
2/17/23: Story and title updated to reflect new statements from both companies.
Atlassian suffered a data leak after threat actors used stolen employee credentials to steal data from a third-party vendor. However, the company says its network and customer information are secure.
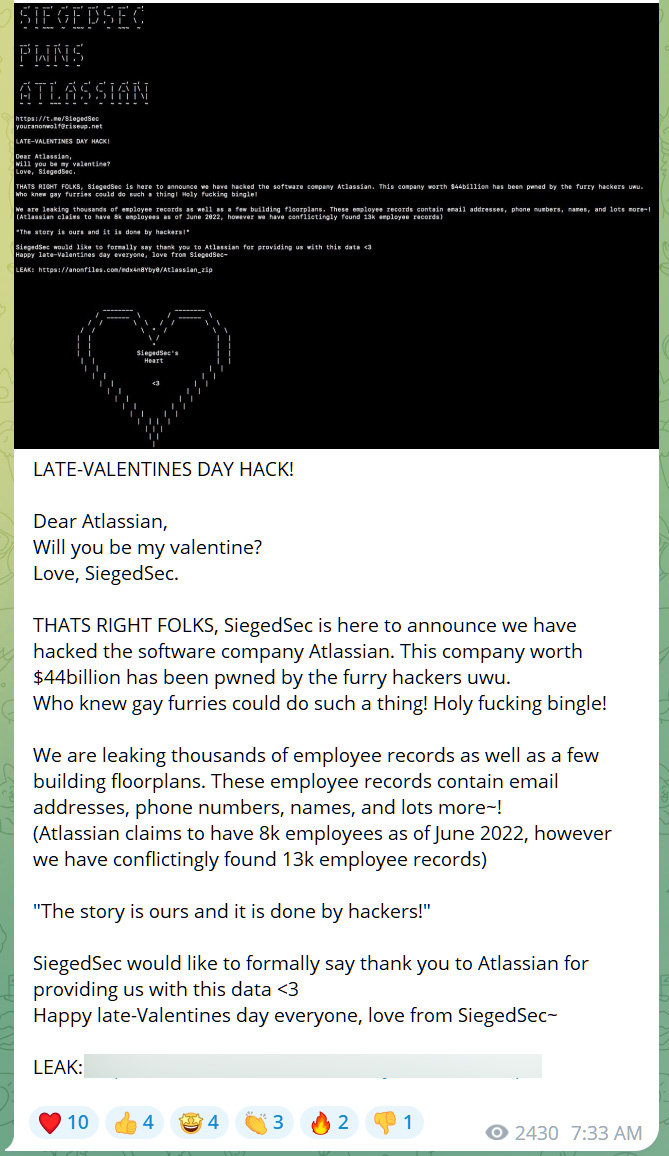
As first reported by Cyberscoop, a hacking group known as SiegedSec leaked data on Telegram yesterday, claiming to be stolen from Atlassian, a collaboration software company based out of Australia.
“We are leaking thousands of employee records as well as a few building floorplans. These employee records contain email addresses, phone numbers, names, and lots more~!,” said the SiegedSec hackers.
Source: BleepingComputer
Soon after the leak, Check Point Software told BleepingComputer that they analyzed the leaked data and that it contained two floor maps for the Sydney and San Francisco offices and a JSON file containing information about employees.
“From the initial analysis, we suspect the group did not hack to Atlassian directly but into a 3rd party provider named https://envoy.com/,” Check Point Software told BleepingComputer.
Atlassian confirmed to BleepingComputer that the compromised data was from third-party vendor Envoy which they use for in-office functions.
“On February 15, 2023 we learned that data from Envoy, a third-party app that Atlassian uses to coordinate in-office resources, was compromised and published. Atlassian product and customer data is not accessible via the Envoy app and therefore not at risk,” Atlassian told BleepingComputer.
“The safety of Atlassians is our priority, and we worked quickly to enhance physical security across our offices globally. We are actively investigating this incident and will continue to provide updates to employees as we learn more.”
However, Envoy says that they are not aware of a breach on their side and believes that an Atlassian employee’s credentials were stolen, allowing the threat actor access to the data inside the Envoy app.
“We’re investigating this right now and are not aware of any compromise to our systems. Our initial research shows that a hacker gained access to an Atlassian employee’s valid credentials to pivot and access the Atlassian employee directory and office floor plans held within Envoy’s app,” Envoy told BleepingComputer.
“Envoy, like Atlassian, takes the security and privacy of our customers’ data incredibly seriously and has stringent measures in place to protect it.”
Update 2/17/23:
In a new statement from Envoy, the company states that its systems were not breached, but rather an Atlassian employee’s credentials were stolen, allowing the threat actors to gain access to data stored in the Envoy app.
“Both Envoy and Atlassian security teams have been collaborating to identify the source of the data compromise. We found evidence in the logs of requests that confirms the hackers obtained valid user credentials from an Atlassian employee account and used that access to download the affected data from Envoy’s app,” Envoy told BleepingComputer.
“We can confirm Envoy’s systems were not compromised or breached and no other customer’s data was accessed.”
Atlassian has told BleepingComputer that an employee’s credentials were mistakenly published to a public repository, allowing the threat actors to use them to steal the company’s data within the Envoy app.
“Our security intelligence team worked closely with Envoy over the past 48 hours to explore all possible modes of entry. Late yesterday evening U.S. time, security intelligence released their findings and we could say with certainty how our Envoy data had been compromised,” an Atlassian spokesperson told BleepingComputer in an updated statement.
“We learned the hacking group compromised Atlassian data from the Envoy app using an Atlassian employee’s credentials that had been mistakenly posted in a public repository by the employee. As such, the hacking group had access to data visible via the employee account which included the published office floor plans and public Envoy profiles of other Atlassian employees and contractors.”
“The compromised employee’s account was promptly disabled early in the investigation which was proven effective in eliminating any further threat to Atlassian’s Envoy data. Atlassian product and customer data is not accessible via the Envoy app and therefore not at risk.”
Update 2/16/23 4:35 PM ET: Added Envoy statement
Update 2/17/23: 9:45 PM ET: Updated story to reflect new statements from Envoy and Atlassian.
Update 2/17/23: 1:45 PM ET: Added additional statement from Atlassian



