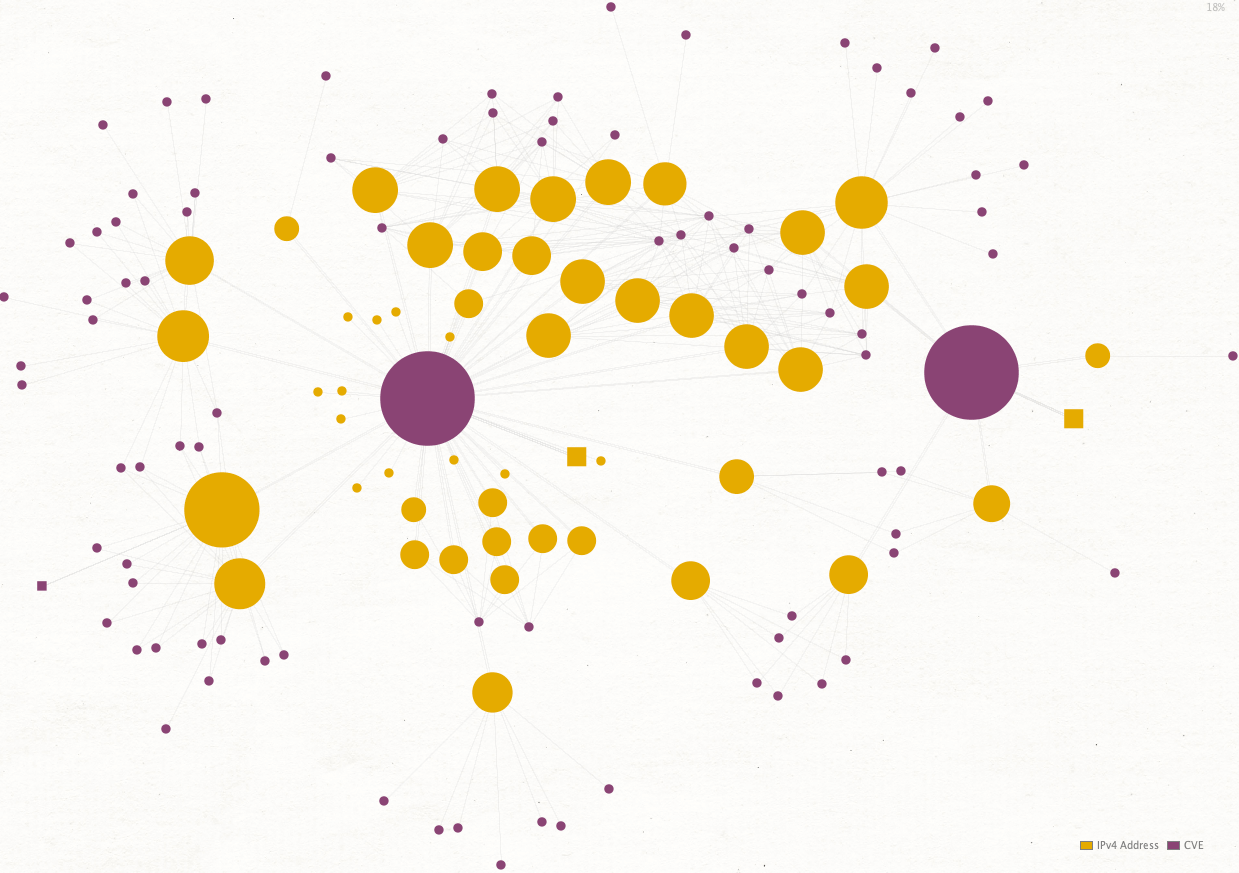We are pleased to announce a major rewrite of one of the most popular Maltego Hub item: The Shodan Transforms!
Shodan is the world’s first search engine for Internet-connected devices. With these Transforms, you can investigate global IoT and infrastructure data from Maltego. In this article, we want to give an overview of the Shodan Transforms in general and demonstrate some of the new features using the example of what could be a real-world investigative scenario.
If you want to jump right into the use cases of Shodan Transforms, please click on the links below:
Major Rewrite of Maltego’s Shodan Transforms 🔗︎
A set of Shodan Transforms was previously provided by Paterva, and those Transforms are being deprecated with this release. In this new release, broken Transforms have been fixed and the functionality has been greatly expanded.
