Analysis of ransomware trends in 2022 shows that business was booming last year for extortionary cybercriminals, with the highest volume of ransomware attacks lobbed by sophisticated criminals that organize into groups that utilize very consistent tactics, techniques, and procedures (TTPs) amongst themselves, even if these organizations “retire” and then come back, rebranded.
A Jan. 26 report from the Guidepoint Research and Intelligence Team (GRIT) showed that while at least one new ransomware group emerged every month last year, the majority of attacks were perpetrated by a relatively small group of entrenched players.
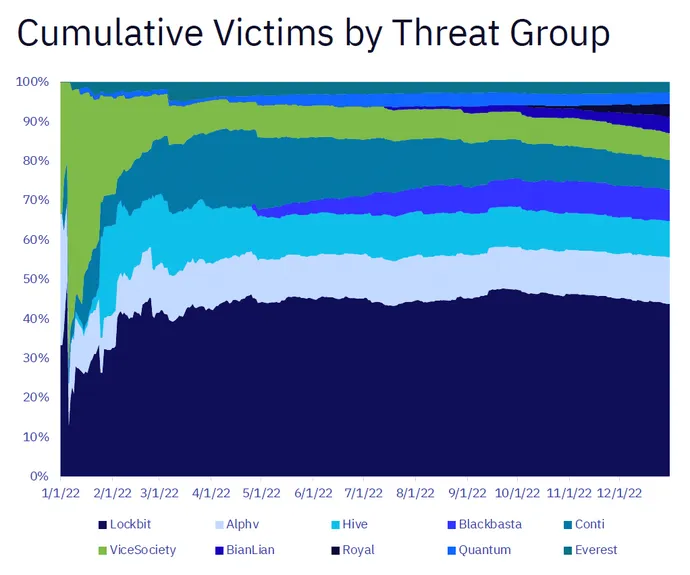
The “GRIT 2022 Ransomware Report” examined data and circumstances from 2,507 publicly posted ransomware victims across 40 industry verticals that were carried out by 54 active threat groups.
“The thing that we really wanted to emphasize was that ransomware is not going anywhere,” says Drew Schmitt, GRIT lead analyst and an experienced ransomware negotiator for GuidePoint Security. “It’s very present. A lot of people seem to think that ransomware is potentially declining, because of things like Bitcoin payments are becoming less valuable. But ransomware is still happening at crazy rates.”
As a negotiator, Schmitt works with actively attacked companies to act on their behalf and interface with the extortionist. There are two goals: to either gain enough information and time to help their security operations centers (SOCs) recover, or to negotiate a lower payment.
Using his inside knowledge about how attackers operate, and the data freely available about victimology last year, he and his team were able to put together a number of insights for the report. Dark Reading caught up with Schmitt to not only dig into details the report, but also to glean observations from his ongoing work as a negotiator. He provided seven key points that defenders should keep in mind as they prepare for more ransomware campaigns in 2023.
1. There’s a Definite Taxonomy to Ransomware Gangs
A big part of the analysis revolved around the development of a ransomware taxonomy for categorizing ransomware groups, which the team organized into four buckets: full-time, rebrands, splinter, and ephemeral.
The majority of attacks came from what the taxonomy dubbed full-time groups, which have been active for nine or more months and publicly claim 10 or more victims.
“These are the Lockbits of the world, and they’re the ones that are doing very consistent operations [and] can maintain a very high tempo,” Schmitt says. “They are very consistent in behaviors and have a lot of really robust infrastructure. Those are the ones that have been operating for a very long period of time, and they’re doing it consistently.”
As the report pointed out, Lockbit alone accounted for 33% of attacks last year.
Then there are the rebrand groups, which have been active for less than nine months but claim nearly the same number of victims as full-time groups, and with some examination of TTPs usually have some correlation with a retired group.
“Really the only difference between the rebrand and the fulltime is the duration of operation,” Schmitt says. “Groups like Royal also fit into this type of category where they just have very robust operations and they’re able to operate at a high tempo.”
Meantime, “splinter” groups are those that have some TTP overlap with known groups, but are less consistent in their behaviors.
