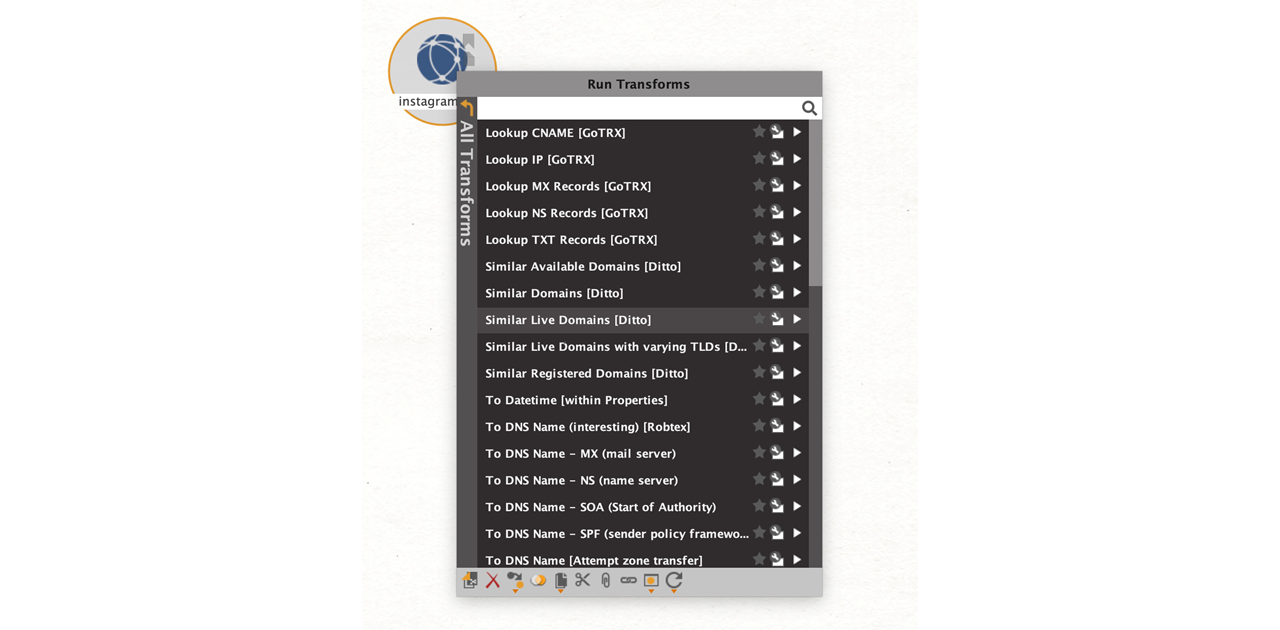
First, drag a standard Maltego Domain Entity, add the input value, and right click to call out the Transform Menu. The Transform Menu will display all the Transforms installed in your Maltego Desktop Client.
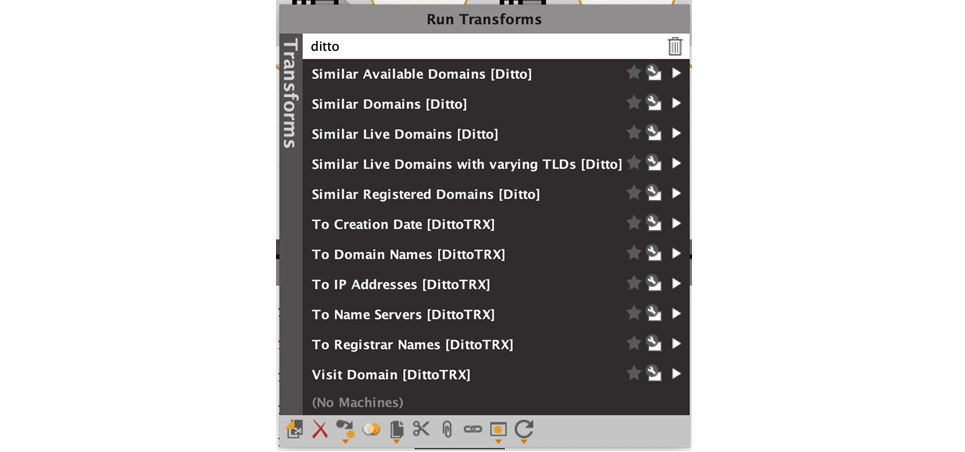
All the transforms that end with [Ditto] are from the ditto service. You can filter only for these by entering the search term “Ditto.”
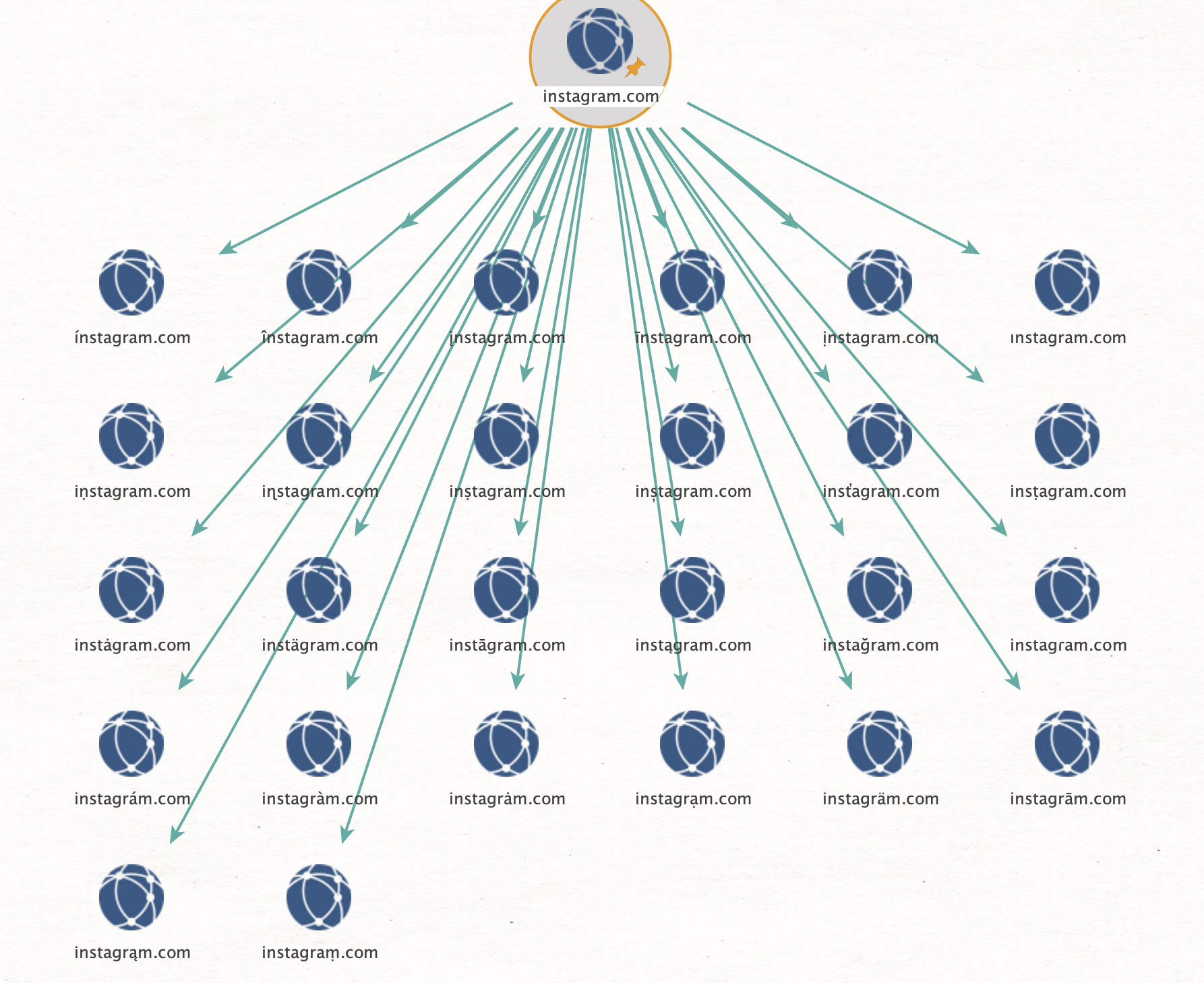
I ran the Similar Live Domains [Ditto] Transform to ask the server to calculate all possible variations as well as to see whether the resulting domains are registered, where they are pointing to, and if the underlying IP addresses are reachable.