Among other changes, here are some of the key updates and added features:
- Both IPv4 and IPv6 Addresses and subnets are supported.
- CIDR subnet representations were added.
- Vulnerabilities can be explored.
- Raw Shodan searches can be executed.
- The Transforms can be used with all tiers of Shodan API keys.
- IP addresses can be searched using different types of hashes like SSH fingerprints and certificate serial numbers.
- In addition, historical records are now also returned for some Transforms.
IoT Devices Pose New Cyber-Risks for both Individuals and Organizations 🔗︎
A projected 38.6 billion devices will be connected to the Internet by 2025. Attackers are constantly looking for vulnerabilities to compromise organizations, and every new, connected device offers a possible weak point to be exploited.
Shodan scans for these devices—in fact, it scans for and finds all machines that are active and reachable on the Internet, extracts as much data as it can from them, puts it all in a database, and makes this database available for the world to query. With the massive number of devices connected to the internet, it is an effective search engine not only for servers and networks, but for the whole Internet of Things (IoT), from unsecured webcams and routers, to SCADA control systems, traffic lights, and hospital equipment.
The risks opened up by seemingly innocuous IoT devices can be fatal. For example, in 2017, a casino in North America was hacked. About 10 gigabytes worth of data were stolen and transferred to an attacker in Finland. It later turned out that the attackers managed to gain access to the company’s internal network through a recently installed internet-connected aquarium. A web of internet connected-devices, including industrial plant controls, refrigerators, and even fish tanks, are now often the norm and can be found in many (sometimes sensitive) networks.
All this is to say that cyber investigations often need to go beyond what is traditionally considered “infrastructure” to paint a fuller picture of the types of risks a system might be exposed to. This is precisely where Shodan is an invaluable source of insight and information.
Shodan and Common Vulnerability Exposure (CVE) 🔗︎
As a short introduction to our redesigned Shodan Transforms, we will briefly walk through one particularly powerful new feature: Vulnerability identification.
Shodan works by generating random IP addresses and, after querying ports from a Shodan-understandable list of ports, collecting their service banners. Shodan then deduces the service name and version, hostnames, domains, geographic location, organization, operating system, and ISPs, among others, from the banner and IP:port combination. Banners can often expose critical information about authentication, such as the default passwords and usernames, or whether any authentication is needed at all.
The information collected is then used to identify systems that may be susceptible to certain vulnerabilities. Vulnerability is assigned to an IP address by looking at the service name and version, and then looking this up against a database that matches services and their respective versions to CVEs. With our new Transforms, these vulnerable systems can be easily identified and explored on the graph as proper Maltego Entities.
For this scenario, we will make use of the Transforms to find devices with the following vulnerabilities: CVE-2019-19781 and CVE-2019-11510. These vulnerabilities have been discovered to affect devices used to establish Virtual Private Networks (VPNs). Services by Citrix and Pulse Secure are affected by these specific vulnerabilities.
The COVID-19 pandemic has forced organizations worldwide to establish VPN installations to support their newly remote workforces. This makes these vulnerabilities particularly dangerous and their possible abuse widespread. For instance, CVE-2019-11510 has been used to infect company networks with REvil ransomware.
Hunting for Vulnerable Systems and Devices with Shodan and Maltego 🔗︎
To start off, we insert the aforementioned CVE’s as CVE Entities into our Maltego graph and run the To Vulnerable IP Addresses [Shodan] Transform.
If you are following this investigation on your Maltego client, remember to set the slider value to 256 or higher in order to see a broader set of results.
Patches for all three vulnerabilities have been released, so less VPN servers are at risk than there were initially. Only 2% of the servers affected by the CVE-2019-11510 are still vulnerable. However, as these are widely used systems, these 2% still leaves plenty of targets for attackers to choose from.
Selecting the Investigating Target 🔗︎
From here, we have a number of different ways to further analyze the vulnerable IP addresses and choose which ones to investigate further. Let us explore a few of them now.