“The splinter groups are an offshoot from either a rebrand or a full-time, where it’s maybe somebody going off and doing their own thing,” he says. “They haven’t been around for very long. Their identity is not solidified at this point in time, and they’re really just trying to find themselves and how they’re going to operate.”
Finally rounding things out are “ephemeral” groups that have been active for less than two months, which have varied but low victim rates. Sometimes these groups come and go, while other times they end up developing into more mature groups.
2. Rapid Rebranding of Ransomware Groups Makes Threat Intelligence Key
The classification into those four taxonomy groups looks cleaner in an annual report than it does on the ground when a SOC starts lighting up.
“When you start dealing with these types of groups that are popping up and going away very quickly, or they’re rebranding, they’re developing new names, it does make it very much more difficult for the blue teamers or the defenders to keep up with these types of trends,” says Schmitt, who explains that keeping tabs on rebranding and splintering of groups is where threat intelligence should come into play.
“We really like to focus on emphasizing communication when it comes to threat intelligence — whether it’s threat intelligence talking with the SOC or the incident response team, or even vulnerability management,” he says. “Getting an idea of what these trends look like, what the threat actors are focusing on, how much they pop up and go away, all of that is very valuable for the defenders to know.”
3. RaaS Groups Are a Wild Card in Negotiations
Even though the underlying TTPs of fulltime groups makes a lot of ransomware detection and response a little easier, there are still some big variables out there. For example, as many groups have employed the ransomware-as-a-service (RaaS) model, they employ a lot more affiliates, which means negotiators are always dealing with different people.
“In the early days of ransomware, when you started negotiations, there was a good chance you were dealing with the same person if you were dealing with the same ransomware,” Schmitt says. “But in today’s ecosystem, there are just so many different groups, and so many different affiliates that are participating as part of these groups, that a lot of times you’re almost starting from scratch.”
4. Ransom Demands Are Climbing Sky High
One of the anecdotal observations Schmitt made was the fact that he’s seen a lot of very high initial ransom demands from ransomware operators lately.
“We’ve seen $15 million, we’ve seen $13 million, we had $12.5 million. There’s a lot of very high initial ransom demands that have been happening, which is a little bit surprising,” he says. “And a lot of times we do successfully negotiate significantly lower ransoms. So starting at $15 million and getting down to $500,000 is not uncommon. But at the same time there are just certain threat actors that are like, ‘You know what? This is my price and I don’t care what you say, I’m not going to negotiate.'”
5. Improved Backup Strategies Are Making a Difference in Preparation
The ratio of clients he sees who can successfully recover without caving to the extortion demands versus those that need to pay a ransom is coming close to a 1:1 parity, Schmitt says.
“In the early days it was like, ‘Well crap, we got encrypted. We can’t recover unless we pay this ransom,'” he notes. “As time has gone on, having really effective backup strategies has been huge for being able to recover; there are a lot of organizations that get hit with ransomware and they’re able to recover simply because they have a really solid backup strategy in place.”
6. Double Extortion Is the Norm
However, there are still plenty of organizations that are still behind the curve, he says, which keep ransomware more profitable than ever. Additionally, the bad guys are also adjusting through doubleextortion, not only encrypting files, but stealing and threatening to publicly leak sensitive information as well. All of the groups tracked in the report utilize double extortion.
“It’s a little bit unclear whether that’s just because people are getting better at securitynor the groups are really realizing that maybe it’s not worth the effort to deploy the ransomware if the client already has a backup strategy in place that’s going to allow them to recover,” he says. “So, they’ve been focusing on that data exfiltration because I think they know that that’s the best chance that they actually have to make money off of an attack.”
7. There’s No Honor Among Thieves, but There’s Business Sense
Finally, the big question in dealing with criminal extortionists is whether the bad guys are even going to keep their word once the money drops in their account. As a negotiator, Schmitt says that, for the most part, they typically do so.
“Obviously, there’s no honor among thieves, but they do believe in their reputation,” he says. “There are edge cases where something bad happens, but most commonly the bigger groups are going to make sure they don’t post your data and they’re going to provide you the decryptor. It’s not going to be some malware backdoor decryptor that’s going to do more damage. They’re very focused on their reputation, and their business model simply just doesn’t work if you pay them and then they still leak your data or they don’t give you what they’re supposed to.”