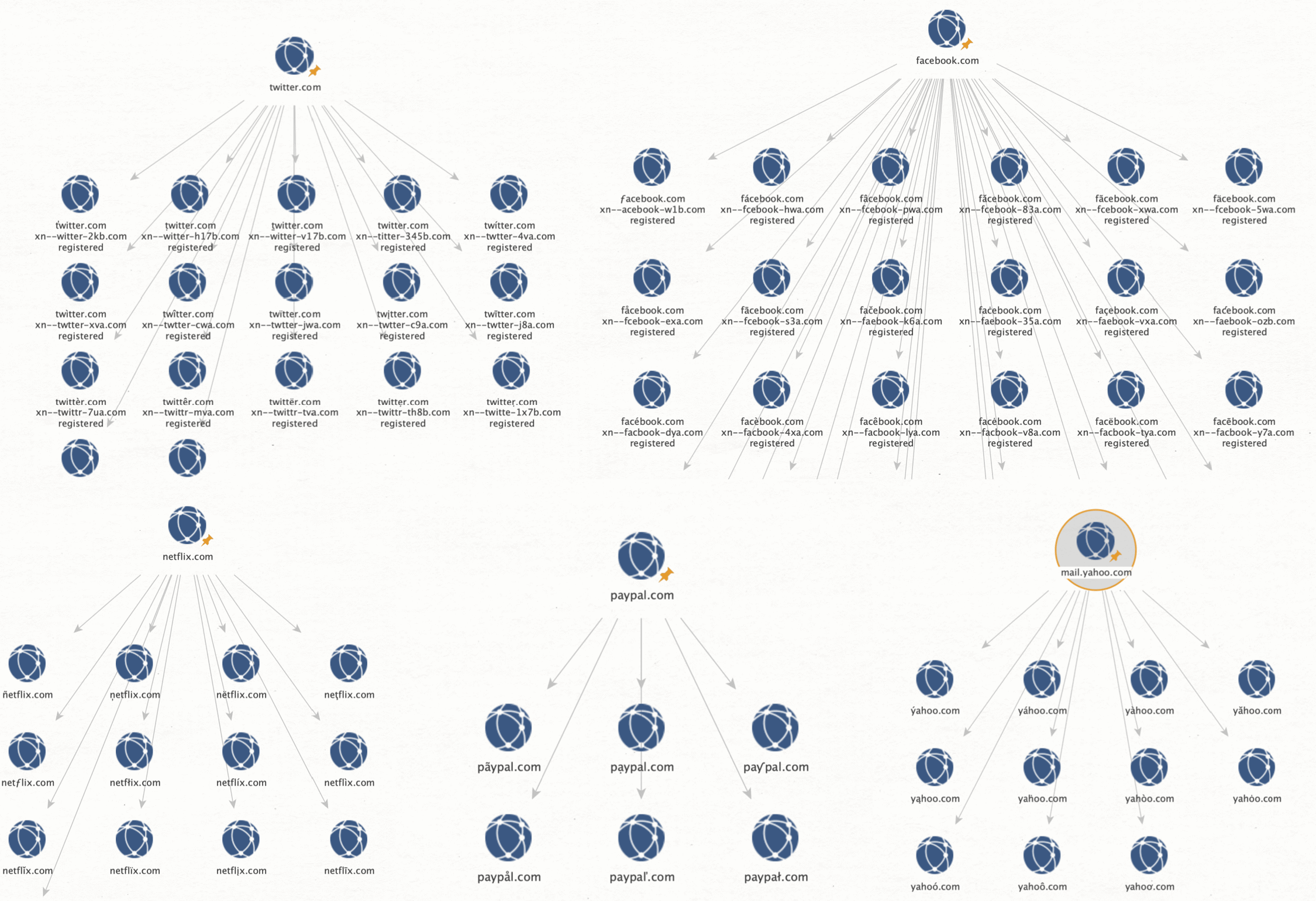
We can repeat this for many big companies and yield results. Although the majority of the results seems to be leftovers from past campaigns that are no longer active, but they are still registered and redirect to their registrars page.
I’ve added the Visit Domain [Ditto] Transform to open all selected entities in the default system browser, so it’s easy to open them all at once to see what content they are currently serving.
Obviously this poses a security risk as one of the sites could serve an exploit that affects your browser! Consider doing this only in a sandbox.
