
Atlassian has confirmed that a breach at a third-party vendor caused a recent leak of company data and that their network and customer information is secure.
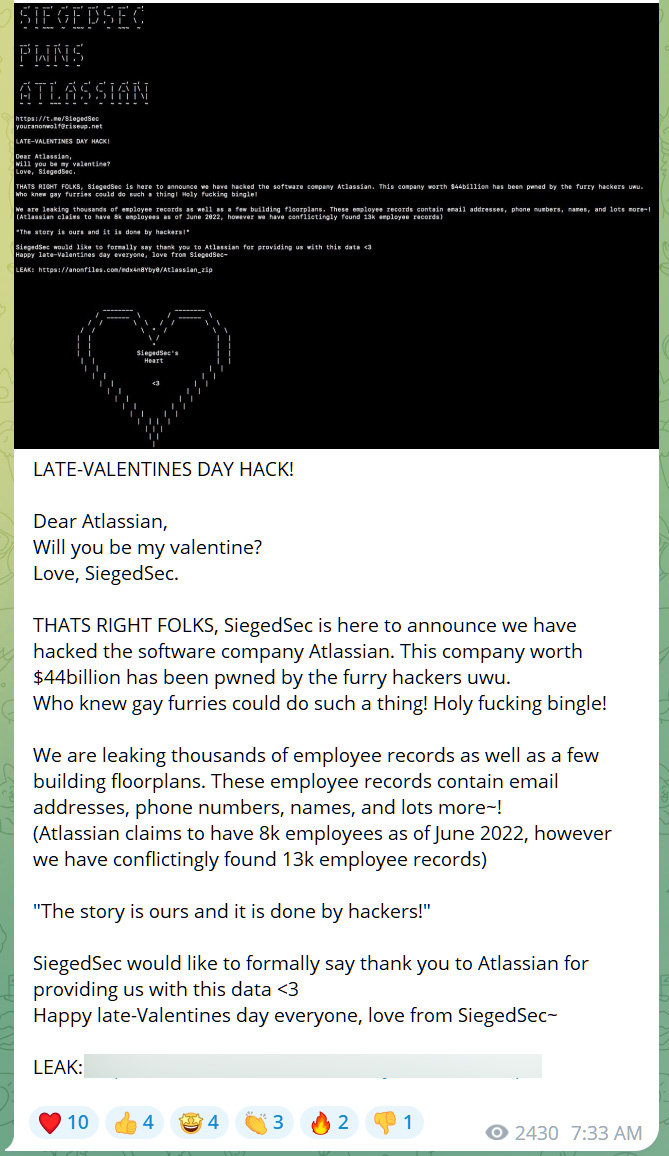
As first reported by Cyberscoop, a hacking group known as SiegedSec leaked data on Telegram yesterday, claiming to be stolen from Atlassian, a collaboration software company based out of Australia.
“We are leaking thousands of employee records as well as a few building floorplans. These employee records contain email addresses, phone numbers, names, and lots more~!,” said the SiegedSec hackers.
Source: BleepingComputer
Soon after the leak, Check Point Software told BleepingComputer that they analyzed the leaked data and that it contained two floor maps for the Sydney and San Francisco offices and a JSON file containing information about employees.
“From the initial analysis, we suspect the group did not hack to Atlassian directly but into a 3rd party provider named https://envoy.com/,” Check Point Software told BleepingComputer.
Today, Atlassian confirmed to BleepingComputer that the data breach was caused by a breach of their third-party vendor Envoy which they use for in-office functions.
“On February 15, 2023 we learned that data from Envoy, a third-party app that Atlassian uses to coordinate in-office resources, was compromised and published. Atlassian product and customer data is not accessible via the Envoy app and therefore not at risk,” Atlassian told BleepingComputer.
“The safety of Atlassians is our priority, and we worked quickly to enhance physical security across our offices globally. We are actively investigating this incident and will continue to provide updates to employees as we learn more.”
BleepingComputer contacted Envoy with further questions about the attack, but a response was not immediately available.



