
The WordPress online course plugin ‘LearnPress’ was vulnerable to multiple critical-severity flaws, including pre-auth SQL injection and local file inclusion.
LearnPress is a learning management system (LMS) plugin that allows WordPress websites to easily create and sell online courses, lessons, and quizzes, providing visitors with a friendly interface while requiring no coding knowledge from the website developer.
The vulnerabilities in the plugin, used in over 100,000 active sites, were discovered by PatchStack between November 30 and December 2, 2022, and reported to the software vendor.
The issues were fixed on December 20, 2022, with the release of LearnPress version 4.2.0. However, according to WordPress.org stats, only about 25% have applied the update.
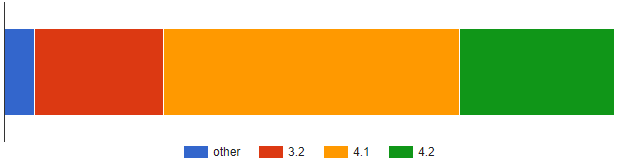
This means that roughly 75,000 websites could be using a vulnerable version of LearnPress, exposing themselves to severe security flaws, the exploitation of which can have serious repercussions.
Vulnerability details
The first vulnerability discovered by PatchStack is CVE-2022-47615, an unauthenticated local file inclusion (LFI) flaw that allows attackers to display the contents of local files stored on the web server.
This could expose credentials, authorization tokens, and API keys, leading to further compromise.
The vulnerability is found in a piece of code that handles API requests for the website, located in the “list_courses” function, which does not validate certain variables ($template_pagination_path, $template_path, and $template_path_item) properly.
An attacker could potentially exploit CVE-2022-47615 by sending a specially crafted API request and using malicious values for the three variables.
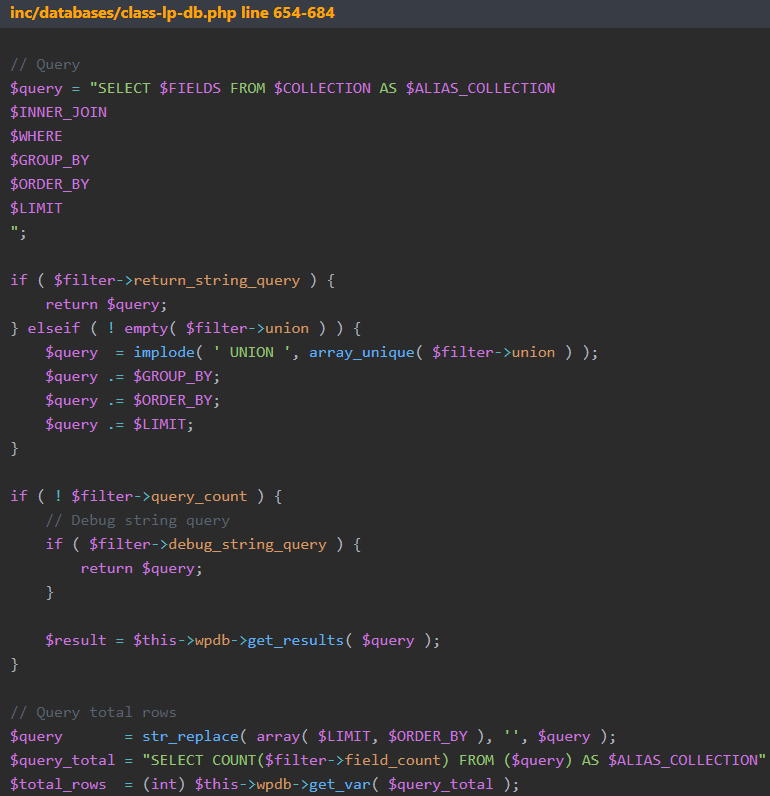
The second critical flaw is CVE-2022-45808, an unauthenticated SQL injection potentially leading to sensitive information disclosure, data modification, and arbitrary code execution.
This vulnerability lies in a function that handles SQL queries for the website, which does not correctly sanitize and validate the “$filter” variable in the query parameters, allowing an attacker to insert malicious code in it.
The third flaw impacting older LearnPress versions is CVE-2022-45820, an authenticated SQL injection flaw in two shortcodes of the plugin (“learn_press_recent_courses” and “learn_press_featured_courses”) failing to properly validate and sanitize the input of the “$args” variable.
PatchStack provided a proof-of-concept exploit showing how a ‘Contributor’ user could trigger the SQL injection using a specially crafted shortcode on a drafted post.
This vulnerability needs to be performed by a user with the ability to edit or create a new blog post, limiting the risk of the flaw.
The vendor fixed the above issues by introducing an allowlist and sanitization of the vulnerable variables or removing the ability to include templates in user input.
Website owners relying on LearnPress are advised to either upgrade to version 4.2.0 or disable the plugin until they can apply the available security update.