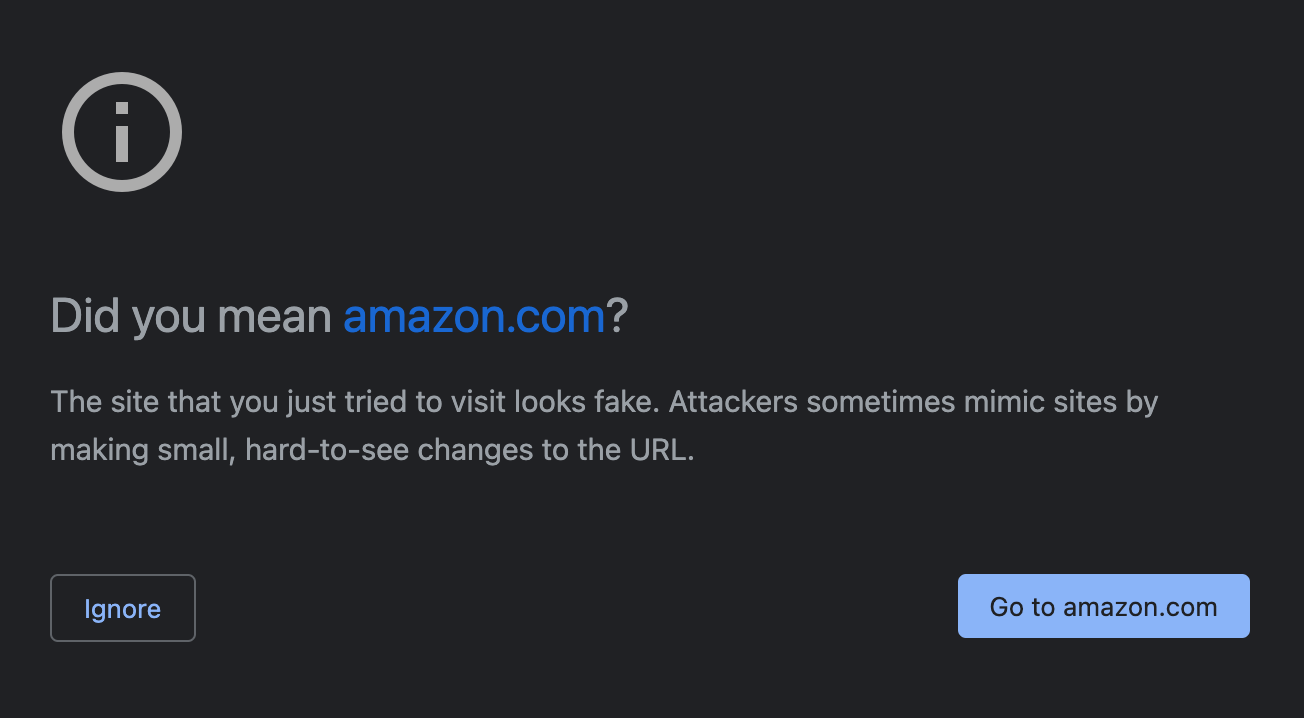
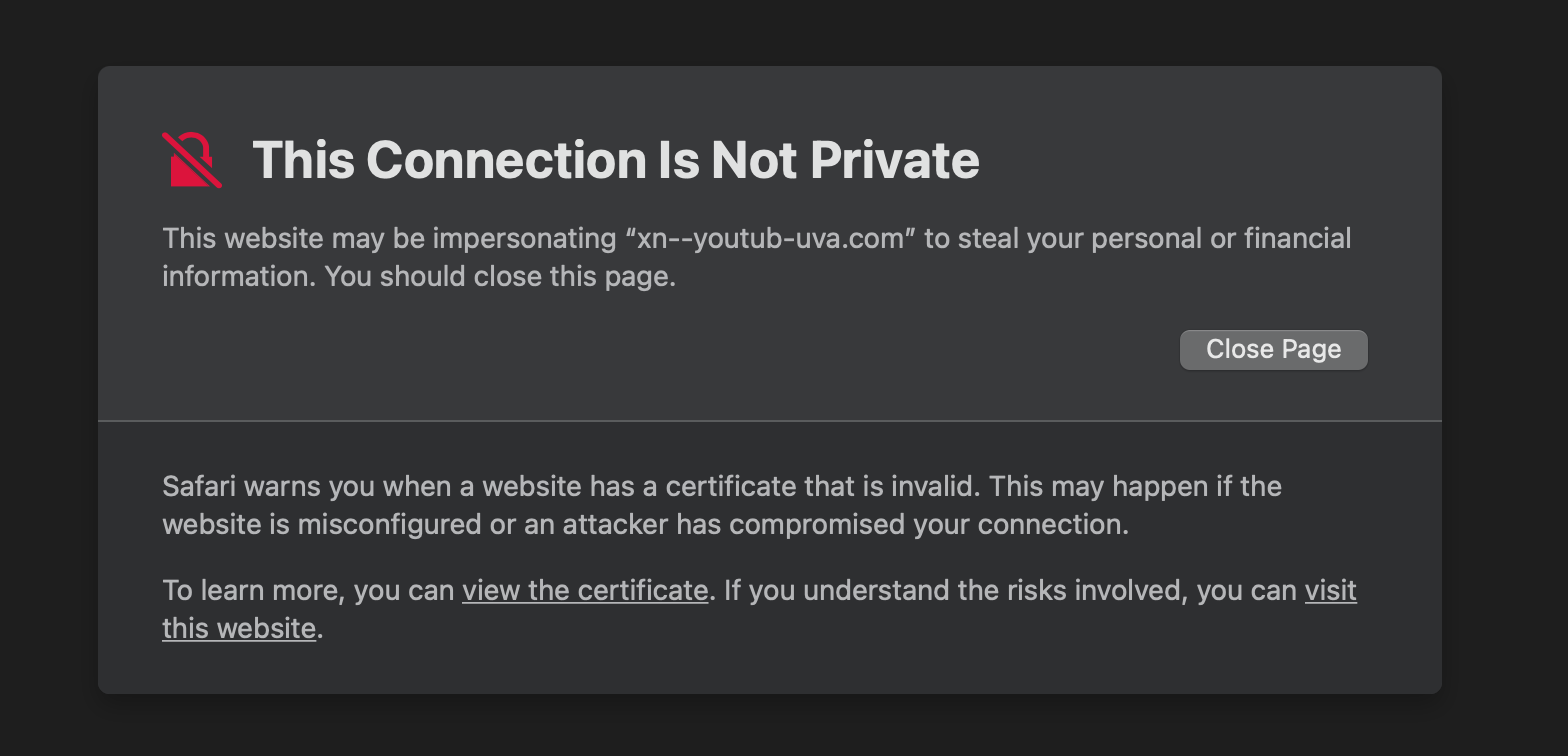
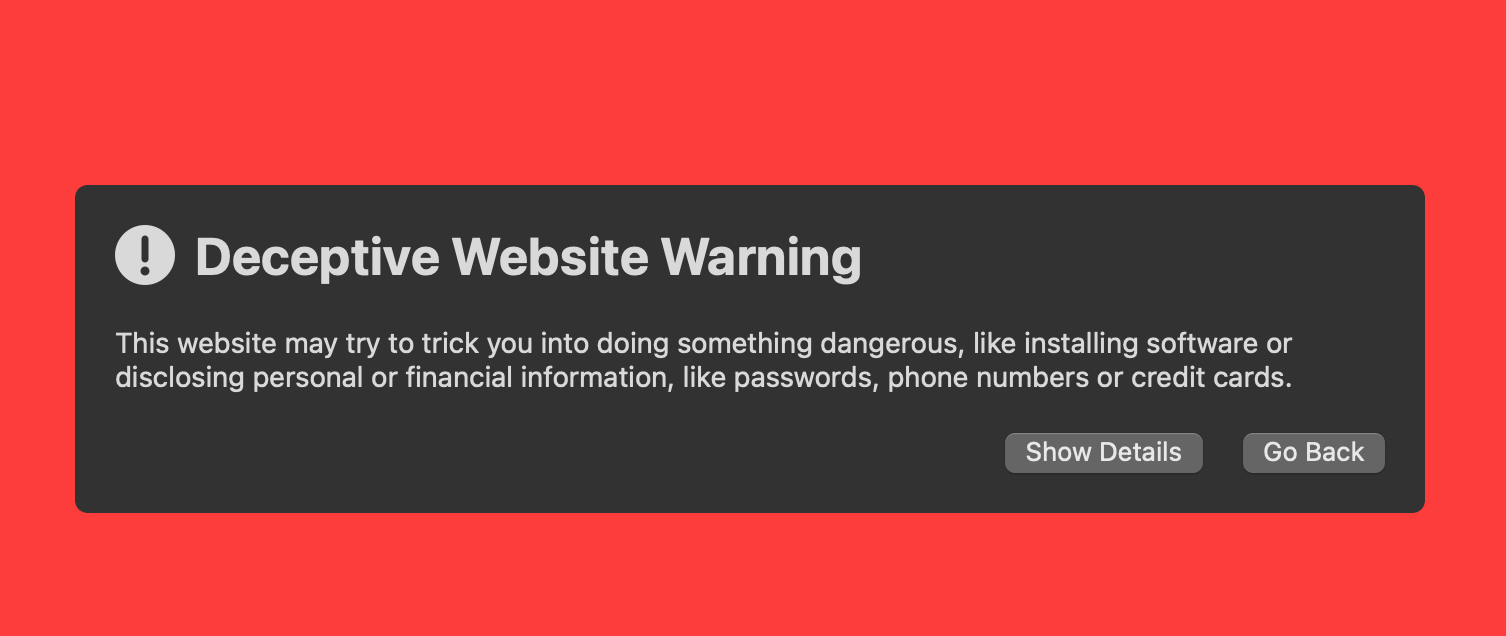
The Chrome browser issued a warning when visiting the sites.
On the other hand, Safari does not care while several websites also have a valid TLS certificate.
I noticed that many sites are not always delivering the same result, so after reloading them they would serve a different page. This is likely because the server checks certain parameters that are set during redirects to only deliver payloads to intended victims.