By Location 🔗︎
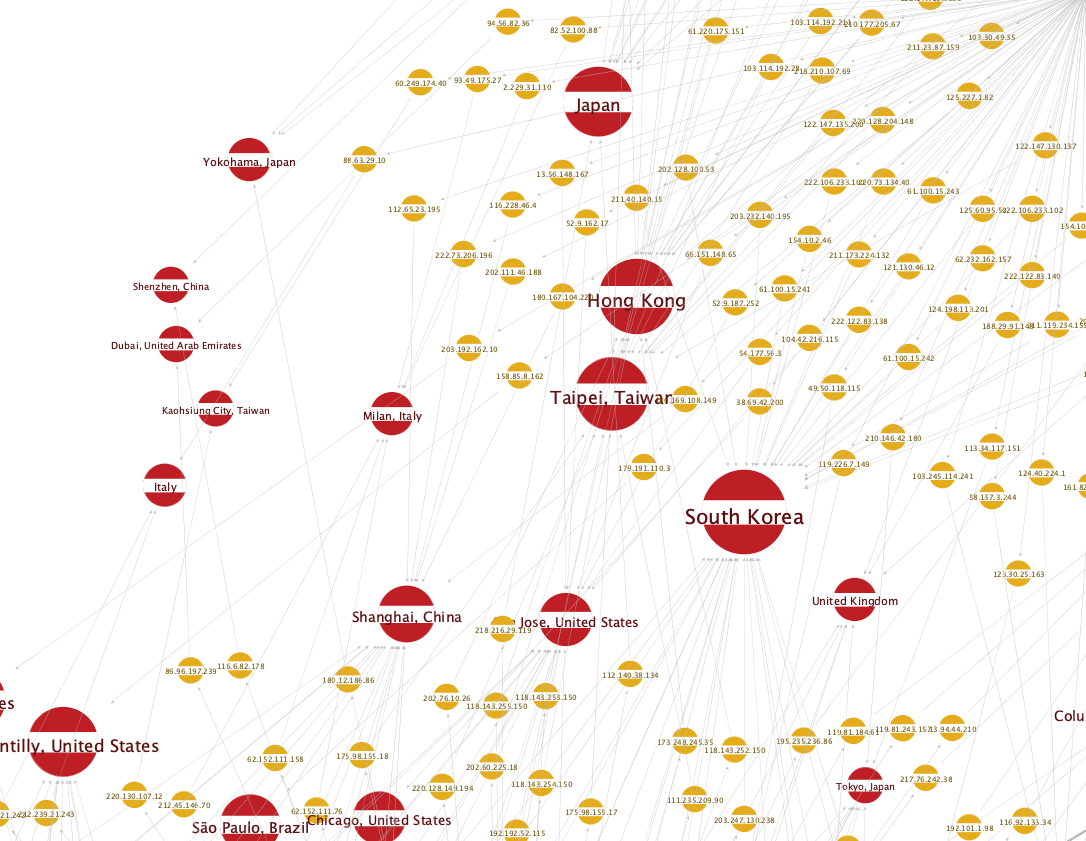
We can use the To Location [Shodan] Transform to filter the vulnerable IP addresses we generated in the previous section by their apparent location. After running this Transform, simply select the Location Entities you are interested in and use “Select Parents” from the top menu bar to select the relevant IP addresses. You can then invert your selection and delete the other Entities in order to isolate them.
We can also use this Transform to simply explore the distribution of affected servers worldwide: Toggling the “Ball Size by Link (Oncoming)” Viewlet, we see that the United States and Japan seem to be where the location for the most of these servers are located.
By Organization 🔗︎
Similarly, we can analyze where these servers are hosted by running the To Organization [Shodan] Transform and analyzing the results in the same way.
We find that a number of the affected servers run/hosted by Softlayer Technologies, Microsoft Azure and Amazon Web Services are mostly affected by these specific vulnerabilities.