Checking Imposter Domains of Instagram, YouTube, Netflix, Microsoft, Amazon, and more… 🔗︎
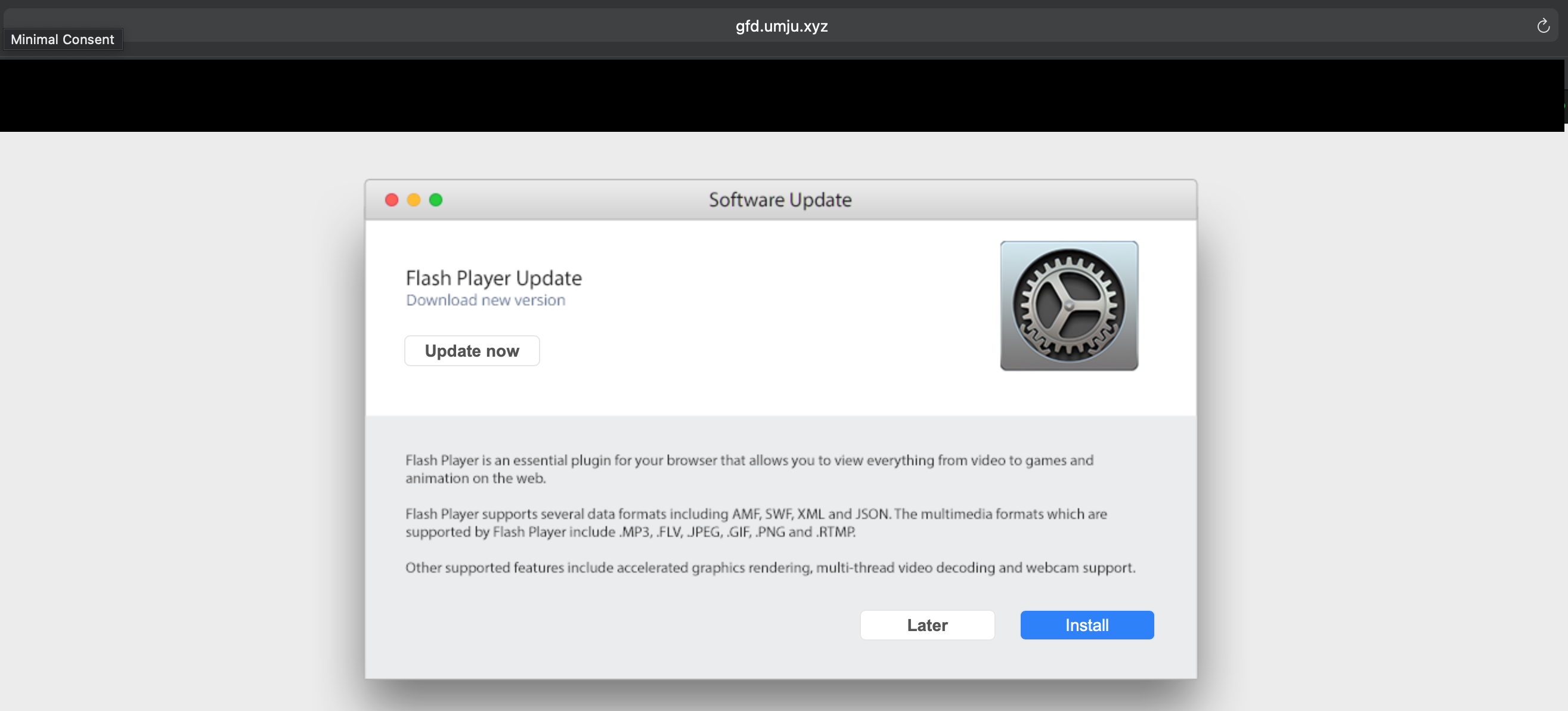
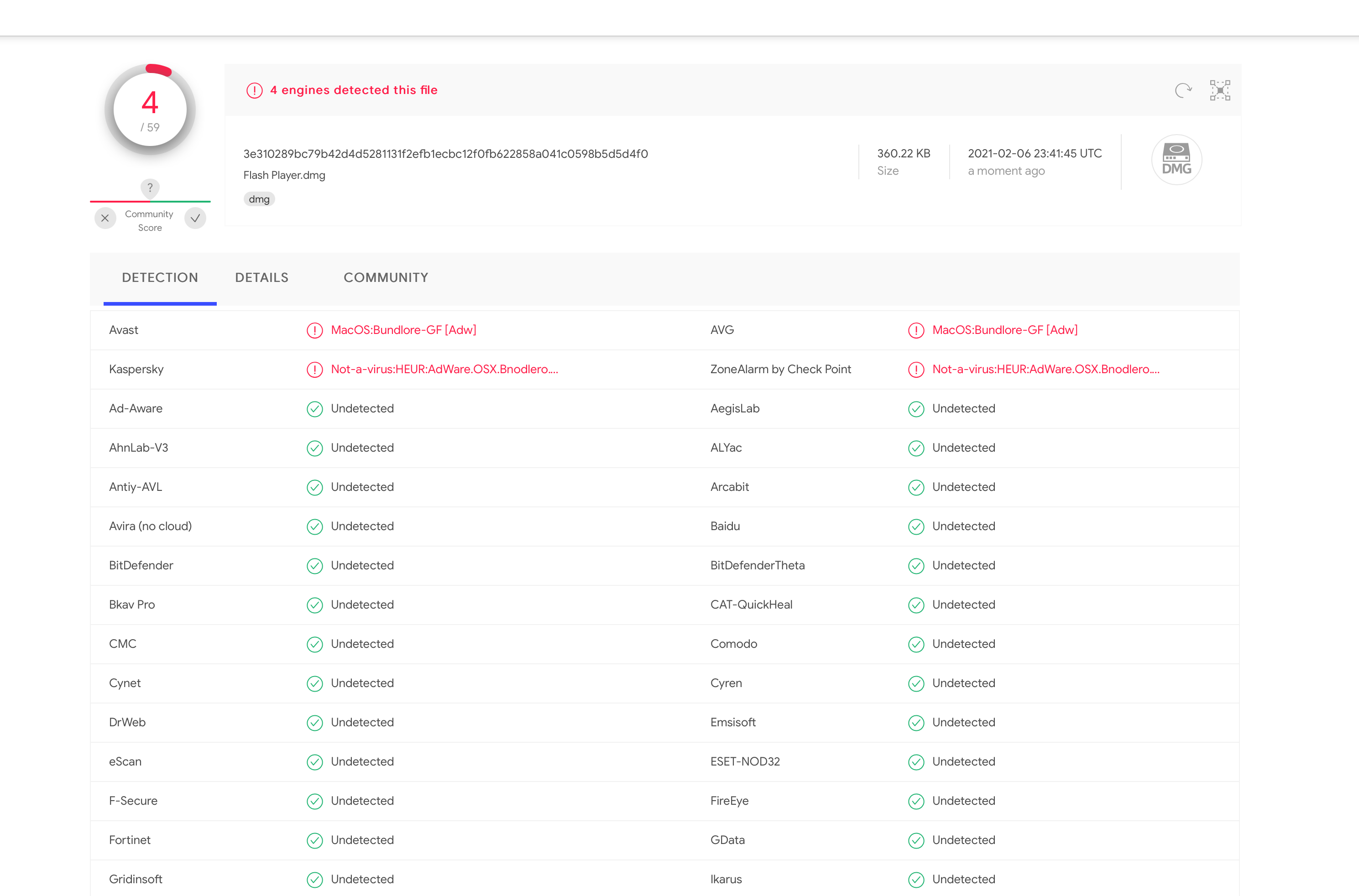
Some Instagram imposters are redirecting to a malicious flash player update that seems to be adware according to the VirusTotal scan.
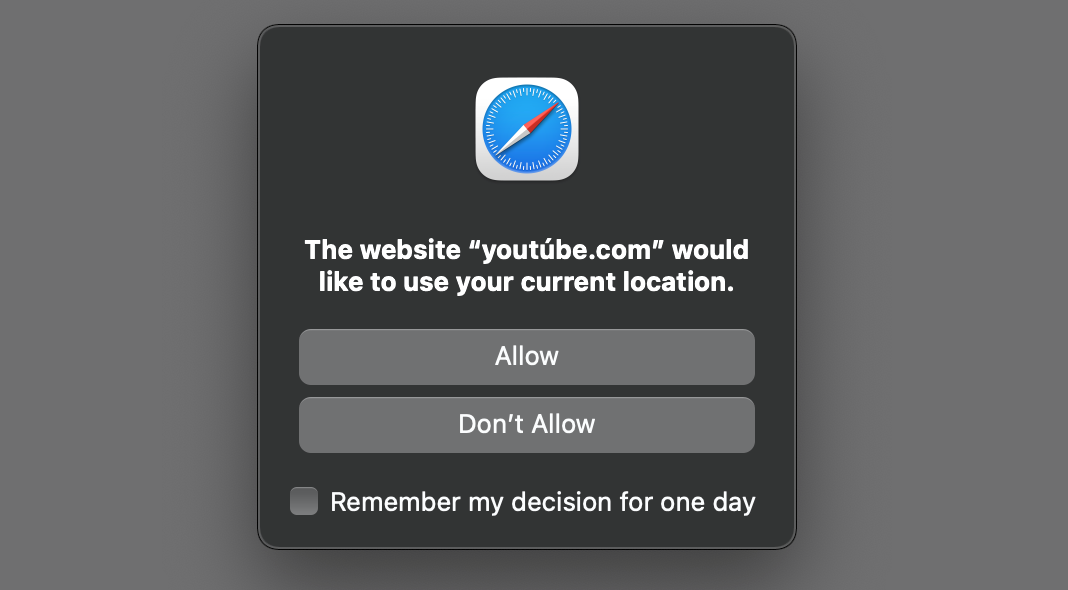
A YouTube imposter politely asked for my location:
Some websites have expired certificates, which indicates they have been operated before. As setting up a service with TLS requires additional effort, and who would do that if they did not intend to use it for something…
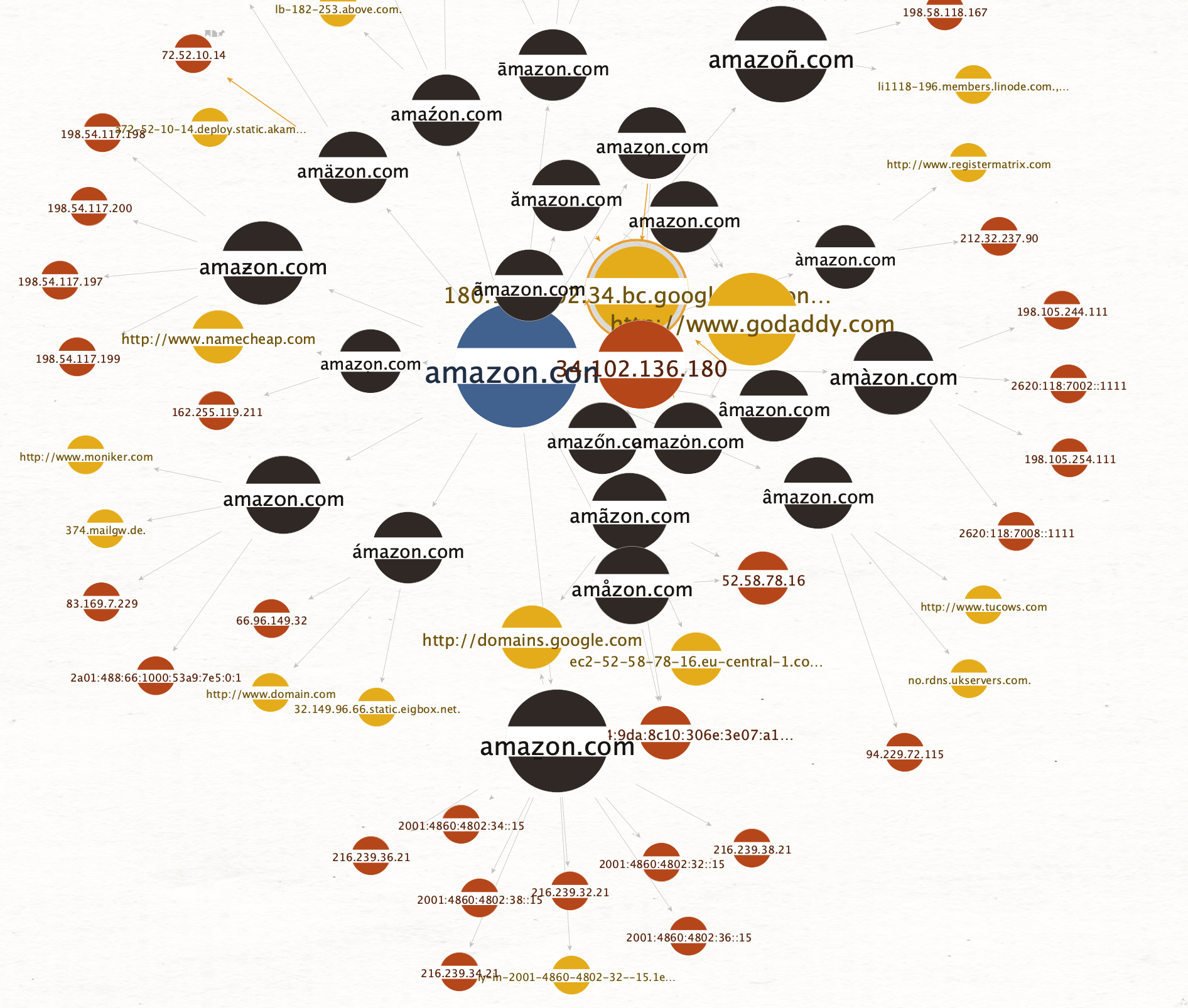
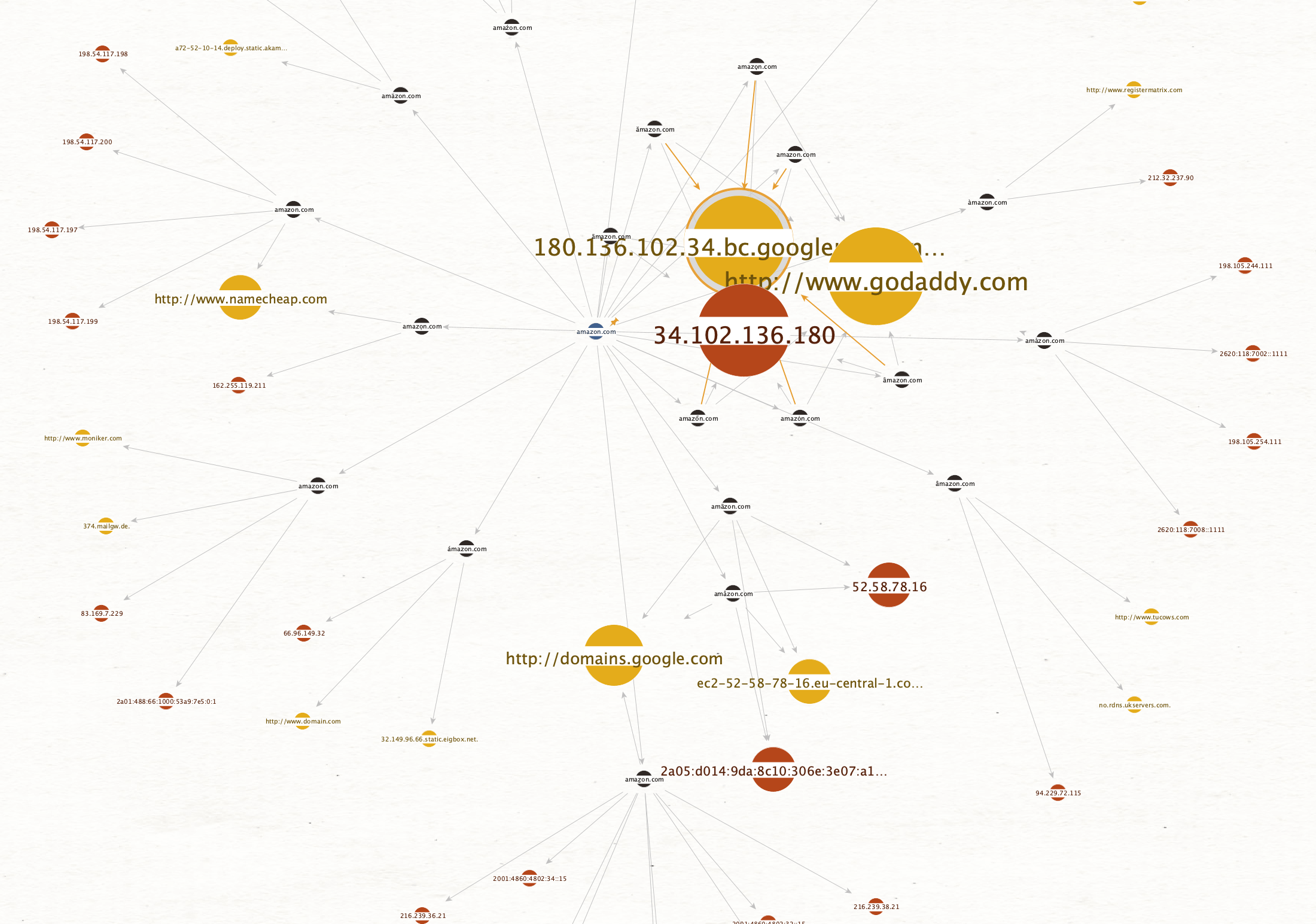
Let’s play with the Ball Size by Links (Outgoing) viewlet in Maltego to look at the different Amazon domains, by increasing the size of entities the more outgoing links they have:
Let’s change the view again to Ball Size by Rank to look at the most common registrars for Amazon imposters. Now, the more links going towards an Entity, the bigger it will become:
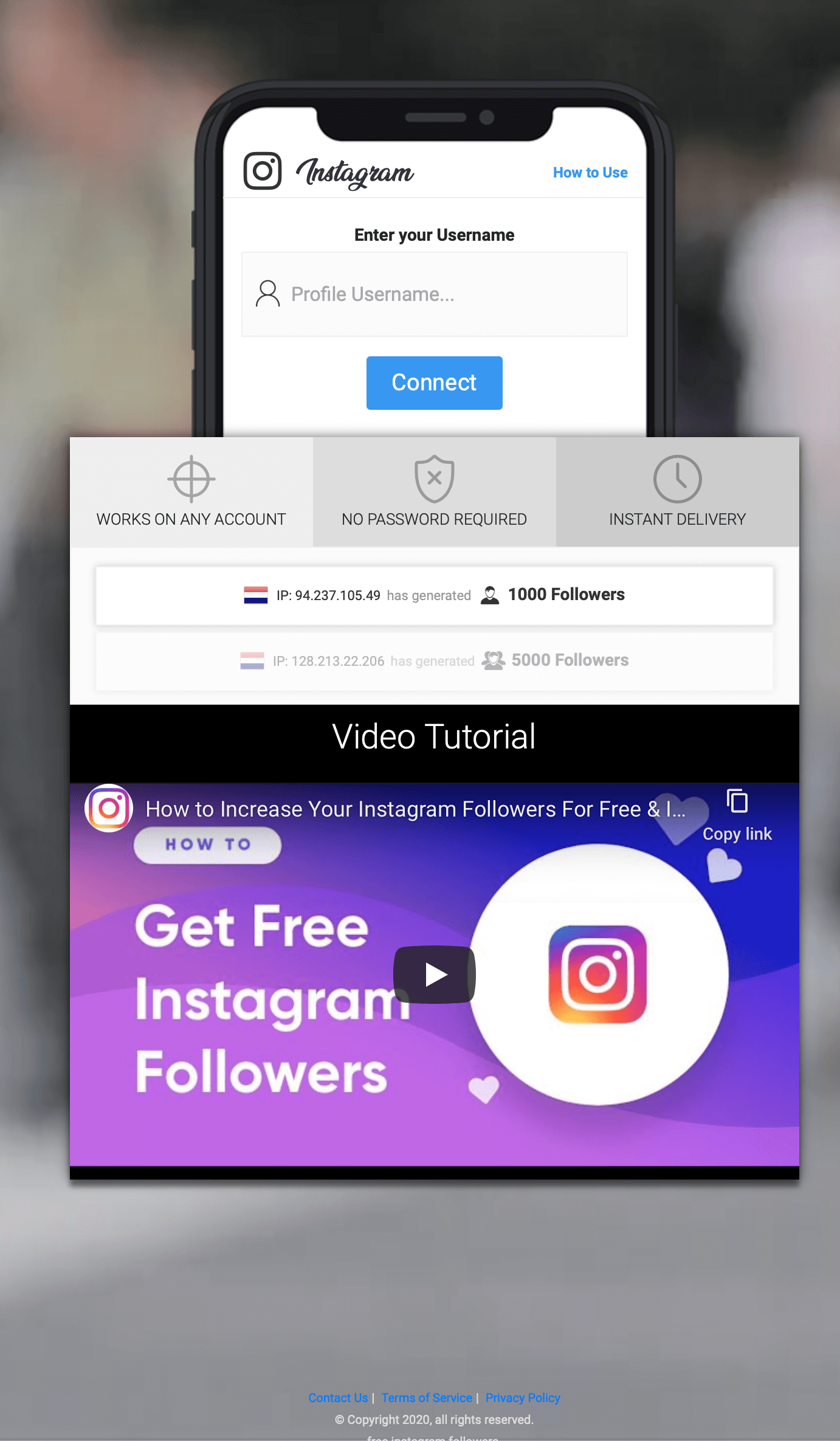
An Instagram follower optimization service, that takes their users privacy very serious:
Several sites enjoy protection from Cloudflare:
Fun fact: Cloudflare is the only one of the checked domains that has only a single imposter domain.