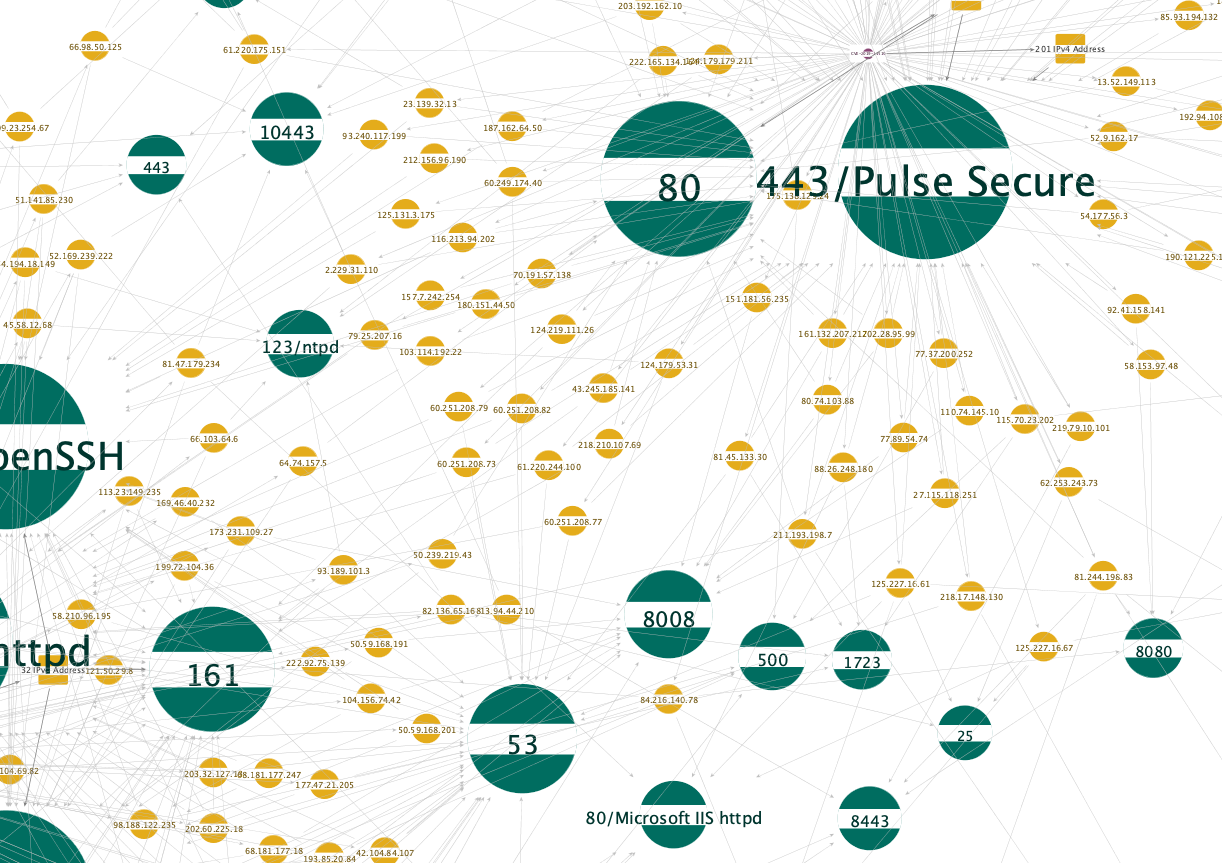
By Service 🔗︎
Most of the identified servers have ports available to connect to an Apache server instance, OpenSSH or Pulse Secure.
By Other Vulnerabilities 🔗︎
We can also analyze the server’s IP addresses found through other vulnerabilities they might be susceptible to using the To Vulnerabilities [Shodan] Transform.
Using the “Ball Size by Links (Outgoing)” Viewlet can help quickly identify devices that have many vulnerabilities. What does it tell us when we find a particularly vulnerable server? For example, one of the machines analyzed had over 100 CVEs. While it could just be an innocuous but poorly maintained machine, we might also find that this particular IP address has too many vulnerabilities, hinting that it might in fact be a honeypot.
After filtering down which devices to target, the Shodan Transforms also are extremely useful for network footprinting, especially when used together with the Maltego Standard Transforms.