And that one (https://xn--cludflare-6x3d.com/) is owned by Simone (the developer of the ditto tool) and redirects to the ditto github repo 😉
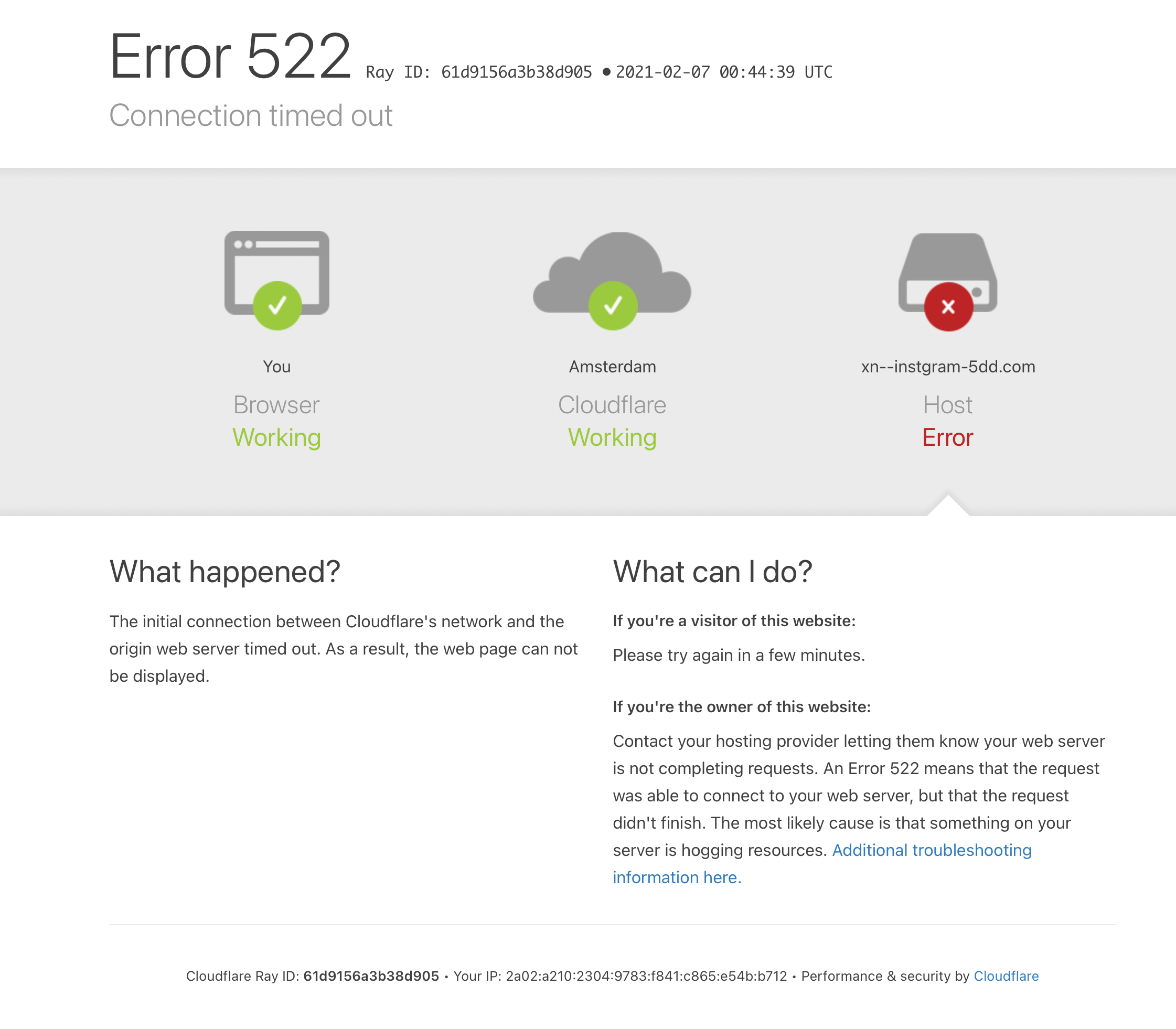
Some websites are on block lists already and will trigger a warning in the browser:
One of the Netflix imposters has a LiteSpeed Web Server running that serves Amazon-named content:
Retrieving Creation Dates of the IDN Domains 🔗︎
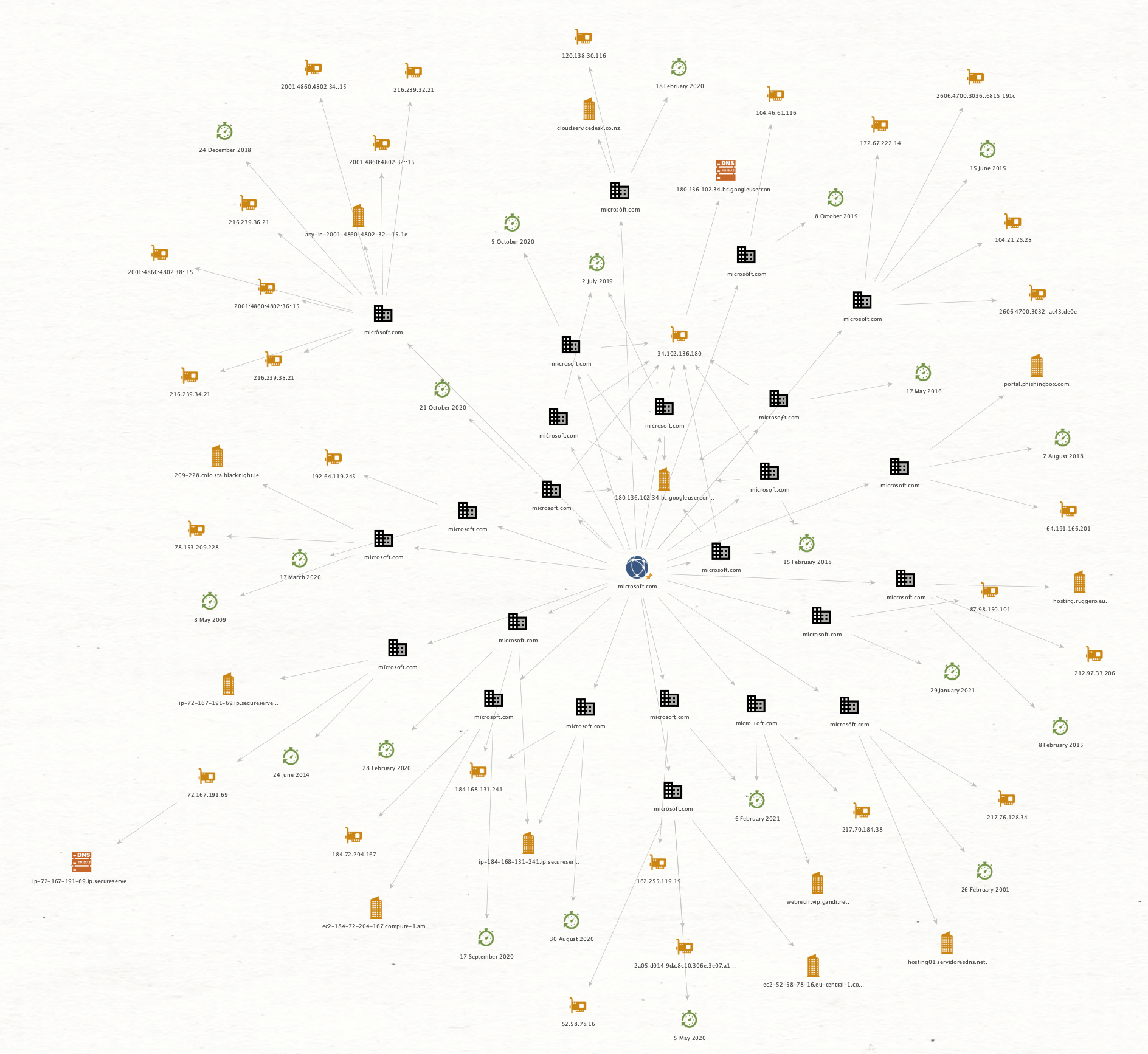
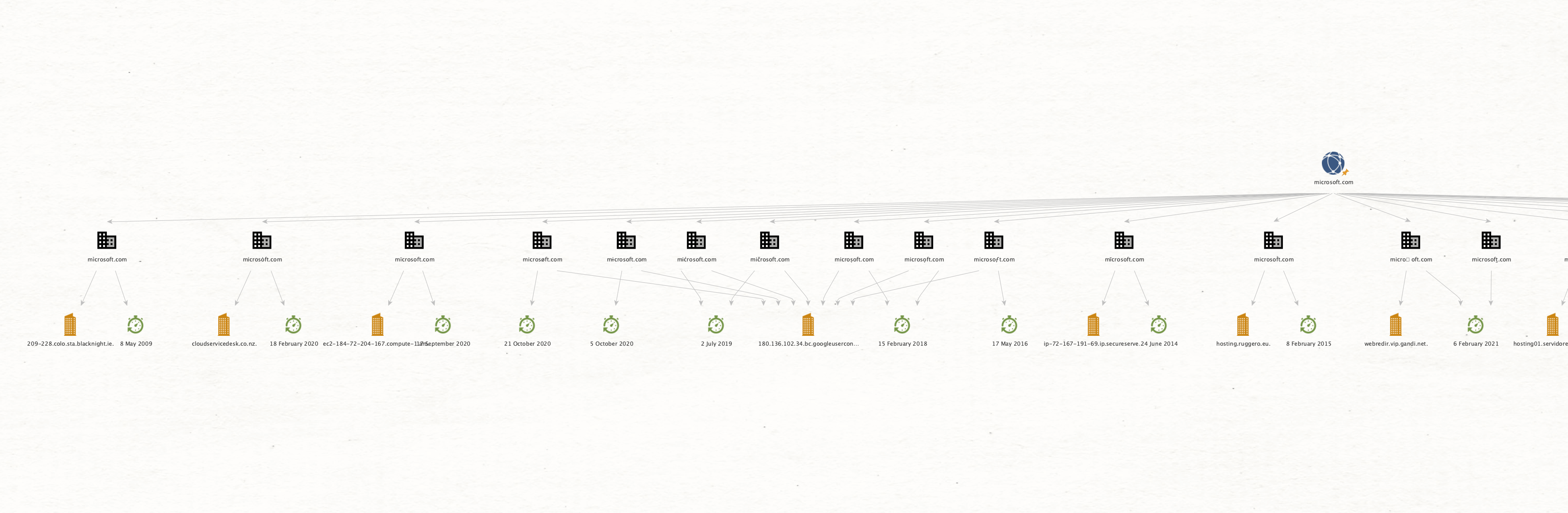
There is also support to show the Creation Date of the IDN domains using the To Creation Date [DittoTRX] Transform. Let’s see what it shows for Microsoft:
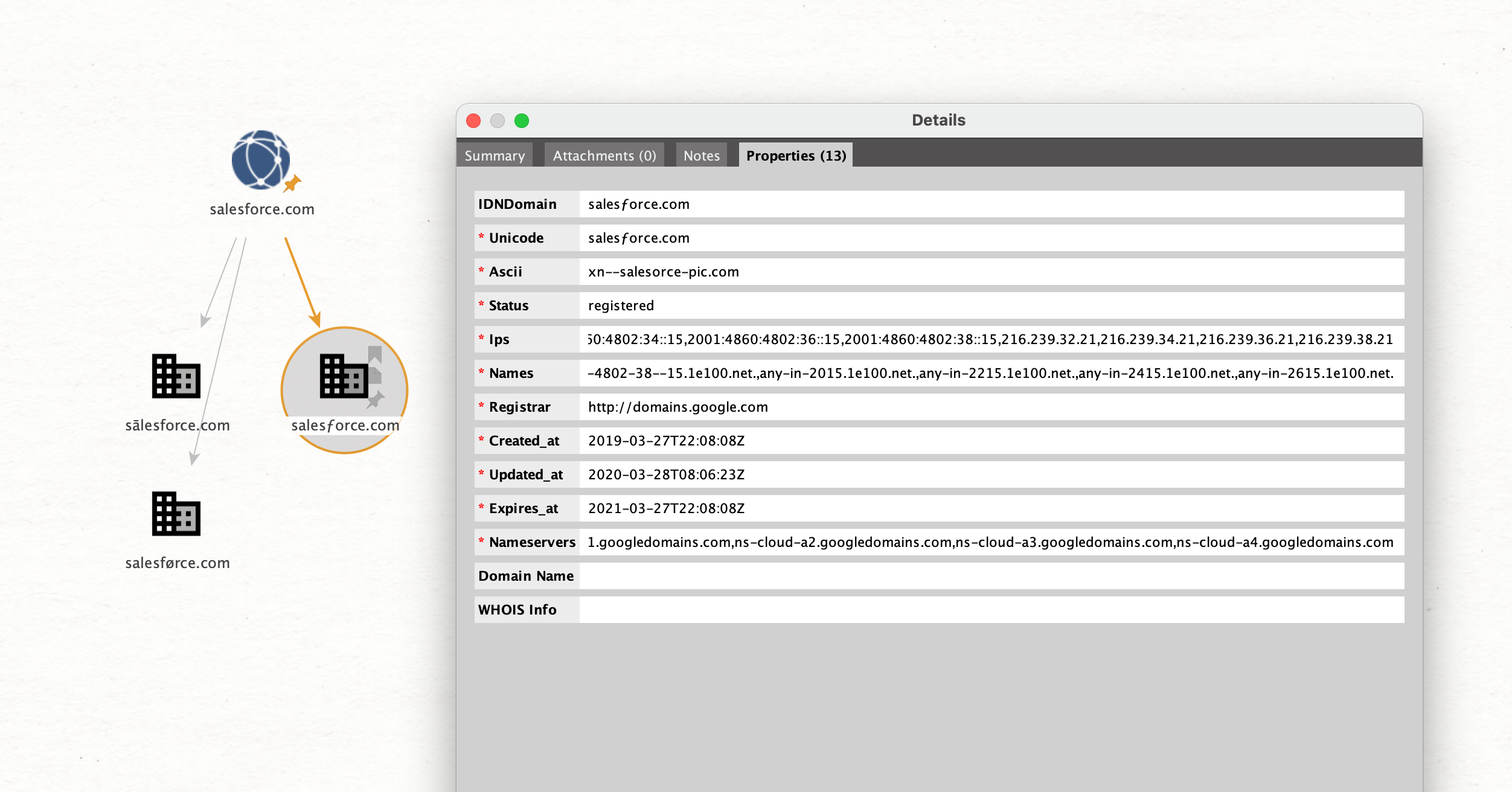
When double clicking an IDN Domain Entity, the properties can be inspected:
Start Using the DittoTRX Transforms in Maltego! 🔗︎
This blog post only touches the surface of what can be done using this Maltego integration. Give it a try and let me know what you think!
From exploring a couple domains from big Fortune 500 companies, I get a feeling that plenty of those domains have been used in the past for advertising or distribution of malware. Several services responded but did only serve a default web server page or a 404, likely because some token or identifier was missing, which would have been added when the victim clicks a prepared link.
I would argue that any connections to domains that use such homograph character variations should be blocked by corporate intrusion detection systems, as their only use is to fool a human victim.
It’s nice to have a tool to check for such attacks. Automating this to monitor domain creation in real time might help to detect fake domains as they are being set up. The ditto tool already supports that!
Exploring the results in Maltego is very convenient and allows to dig into different aspects quickly, especially because the extracted data can be further enriched using other Transforms.
I’ve tested Safari, Chrome, and Firefox for opening the imposter websites, and only the Chrome browser issued a warning to the user. That makes this technique certainly dangerous and useful to trick people. Registered and reachable imposter domains do seem to exist for every big company I’ve checked, which confirms the IDN homograph attacks are used in the wild.
Follow Maltego on Twitter and LinkedIn and subscribe to Maltego’s email newsletter to stay updated on the latest releases, tutorials, and webinars!
About the Author 🔗︎
Philipp Mieden
Philipp Mieden is a security researcher and software engineer from Germany, currently focusing on network security monitoring and the use of machine learning. He presented his research on classifying malicious behavior in network traffic at several international contests from Kaspersky Lab and won multiple prizes. After finishing his bachelor at the LMU Munich, he moved to Amsterdam to continue his master studies in “Security and Network Engineering” at the UvA. He is sharing many of his projects on Github, but you can also find him on ResearchGate or Twitter. Besides network monitoring, Philipp is also interested in hardware security, industrial control systems and reverse engineering.