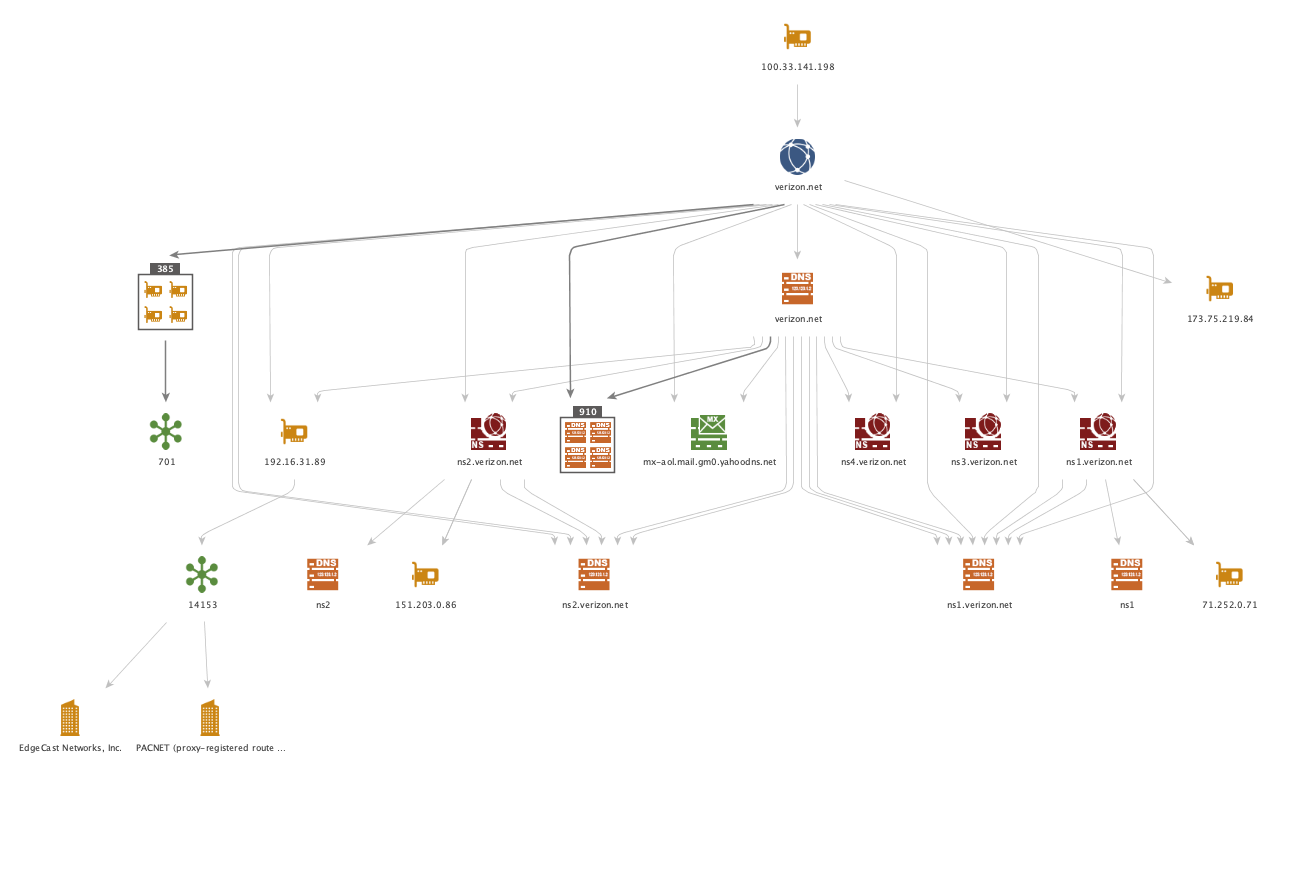
For instance, from a chosen IP address you can use the To Domains [Shodan] Transform to find the Domain connected to the IP address.
From there, we can, find the corresponding DNS servers, mail servers, further IP addresses, websites, netblocks, AS Numbers, and corresponding organizations using the Maltego Standard Transforms.
Continuing the Investigation with Shodan Transforms in Maltego 🔗︎
Besides finding vulnerabilities and conduct a network infrastructure footprint, you can do a lot more with the Shodan Transforms.
For example, the Raw Search [Shodan] and Search Shodan [Shodan] Transforms open up the opportunity to conveniently run all different kinds of native and prepared queries on Shodan from within Maltego. The Search Shodan [Shodan] Transform additionally offers convenient filters to trim down your results from the start.
It is now also possible to search for IP addresses from a Netblock using the Search Netblock [Shodan] Transform. Of course, you can use our Maltego Standard Transforms and many of our Hub partner’s Transforms to further investigate the network infrastructure of any system you analyze using Shodan.
We hope that this demonstration of our Shodan Transforms has piqued your interest to explore and we trust that they will be a valuable tool in your investigations!
We would love to hear about your experience and use cases for these Transforms. Keep visiting our blog, follow our Twitter and LinkedIn pages, and subscribe to our email newsletters for more interesting walkthroughs, announcements and use cases.